With technology advancing faster than ever, cybersecurity is crucial for safeguarding next-generation Information and Communication Technology (ICT) solutions. Emerging technologies such as artificial intelligence (AI), 5G, and IoT are transforming the cybersecurity landscape, presenting both opportunities and challenges.
AI, in particular, is a double-edged sword. On one hand, it enhances cybersecurity by automating threat detection, analyzing vast datasets, and predicting vulnerabilities. On the other hand, cybercriminals are leveraging AI to create more sophisticated attacks, such as deepfakes and adaptive malware. Additionally, integrating AI into cybersecurity introduces challenges like adversarial AI, bias in AI models, and regulatory compliance.
Cybersecurity Challenges in the Age of Innovation
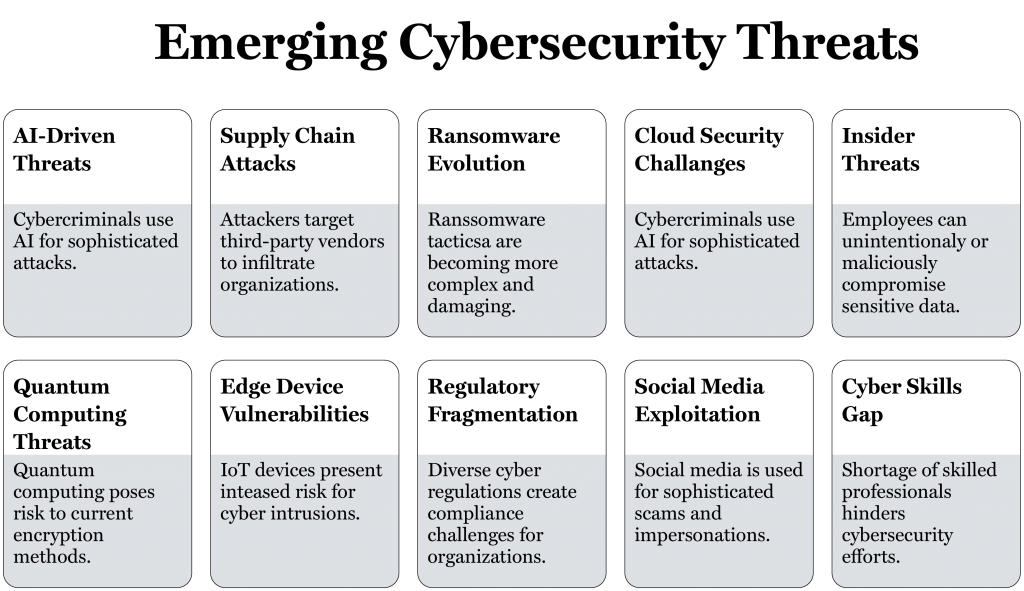
In 2025 and beyond, the cybersecurity landscape is evolving rapidly, with new threats and vulnerabilities emerging due to technological advancements and changes in attack vectors. Below are some of the key emerging threats in next-generation ICT:
AI-Driven Threats
Cybercriminals are weaponizing AI to create highly sophisticated attacks, such as targeted phishing campaigns, polymorphic malware, and deepfake fraud schemes. Since ChatGPT’s public launch in late 2022, phishing attacks have surged by an astounding 4,151% due to generative AI.
- Phishing Campaigns: AI can generate compelling, personalized phishing emails that are harder to detect.
- Polymorphic Malware: AI-driven malware can change its code to evade detection by traditional security measures.
- Deepfake Fraud: AI can create realistic deepfakes to impersonate individuals or executives, leading to fraudulent activities.
Supply Chain Attacks
Cybercriminals are targeting third-party vendors and suppliers to infiltrate larger organizations, exploiting the trust and access granted to these external entities.
- Compromised Vendors: Attackers gain access to sensitive systems through vulnerabilities in third-party software or hardware.
- Software Bill of Materials (SBOM): Organizations must track and verify software components in order to detect vulnerabilities in dependencies.
Ransomware Evolution
Ransomware attacks are becoming increasingly sophisticated, incorporating encryption, data exfiltration, and extortion tactics.
- Double Extortion: Attackers encrypt data and threaten to release stolen information if a ransom is not paid.
- Triple Extortion: In addition to encryption and data release threats, attackers may also launch DDoS attacks if the ransom is not paid.
Cloud Security Challenges
The adoption of cloud services continues to grow, but cloud environments present unique security challenges, including misconfigurations, data breaches, and unauthorized access.
- Misconfigurations: Cloud settings that are not correctly configured can expose sensitive data to attackers.
- API Vulnerabilities: APIs are often the weakest link in cloud security, making them a target for attackers.

Insider Threats
Employees, contractors, and partners with access to sensitive information can pose a risk if they misuse their privileges or fall victim to social engineering attacks.
- Accidental Breaches: Employees may unintentionally share sensitive information with AI platforms like ChatGPT, leading to data breaches.
- Behavioral Analytics: Tools that monitor user behavior can help detect unusual activities that may indicate insider threats.
Quantum Computing Threats
Quantum computing holds the potential to break conventional encryption methods, posing a significant threat to current cryptographic techniques.
- Future-Proofing: Organizations need to explore quantum-resistant cryptographic solutions to prepare for the future impact of quantum computing.
Edge Device Vulnerabilities
The proliferation of IoT devices and remote work hardware presents an area of increased intrusion and exploitation, with a rise in zero-day vulnerabilities.
- IoT Security: IoT devices are often less secure and more challenging to monitor, making them an attractive target for attackers.
- Network Segmentation: Segmenting IoT networks from critical IT infrastructure can mitigate security risks.
Regulatory Fragmentation
The proliferation of cyber regulations worldwide creates complexity for organizations operating across multiple regions.
- Compliance Challenges: Organizations face difficulties maintaining compliance with fragmented regulations, which can lead to legal repercussions.
- Unified Standards: There is a growing call for globally unified data protection standards to address cross-border data flows.
Social Media Exploitation
Social media and generative AI enable sophisticated attacks such as targeted scams and impersonations.
- AI-Generated Content: Attackers can use AI to create convincing content for scams and impersonation attempts.
- Bots and Deepfakes: AI-driven bots and deepfakes can make it difficult to distinguish real from fake interactions.
Cyber Skills Gap
The cybersecurity industry faces a significant shortage of skilled professionals, making implementing and managing advanced security solutions difficult.
- Training Programs: Investing in training and certification programs can help bridge the skill gap.
- Public-Private Partnerships: Collaborations between governments and private organizations can accelerate the development of cybersecurity talent.
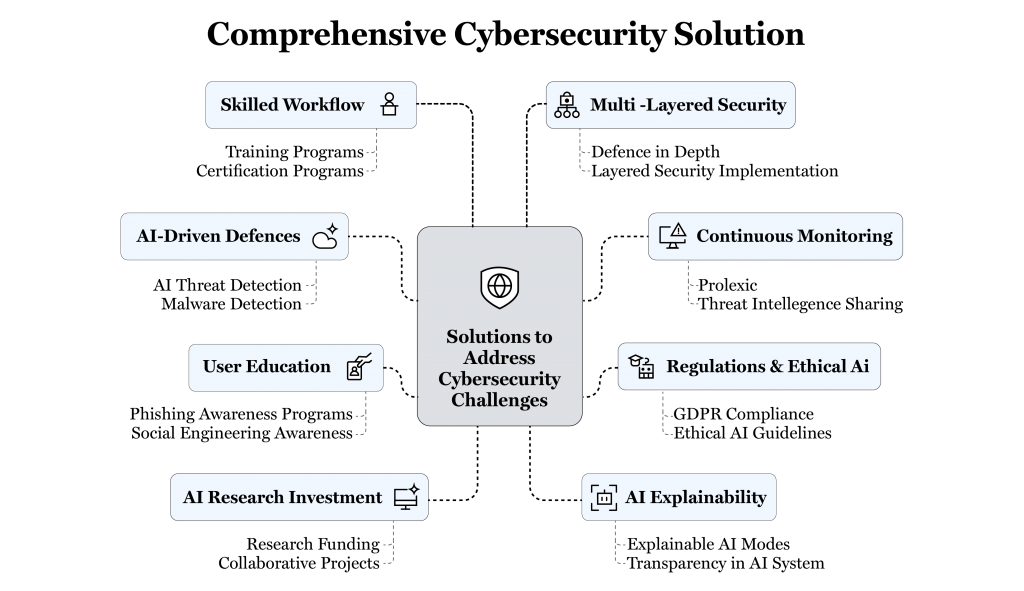
Solutions to Address Cybersecurity Challenges
Implementing AI-Driven Defenses
Organizations can leverage machine learning algorithms to detect anomalies, identify zero-day vulnerabilities, and respond to threats in real time.
- AI Threat Detection: AI systems can analyze network traffic in real time to spot unusual patterns or potential issues that can harm the network. This helps identify and mitigate cyber threats such as unauthorized access and network intrusions.
- Malware Detection: AI-based algorithms can identify malicious software by analyzing file behavior and system changes. Unlike traditional methods that rely on known malware signatures, AI can detect new and emerging threats.
Continuous Monitoring and Threat Intelligence
Cybersecurity frameworks should include continuous monitoring of networks and systems. AI-powered threat intelligence platforms can analyze data from global sources to identify emerging threats.
- Prolexic: Akamai’s Prolexic platform proactively reduces attack surfaces and instantly stops DDoS attacks. It uses real-time threat intelligence to identify and mitigate large-scale attacks.
- Threat Intelligence Sharing: Organizations can share threat intelligence across industries to collectively defend against evolving cyber risks. This collaborative approach helps to stay ahead of attackers.
Strengthening Regulations and Ethical AI Development
Governments and regulatory bodies should establish ethical guidelines for AI development and enforce strict regulations to limit the misuse of this technology.
- GDPR Compliance: Organizations must ensure compliance with data protection regulations like GDPR when collecting, storing, and processing data for AI purposes. This helps maintain user privacy and avoid legal repercussions.
- Ethical AI Guidelines: Establishing ethical guidelines for AI development ensures that AI systems are used responsibly and do not cause harm. This includes transparency in AI decision-making processes.
Educating Users and Employees
Human error remains one of the weakest links in cybersecurity. Educating users and employees about potential threats, such as phishing scams and social engineering tactics, can significantly reduce risks.
- Phishing Awareness Programs: Training programs that educate employees on recognizing phishing attempts can significantly reduce the risk of successful phishing attacks. AI algorithms can also help by analyzing email metadata and content to detect and block phishing attempts.
- Social Engineering Awareness: Regular training sessions on social engineering tactics help employees understand and report suspicious activities, reducing the risk of information theft.

Investing in AI Research and Development
Governments and businesses should fund AI research to stay ahead of adversaries and construct robust systems.
- Research Funding: Investing in AI research helps develop advanced tools and techniques to combat emerging threats. This includes funding for academic and industry research projects.
- Collaborative Projects: Public-private partnerships can accelerate the development of AI-driven cybersecurity solutions. These collaborations bring together expertise from different sectors to create more effective defenses.
Enhancing AI Explainability
Creating interpretable AI models promotes transparency and trust, facilitating compliance and decision-making.
- Explainable AI Models: Developing AI models that can explain their decision-making processes helps build trust and ensures that AI systems are used responsibly. This is particularly important for compliance with regulations like GDPR.
- Transparency in AI Systems: Ensuring that AI systems are transparent and understandable helps identify and correct biases, improving the overall effectiveness of AI-driven cybersecurity solutions.
Building a Skilled Workforce
Upskilling the workforce in AI and cybersecurity is critical for meeting future needs.
- Training Programs: Investing in training programs to upskill existing employees in AI and cybersecurity helps bridge the skills gap. This includes both technical training and soft skills development.
- Certification Programs: Offering certification programs in AI and cybersecurity ensures that professionals have the necessary skills to implement and manage advanced AI-driven solutions.
Multi-Layered Security Approach
Deploying various security measures at different levels, such as firewalls, intrusion detection systems, endpoint protection, and data encryption, ensures comprehensive protection.
- Defense in Depth: Using multiple layers of security, including physical, technical, and administrative controls, creates a robust defense against cyber threats. This approach ensures that even if one layer is breached, others can protect the system.
- Layered Security Implementation: Implementing tools like web application firewalls, bot management, and data encryption helps protect against various threats. For example, Imperva offers layered security solutions that protect data and networks through multiple layers.
Governmental Support for Cybersecurity:
United Kingdom
- National Cyber Security Centre (NCSC): The NCSC was established to protect the UK’s critical services from cyber threats, manage major incidents, and improve the underlying security of the UK’s internet. It provides support to critical organizations, the public sector, industries, and SMEs.
- App Security and Privacy Code of Practice: The UK government proposed a new code of practice to enhance app security and privacy, requiring app stores to implement vulnerability reporting processes and share security information.
United States
- CISA and NSA Guidance: The US government’s Cybersecurity and Infrastructure Security Agency (CISA) and the National Security Agency (NSA) published guidance on securing the software supply chain, focusing on open-source software. This initiative aims to improve the security of software development and infrastructure.
- Quantum-Safe Initiatives: The US government is investing in research and development to prepare for quantum computing threats and ensure critical infrastructure is quantum-resistant.
Saudi Arabia
- National Cybersecurity Authority (NCA): Saudi Arabia’s NCA has introduced three key cybersecurity frameworks: Essential Cybersecurity Controls (ECC), Cloud Cybersecurity Controls (CCC), and OT Cybersecurity Controls (OTCC). These frameworks strengthen cybersecurity resilience across all sectors and ensure alignment with the nation’s goals for a secure digital economy.
United Arab Emirates (UAE)
- Comprehensive Cybersecurity Strategy: The UAE has established the Information Assurance (IA) Regulation to align national cybersecurity efforts and protect critical information and communications infrastructure. This regulation covers management and technical security controls, governance and risk management, information security management, network and communication security, and incident management.
Qatar
- National Cybersecurity Strategy (NCSS): Qatar’s NCSS is a strategic framework for enhancing the nation’s cybersecurity capabilities. It prioritizes the defense of critical sectors such as energy, finance, and transportation and promotes cybersecurity awareness and skill development among citizens and organizations.
Canada
- Legislation and Funding: Canada introduced Bill C-26 and the Critical Cyber Systems Protection Act (CCSPA) to enhance cybersecurity across critical sectors. Additionally, the government committed $675,000 CAD to support Quantum-Safe Canada’s project, which aims to raise awareness and preparedness for quantum threats.
Singapore
- Cybersecurity Industry Call for Innovation: Singapore’s Cyber Security Agency (CSA) launched CyberCall 2022, inviting cybersecurity companies to develop innovative solutions in AI, cloud security, IoT security, and privacy-enhancing technologies. This initiative aims to strengthen cyber resilience and catalyze cutting-edge solutions.
India
- CyberShikshaa Program: The CyberShikshaa program is a public-private partnership that trains women in cybersecurity. This initiative helps build a diverse cybersecurity workforce and addresses the gender gap in the industry.
Ghana
- Cyber Security Authority Partnerships: The Cyber Security Authority partnered with the Elizabeth Sloane Institute of Technology (ESIT) to develop cybersecurity skills. This partnership aims to scout and nurture cybersecurity talent from a young age, encouraging students to pursue careers in the field.
Togo
- Public-Private Partnership for CIRT: Togo established a national Cybersecurity Incident Response Team (CIRT) through a public-private partnership with Cyber Defense Africa (CDA). This initiative leverages private sector expertise to build local cybersecurity capacity and reduce financial barriers.
Senegal
- Regionally Oriented National School of Cybersecurity (RONSC): Senegal launched RONSC to provide cybersecurity education and training. This initiative aims to build a skilled cybersecurity workforce and support regional cybersecurity capacity building.
Oman
- Comprehensive IT Governance: The Sultanate of Oman’s Ministry of Transport, Communications, and Information Technology (MTCIT) has implemented digital strategies, policies, and frameworks to ensure effective IT governance and risk management. Key policies include the IT Governance Policy, Information Reference Model (IRM), and Basic Security Controls Guidelines.

Conclusion
Governments worldwide are taking proactive steps to enhance cybersecurity. These initiatives include establishing dedicated cybersecurity agencies, introducing legislation, funding research and development, and creating public-private partnerships. These countries aim to build resilient digital environments and protect critical assets from emerging threats by investing in cybersecurity education, infrastructure, and innovation.









