Introduction
Let us start with defining the following important terms; Backup, Information Security, and Information Assurance
Backup
In Information Technology, a backup is defined as a process of copying and archiving computer data that can be used to restore the original data after the occurrence of a data loss event Backups have two distinct purposes. The primary purpose is to recover data after its loss, be it by data deletion or corruption.
The secondary purpose of backups is, from an earlier time to revive lost data. According to a user-defined data retention policy, these data are typically configured within a backup application for how long copies of data are required.
Backups are usually used to ensure the availability of information.
Information Security
Also referred to as InfoSec, is the practice of unauthorized access prevention, usage, disclosure, disruption, modification, inspection, recording or destruction of information. This is a general term that can be used either for electronic or physical data.
The aim of InfoSec is to ensure that the Confidentiality, Integrity, and Availability (CIA) of the information are not violated, e.g. ensuring that data is not lost when critical issues arise. These issues consist of physical theft, natural disasters, or even computer/server malfunction. A common method of protecting information is to have an off-site backup of the data in cases when one of the mentioned issues arise.
Information Assurance (IA)
Is the practice of assuring information and managing risks related to the use, processing, storage, and transmission of data. IA includes protection of the integrity, availability, authenticity, non-repudiation, and confidentiality of user data.
In addition, IA is the process of getting the right information to the right people at the right time.
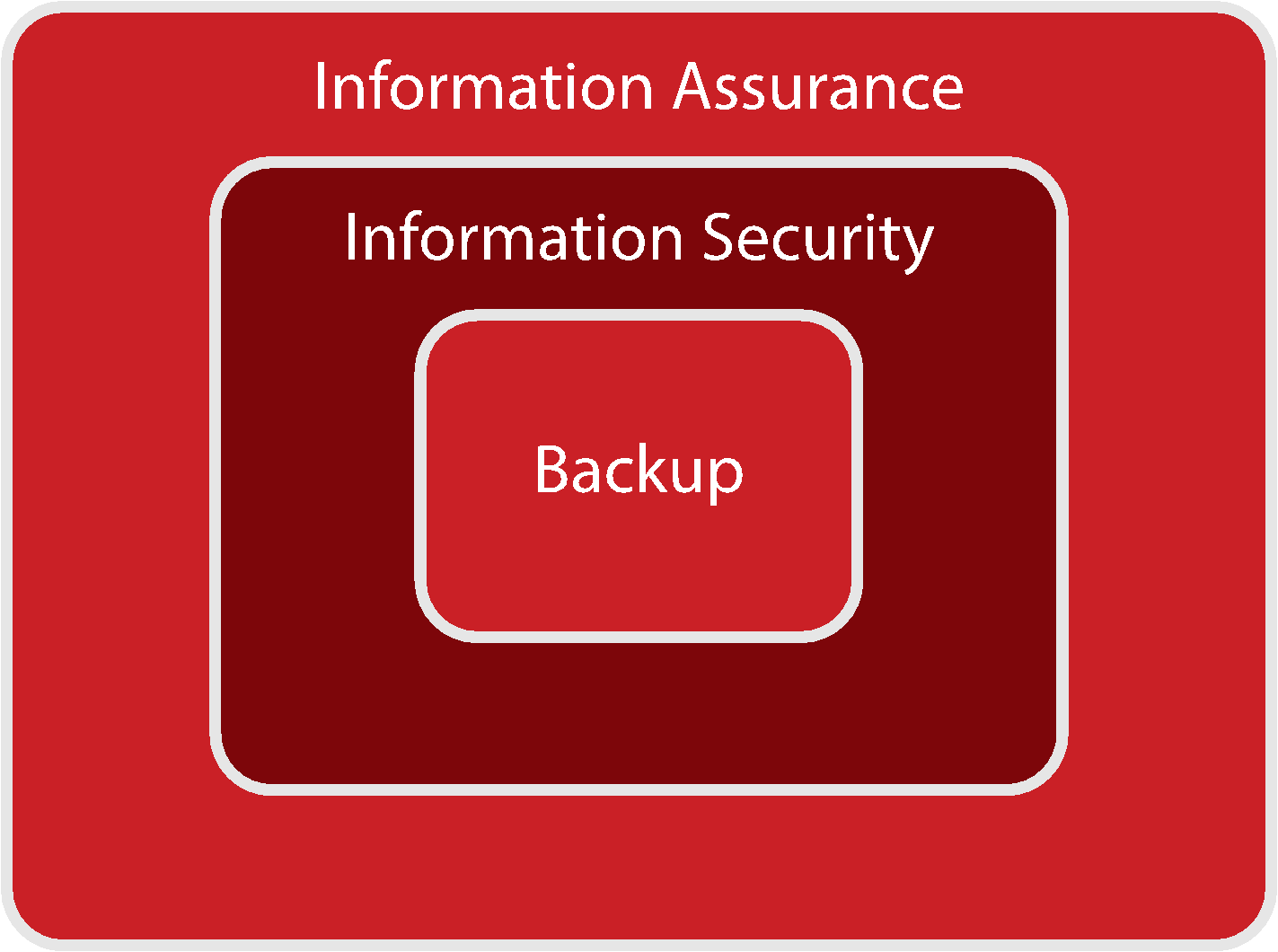
Comparing between Backup, InfoSec and Information Assurance (IA)
Information Assurance (IA) adds business benefit through the use of Information Risk Management, Trust Management, Resilience, appropriate Architecture, system safety, and security, which increases the utility of information to authorized users and reduces the utility of information to those unauthorized.
It is strongly related to the field of InfoSec, and also with Business Continuity. IA relates more to the business level and strategic risk management of information systems, rather than to the creation and application of security controls.
Therefore, in addition to defending against malicious hackers and code (e.g., viruses), IA practitioners take into account organizational issues such as privacy, regulatory, and standards compliance, auditing, business continuity, and disaster recovery as they relate to information systems.
Further, while InfoSec draws primarily from computer science, IA is an interdisciplinary field requiring expertise in business, accounting, user experience, criminology, security engineering, systems engineering, fraud examination, management, and forensic science, in addition to computer science.
Therefore, IA is best thought of as a superset of InfoSec (i.e. umbrella term), and as the business outcome of Information Risk Management.
Also, we may think of backup as a subset of InfoSec and as an outcome of effective InfoSec program.
The relationship between IA, InfoSec, and Backup is depicted in the following graph:
Why do enterprises make the fatal mistake of paying more for backup than for security?
Though backups represent a simple form of disaster recovery and should be part of any disaster recovery plan; however, backups by themselves should not be considered a complete disaster recovery plan.
Reconstituting a computer system or other complex configuration such as computer cluster, active directory server, or database server, or database server is not merely possible to be conducted from every backup system. For this reason, even with implementing the most powerful and expensive backup technology/applications enterprise will never gain the necessary IA for its business.
InfoSec is important to protect the integrity, availability, authenticity, non-repudiation, and confidentiality of user/business data, to have effective InfoSec there is a need to establish an InfoSec Program, certainly, the expected benefits from establishing such a Program will outweigh its expenses.
Conclusion
Kotler defines enterprise governance as the following:
“Enterprise Governance is a set of responsibilities and practices exercised by the board and executive management with the goal of providing strategic direction, ensuring that objectives are achieved, ascertaining that risks are managed appropriately and verifying that the enterprise’s resources are used responsibly”.
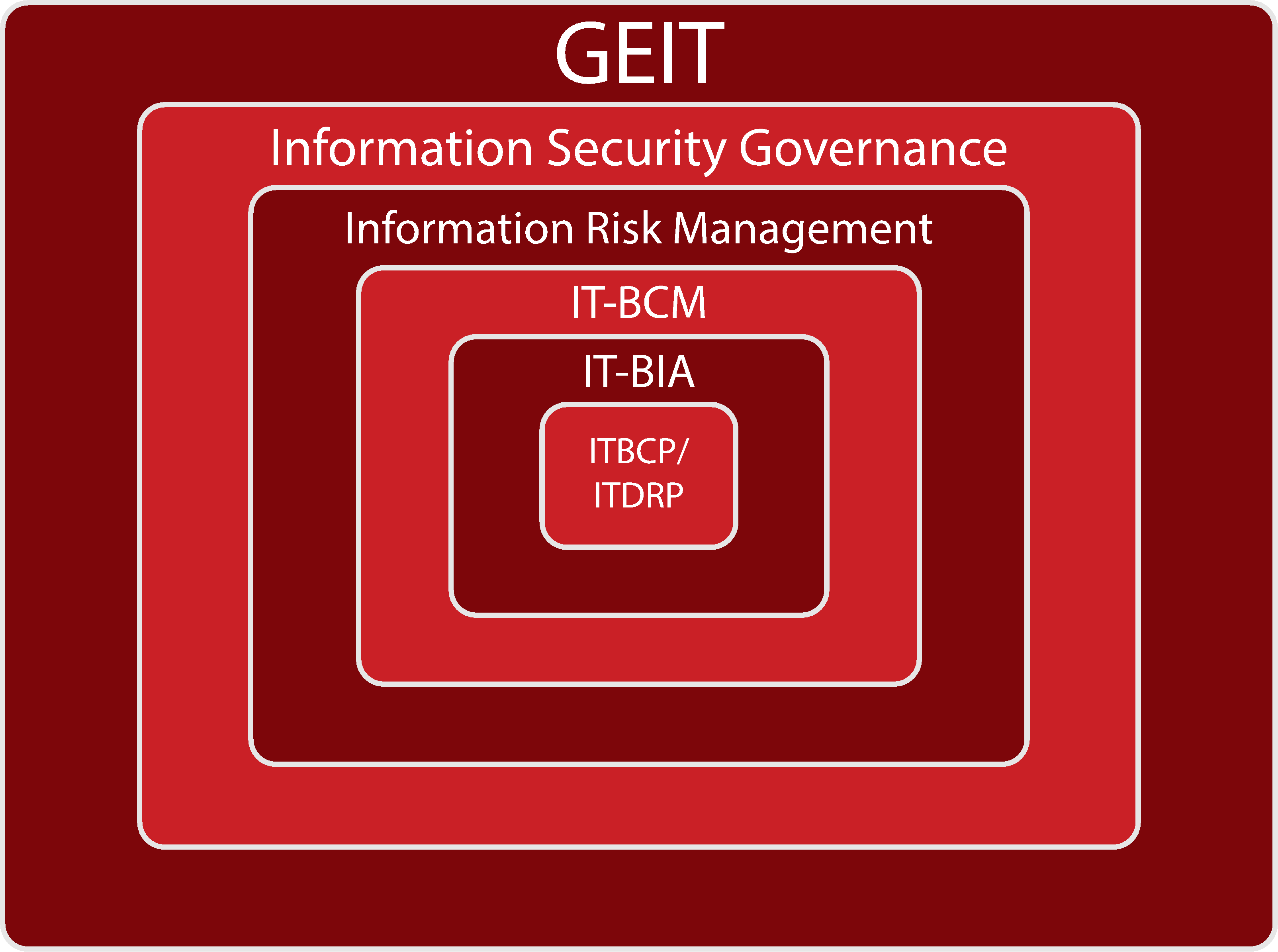
A good practice for any enterprise to protect its valuable information assets is to start by understanding practices such as the Corporate Governance, the Enterprise Risk Management (ERM), the Business Continuity Management (BCM) and the governance of enterprise IT (GEIT) and the InfoSec Governance as a subset of Corporate Governance. The Information Risk Management (IRM) directs the IT Business Continuity Management (IT-BCM) that should be based on a solid IT Business Impact Analysis (IT-BIA) to develop the necessary IT Business Continuity plans (ITBCP) and IT Disaster Recovery plans (ITDRP). Part of the later plans will also be the backup plan.
The previous relationships are delineated in the following graph:
To better understand the frameworks mentioned in this article, the reader is advised to refer to the following ISO standards’ certifications:
ISO/IEC 38500 (ISO/IEC IT Corporate Governance Manager)
This standard provides guiding principles for members of governing bodies of organizations on the effective and efficient use of information technology in their company.
ISO 31000 (ISO 31000 Risk Manager)
Risk management – Principles and guidelines provide the principles, the framework and the process for managing risk.
ISO/IEC 27005 (ISO/IEC 27005 Risk Manager)
Provides guidelines for InfoSec risk management.
ISO 22301 (ISO 22301 Implementer/Auditor)
Specifies requirements to plan, implement, establish, operate, monitor, maintain, review, and continually improve a documented management system to protect against, reduce the likelihood of occurrence, prepare for, respond to, and recover from disruptive incidents when they arise.
ISO/IEC 24762 (ISO/IEC Disaster Recovery Manager)
Provides guidelines on the provision of information and communications technology disaster recovery (ICT DR) as a very important part of business continuity management, applicable to both “in-house” and “outsourced” ICT DR service providers of physical facilities and services.
PECB
The value of information security structures on one’s business increases the competence of promising personal data security. Further, mastering risk management elements for information security through ISO/IEC 27005:2011, complements competence through the interpretation of requirements of ISO/IEC 27001 on information security risk management. PECB offers training courses on ISO/IEC 27005 to be attended by Risk Managers, members of information security teams, IT consultants, etcetera.