Introduction
Digital transformation has proliferated across many business sectors. Corporations are harnessing the underlying technologies to automate processes, mine data, pivot to new markets, reduce costs, or tailor services to client preferences. For example, the hotel industry is digitally transforming the business model to improve energy efficiency, characterize customer trends, and improve their guests’ experience. Economies of scale and technological advances in artificial intelligence, Internet Of Things (IoT), cloud computing, 5G infrastructure, and processing power have catalyzed strategy adoption. These technological advances have decentralized computation, increased data traffic density, and reduced non-recurring costs. Analysts project digital transformation spending to exceed $1.2 trillion by 2022. According to a report, Ericsson, the Swedish telecommunications manufacturer, projects 3.5 billion wireless sensors transmitting data. Additionally, KPMG reports that digital transformation will drive the greatest paradigm shift in the first half of the decade.
Digital transformation also increases cyber-risk. Digitally transforming businesses do not understand the full scope needed to protect their enterprise network and the assets on these networks. Hackers, ranging from lone wolves to criminal organizations, penetrate the network for financial gain, geo-political ends, or credibility. Potential consequences include financial loss, compromised credibility, and injury or death. Recent examples include the Colonial Pipeline, ethical hackers who compromised a Jeep Cherokee, and the cyberattack on JBS, a large meat supplier in the United States. Recent news headlines highlight increased hacking activity across many sectors. In addition, surveys and independent security audits have uncovered underlying trends across many sectors that increase IoT cyber risk. Design strategies, management policies, and awareness compromise the security posture for digitally evolving businesses. This article will discuss these trends and introduce strategies to improve the security posture from the sensor endpoints to the central data center. When implemented, these strategies require expanded headcount, training, iterative evaluation, additional system complexity, and increased project costs.

System lifecycle management
Vulnerabilities form throughout the system lifecycle and can materialize as early as the system design. Digitally transforming businesses typically lack the system design expertise and outsource the project to engineering firms. One common mistake is omitting a cyber professional’s design assessment of its cyber readiness. They can also advise on asset management, event management, and cyber awareness training. Unfortunately, cyber specialists are in high demand and adding them to the design team increases project cost significantly. Finally, policies to assess cyber readiness continuously through audits are not implemented to improve the security posture.
Implementing cybersecurity best practices into a system lifecycle is shown in Figure 1. A system lifecycle is a standard framework that describes the event sequence from the initial strategy through system obsolescence. Key cybersecurity contributions are highlighted through the system lifecycle. During the design phase, security best practices and tools, which are discussed later in this article, are integrated into the system design. The tools consist of both hardware and software platforms that harden the systems security posture. After the prototype has been implemented and is ready for a pilot phase, cyber tools scan the infrastructure for both vulnerabilities and best security practice compliance. The security gaps must be remedied before going live.
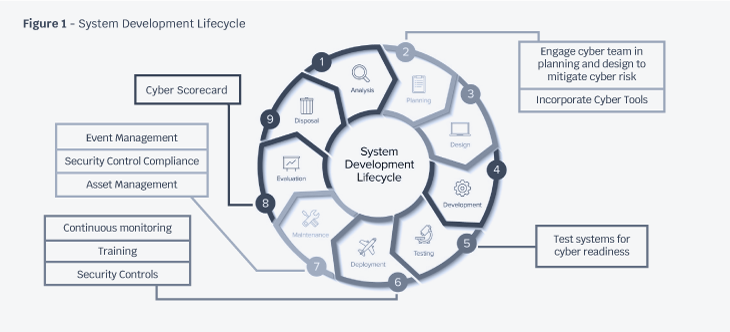
During system deployment, monitoring tools must also be implemented before the services go live. Tools are used for event detection and data analysis. Integrated messaging platforms quickly alert users of a suspicious activity or component failure. Many enterprise platforms integrate these capabilities as basic features. In addition, dashboards ingesting real-time data and translating it to user-friendly graphs and indicators can be rapidly designed and integrated into the system. These dashboards help administrators quickly assess event criticality and determine the course of action.
Security controls are implemented to protect critical assets. Controls can include policies or physical objects such as key cards to limit access. Common controls, discussed later in this article, include Zero-Trust and Public Key Infrastructure (PKI). Implementing security controls adds another management layer to daily operations and maintenance. Passwords are also a security control and policies can be implemented to mandate complexity and periodic changes.
When digitally transforming, businesses must train staff tasked to manage the new capabilities. Key focus areas are event management, operations and maintenance (O&M), security best practices, and cyber awareness. Event management utilizes a framework to assess incidents and implement corrective actions. Key roles and responsibilities during incidents are identified, and reporting strategies based on incident severity are planned. Event management also designates a crisis response team and a crisis response plan for service disruption. Playbooks and periodic event walkthroughs reinforce the plan and address any critical gaps when risk is low. O&M activity includes software patch management, system repair, diagnostic assessment, and account maintenance. Organizations plan periodic maintenance around software release and patch schedules, which can be manually applied or automatically updated.
Security best practices define the industry standards and processes that organizations follow. Practices include optimized configuration, manufacturer recommendations, and design techniques.
Finally, all employees must improve cyber awareness, which has been identified as a critical vulnerability. Cyber awareness involves everyone who touches a computing asset, including the receptionist at the front desk. Recommended cyber awareness strategies include period refresher training and information sharing between intercorporate organizations. Businesses can also incentivize cyber awareness through rewards and recognition.
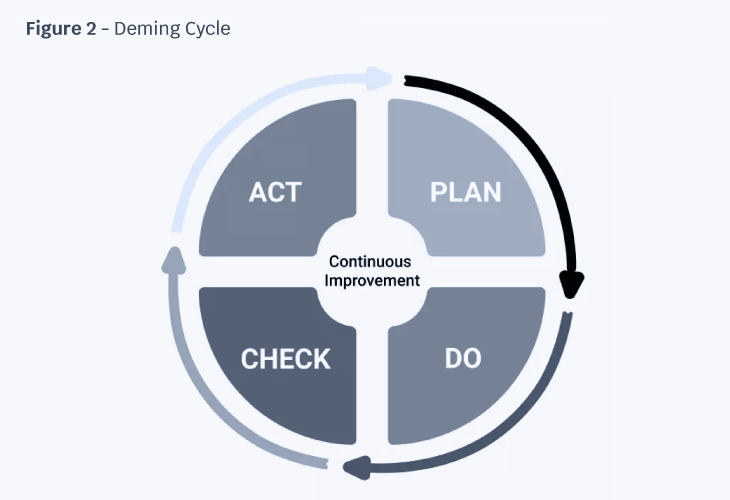
Throughout live operation, periodic reevaluation and audits should be implemented to identify developing vulnerabilities. Remediation plans are then evaluated and implemented to mitigate risk. The Deming Cycle (Plan-Do- Check-Act), shown in Figure 2, is a management framework used to assess cyber readiness continuously and implement corrective action. During the Plan stage, multiple strategies are evaluated for cost, complexity, and potential efficacy. The success criteria is also planned during this phase as is the fallback plan in the event the strategy is not successfully implemented. The best strategy is selected and the implementation team plans the roll-out. The implementation team then integrates the strategy during the Do phase. During the Check phase, the implementation is evaluated against its key success factors and lessons learned are also discussed. Finally, in the Act phase, the next improvement is selected based on the success and lessons learned. The Deming Cycle is repeated as the iteration is planned, implemented, and evaluated.
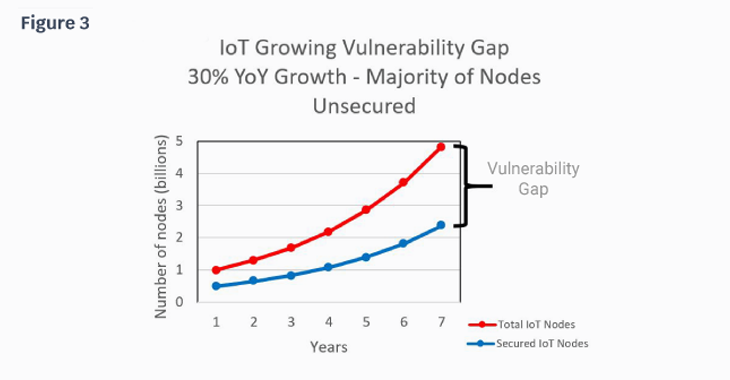
A scorecard can continuously assess the training, response, and posture. A scorecard should be simple and easy to read, however, it needs to state key deficiencies and critical trends explicitly. Figure 4 shows an example of a simple scorecard. The individual scores for the key success factors are tabulated on the right hand side of the scorecard. This score decomposition identifies key areas to improve to harden the security posture. The top center shows the overall score and the score weighting to stress which factors have greater significance in the evaluation. The graph in the bottom center shows the tabulated score over a pre-determined time interval. The left hand side is an evaluation of how the company’s cyber posture compares to its competitors’. This scorecard is just an example, but the key data points are the overall score, the score breakdown to the individual metrics such as patch management, the score weighting, and the trending score over the past year. Other data points not presented in this score card are key security events such as a data breach or bullets describing deficiencies.
Internet of things (IoT) networks
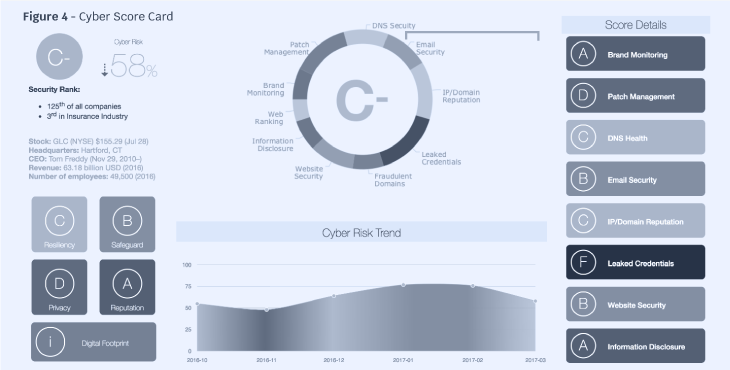
IoT networks form the core infrastructure for many digital transformations. Innovation has decreased sensor costs, improved decentralized computation, and enhanced scalability. However, IoT networks pose significant security risks. A recent survey of executives reports that organizations do not account for all devices on the enterprise network. This same survey states roughly 33% of these devices are properly managed. Figure 3 shows an estimated vulnerability gap based on analysts’ IoT projections and device management estimates. As more firms pivot to IoT to digitally transform their business models, the cyber exposure increases exponentially. The vulnerability gap can be reduced by implementing the management lifecycle previously discussed and the cyber tools that will be discussed in the next section. A notional vulnerability gap based on these projects is shown in Figure 3.
Hackers view IoT sensors as a bridge into the enterprise network. Many sensors are placed outside the security perimeter and communicate wirelessly to the enterprise. Sensors also forward data with other wireless sensors that do not have enough transmit power to reach the network’s wireless access points. Sensors are continuously reconfiguring as wireless channels change with the weather, obstructions, or defective sensors. Sensor manufacturers are not obligated to design security features or to update firmware to correct bugs. Passive sensors that only transmit data are especially vulnerable.
IoT vulnerabilities differ based on manufacturer design specifications, sensor placement outside the secure network perimeter, and software patches and updates to mitigate bugs. Sensors are typically commodities and manufacturers are not motivated to design security features into the sensors. IoT network designers must implement strategies and cyber tools to mitigate the security gap. Since most sensors are wirelessly connected and lack enterprise security tools, they are susceptible to wireless intrusion by hackers. Firmware updates in many cases are not continuously updated and critical vulnerabilities are not remedied by the manufacturer. Transmitting firmware updates to geographically diverse and sensor types is difficult because the software updates potentially saturate the wireless channels and require multiple hops from sensor to sensor. In addition, sensors do not operate using the same firmware, which adds asset management complexity. Finally, referring to the vulnerability gap above, the unaccounted sensors potentially never have their password changed, never receive software updates, and are never properly removed from the network when they become obsolete.
Cybersecurity tools and strategies
An Intrusion Detection System (IDS) actively monitors the wireless network access and reports anomalous behavior. IDS can also be configured to alert administrators when black-listed devices try to communicate with the network. IDS can also be configured to alert users of anomalous traffic, such as a device repeatedly trying to access one device or cycling through a string of network addresses. IDS is a monitoring tool and is not used to actively manage the network.
The partitioning of vulnerable sensors into Virtual Local Area Networks (VLANs) is important to mention at this point. VLANs partition the network and will restrict traffic from the vulnerable sensors into the enterprise. VLANs can also quarantine compromised devices from the network itself. Firewalls and firewall rules can be implemented between VLAN’s to enhance security between different network subnets.

Network access control (NAC) incorporates Access Control Lists (ACLs) to grant entry into the network. Devices not existing in the ACL will either be quarantined or redirected to a VLAN. NAC can also be configured to restrict compromised devices from accessing the network. NAC also replaces port security, where a specific network port is to a specific network device. This capability eliminates device replication.
Compliance scanners audit the network and notify administrators of devices that do not operate on recommended software versions or have not been properly patched. Scanning can occur daily, weekly, or monthly. Once non-compliant systems are detected, the administrators must update the software and patches to maintain compliance. Comply-to-Connect remedies non-compliant hardware that do not have recommended software updates or critical patches.
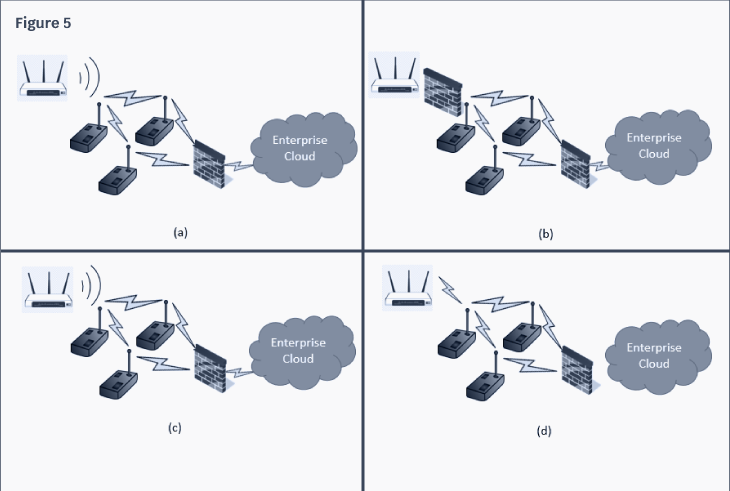
IoT networks are dynamically scalable and use Certificate Authority to manage the public key infrastructure (PKI) for the network. The CA releases certificates to trusted devices. When a device comes online and starts communicating, it shares its credentials with the enterprise. If the enterprise recognizes its credentials, the device is integrated into the network. If the credentials are not recognized, it is not allowed to join the network. Figure 5 shows this interaction. Figure 5 (a) and (b) demonstrate a wireless device whose credentials are not recognized and are firewalled from the network. In Figure 5 (c) and (d), the enterprise network recognizes the certificate and allows the device to join the network. PKI can also be used to encrypt the data through key use, further hardening the sensor network.
Zero Trust policies has gained prominence as insider threats evolved. Zero trust follows the principle of least privilege, where network access is granted on role, user group, and specific access requirements. For example, basic users do not need administrative access to the enterprise network, however, network engineers will need this access to maintain the network. This policy is also known as role-based access control (RBAC). Zero-trust also incorporates and manages alerts that record and notify stakeholders of anomalous behavior such as off-hour database access.
Conclusion
This article presented opportunities to incorporate cybersecurity best practices into any organization undergoing digital transformation. Businesses must focus on technology tools, management policies, and training to improve their security posture. Common cyber risk trends were also discussed to stress potential vulnerabilities exploited by hackers. Best practices were discussed throughout the system lifecycle. Strategies were presented to help develop policies, self-audits, and corrective actions into observed vulnerabilities. IoT, which has gained significant traction during the last decade, is also vulnerable and susceptible to exploitation.










