Worldwide there are several reasons for project start-ups, but what are the real reasons behind it. Another question to be asked here is “is there enough attention for Information Security in projects”? The drawbacks of information security are both project and business risks. Referring to the investigation of Price Water House Cooper we may notice a 48% increasing rate of incidents, there are 117,339 Information Security incidents a day summing up to a yearly cost of 42,8 million. Additionally, the estimated damages worldwide peak to 2,7 million dollars for each incident. These figures mark a decrease of as much as 34% since last year! Thus, the urgency of companies comes down to how they can strengthen Information Security in the daily business and projects, by also eliminating ‘security leaks’ in the scope of Project Governance. Commonly Businesses do not become aware of such issues related to the Project Governance. In other words, the management becomes so occupied protecting the house and forgets the barn or even the new building in progress.
For effective Project Governance Security you must embed:
• A Project Governance strategy, policy, a project plan/roadmap, project architecture and independent assurance;
• A temporary project organization with ownerships, roles, accountability, responsibilities, and segregation of duties;
• A Project Risk Management team with information on project risks, project management framework, risk assessment abilities, certification, training, education, dependence on project interfaces or key specialists, job changes and/or termination, knowledge sharing and project security awareness;
• Project configuration with identification, maintenance of configuration items, configuration repositories, and their baseline;
• Project Incident Problems and Incident/Problem Management; for incident escalation, and incident response on security issues;
• Project Change Management standard and procedures; For impact assessment, priority and authorization;
• Project development; A Project methodology for secure development, implementation;
• Project data classification; like ownership, classification, security requirements, exchange policy, disposal;
• Project Identity & Access Management for Access rules, Access rights project administration, super users and periodic phase review of access rights;
• Project Security Management with Company- Project security baseline in line with the strategy and policy, i.e.; authentication mechanism, mobile devices, teleworking, logging, security testing, surveillance, monitoring, threat and vulnerability, infrastructure resources, protection, availability, maintenance, project network security etc.;
• Project operations for job processing, back-up and recovery procedures, capacity and performance management;
• Business continuity after the closure of a project; business- and project continuity planning in line with continuous improvement (lesson learned), service level management and imbedding the Deming Cycle “Plan, Do, Check and Act”.
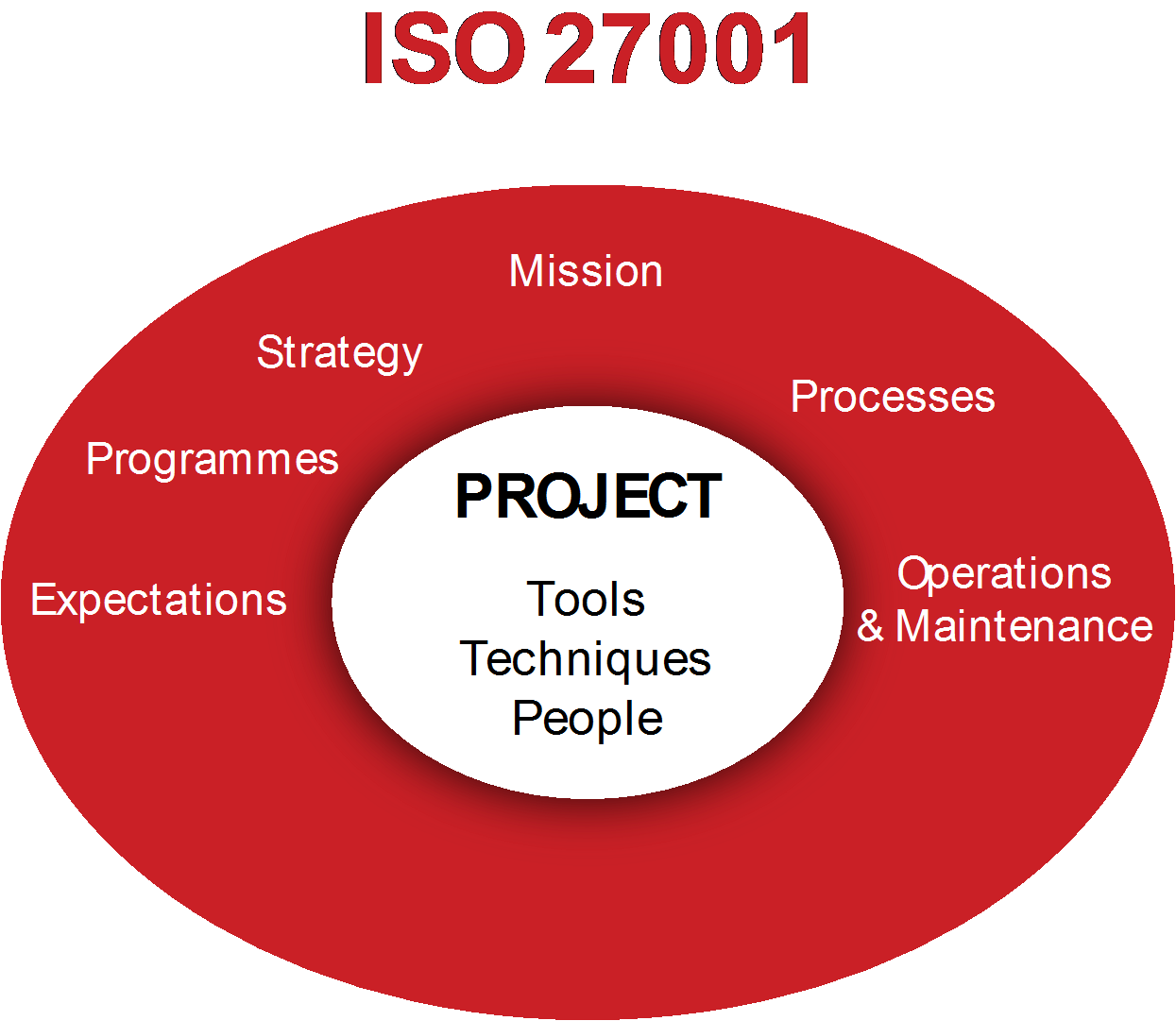
ISO 21500 project management, in this case, is definitely advisable, being that, ISO 21500 is familiar with international project management and covers PRINCE2, International Competence Baseline (ICB), and PMI, it is also compatible with ISO 27001 and ISO group 55000, 2001, 9001 and 31000. This ISO family is compatible with: project control mechanism, policy, business governance, PDCA cycle control mechanism, screening, awareness, project and company continuity/hygiene. However, these are only some of the strongest points by adapting ISO21500 in combination with ISO 27001.
Following this direction displayed above and ISO normalization with a ‘practical handyman’, both the internal audit department and steering committee get a clear overview of the necessary steps for improvement in terms of security standardization and continuous improvement. Other international PM methodologies are also free to use, but, with ISO (International Organization for Standardization) you can prove:
- The difference between ‘industry peers’;
- Application for Bench Marketing, Best Value Procurement, and European tenders;
- That procedures around ‘Information Security in projects’ are under control;
- The risks are known and that you can set-up or initiate the mitigations;
- Standardization;
- And that Quality is bound to increase through continuous improvement
Correspondingly, in order for the Steering Committee to ensure a clear vision and involvement/sponsoring for ISO decisions concerning ‘Information Security in projects’, they need to answer:
- What quality level do we need for ‘Information Security in projects?’ What is the common or standardized ISO 27001/ISO 21500 level?
- What is our current situation presently?
- What are the steps to undertake for minimalizing the project and business risks?
Answering these questions is undoubtedly difficult. Managers do not always have enough overview or a consistent way of working. Therefore, they need professional consultants and tools to get a clear overview to address various issues happening to their organization. So, to a company, a proper project development plan supplemented by training and coaching may facilitate easier implementation.
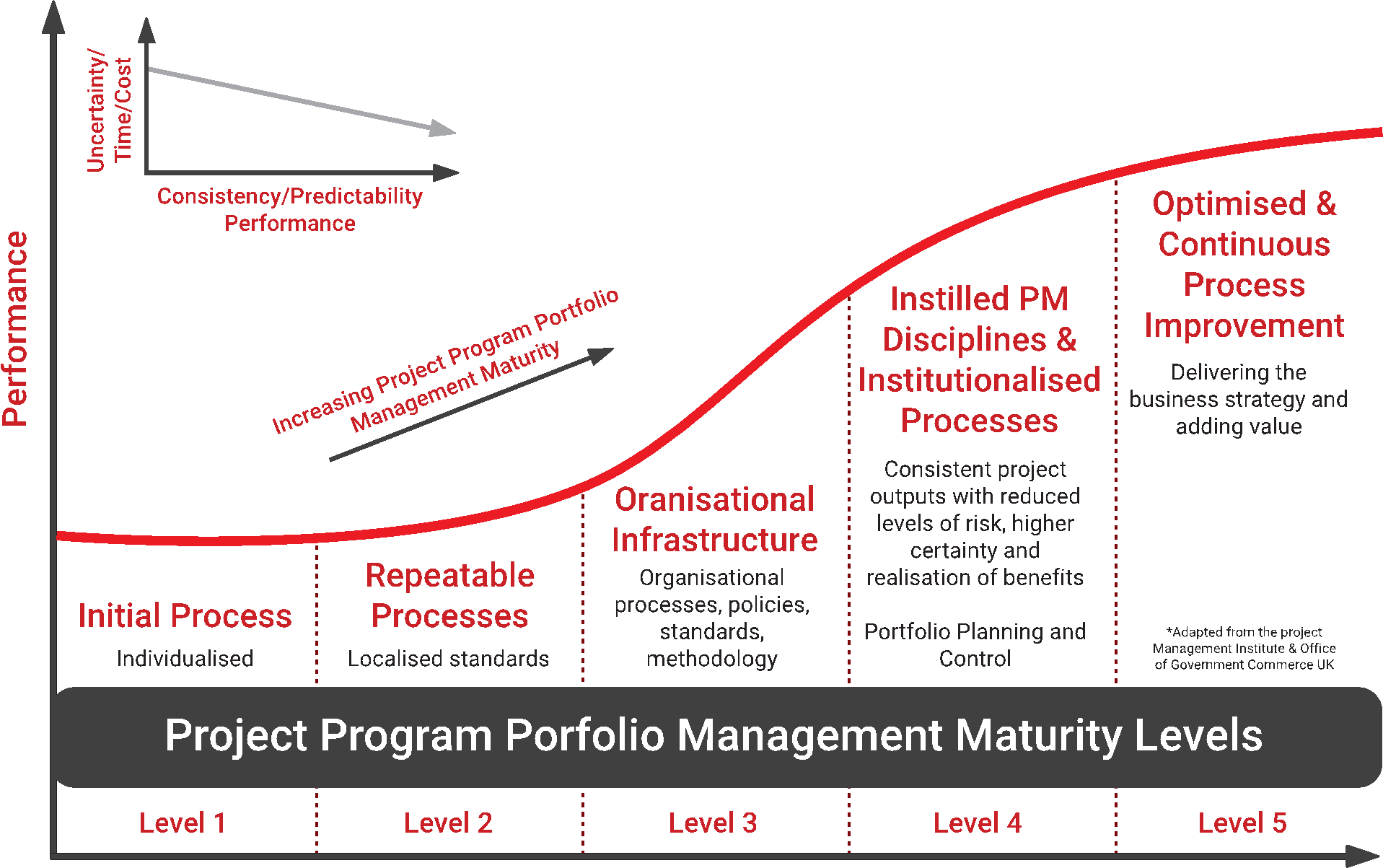
ISO21500 helps you with project management maturity
During the last decades, several attempts have been made to determine the relationship between the maturity level of a company and project performance. After studying projects with 200 different organizations in 30 countries, it turned out that; the lower the maturity level of the company is, the higher the chance of project failure. Therefore, ISO 21500 project training help your organization to reach a higher level of maturity (read quality), which will undoubtedly lead to cost reduction up to an estimated 30%, as well as minimalize risk of project failure and naturally give more effectiveness of your projects.
Moreover, your company will certainly also benefit from:
- Proven, internationally recognized quality framework;
- Transfer of knowledge between projects and organizations;
- Integration with specific standards;
- Continuous improvement;
- Business continuity and business hygiene;
- Having a diagnostic tool for assurance and assessments.
If you have reached ISO 21500/ISO27001 certification, then you should take a moment to celebrate this achievement! You need to tell your customers, vendors, employees and any other stakeholders of your accomplishment.
Tips and Tricks for Security
It is recommended to get a clear overview of your network information while limiting Internet usage in your company or project environment for prevention from various outside risks and malware. Make a choice of a Risk Management methodology i.e. ISO 31000; plan weekly, monthly, quarter and yearly risk audits with several scenarios; invent external specialists and entrepreneurs; take a look on the outside, not only inside; What can happen? Which security development do you see? What is the news? Set-up and initiate a Security prevention team in your Governance with clear job descriptions about tasks, authorities, and responsibilities. Look at your internal company and project procedures if they are not too bureaucratic. Invest in professional and standardized company and project management information security. Adapt ISO 27001, ISO 21500 and ISO 31000. Be aware of the damage, costs if insecurity occurs. Create a permanent program for your employees and contractors. If they are not competent, screened and well trained they are your biggest risk. You need to create with the Human Resource Department, Business Manager and employee a Personal Development Program and awareness program of training.
PECB
As a progressively harmful phenomenon to our society as much as the whole business environment, Information Security should not be neglected; regardless of the industry, you are operating. Thus, we must give significant importance to the implementation of various Information Security frameworks. Likewise, implementing ISO 27001 in projects will confidently increase your project’s likelihood of success. Harmoniously, PECB is pleased to offer you with thorough training on effective implementation while certifying you in ISO 27001.