In the context of the major health crisis caused by the novel coronavirus (COVID-19), that our planet is going through, hackers and cybercriminals are trying to take advantage of the situation to attack the impacted companies and exploit their vulnerabilities, particularly those caused by teleworking.
A great number of companies have switched to remote working overnight, operating in partial and degraded mode, without necessarily being previously prepared for the risks associated with nomadism.
Organizations that had not previously taken into account or poorly prepared the scenario of unavailability of human resources in the framework of their business continuity plans found themselves deprived and obliged to improvise in an emergency the confinement of their employees and working remotely without taking into account all the necessary security, good cybersecurity practices, and especially without having tested their crisis management systems and remote access in such scenarios.
The weakest links in this equation are on the one hand the company’s staff, because they are not sufficiently aware and trained regarding the risks associated with remote working, and on the other hand the information systems, because they are not prepared for this unusual operation.
The risk of exploitation of vulnerabilities induced by the health crisis situation thus becomes stronger by more offensive and opportunistic threat agents in the current context, as the reported attacks and the figures that have been compiled are there to prove. Thus, since the beginning of the pandemic, many serious cybercriminal actions have already been carried out. According to indicators, hundreds of millions of dollars have been paid to Bitcoin accounts that spread ransom, tens of thousands of new domains registered since the beginning of the pandemic including hundreds of domains used by phishing and spear-phishing campaigns.
In this particularly sensitive situation, companies must now adopt an emergency cybersecurity strategy to deal with these unexpected risks.

The experts and analysts of ACG Cybersecurity recommend to carry out an emergency cybersecurity action plan to deal in the best possible way with the submerging threats of the pandemic crisis COVID-19:
1. Awareness of the risks associated with cybersecurity
It is never too late to set up and run targeted and sustainable cybersecurity awareness campaigns among business users on the risks associated with teleworking and the proper use of teleworking tools, by diversifying the awareness channels.
2. Support for information systems specialists
Good management and support of the IT and Cybersecurity teams in charge of the information system and its security is essential in crisis situations. Increasing their skills can become a priority, in particular by supporting external teams of specialized consultants, available on the consulting market, and then by targeted training strategies.
Reinforcing the security of nomadic devices through additional security measures could prove necessary even in the heat of the moment. The ultimate goal is to establish a sustainable culture of security by design from the very beginning of IT projects. As the company is not immune to internal threats, monitoring and control of privileged access must be carried out continuously and effectively through IAM systems and well-defined procedures.
3. Vulnerability assessment and scanning
The first way to protect your information system is to assess its security level by conducting periodic campaigns of scans and vulnerability tests of IT devices and assets. This consists of an examination of the ability of systems or applications, using security procedures and controls, to resist attack, followed by the immediate correction of major and critical nonconformities.
Vulnerability assessment therefore consists of analyzing the network for known security weaknesses.
Vulnerability scanning tools recognize, measure, and classify security vulnerabilities in a computer system, network, and communication channels. They also help security professionals secure the network by identifying security flaws or vulnerabilities in the current security mechanism before they can be exploited by malicious parties.
Vulnerability assessments are used to:
- Identify weaknesses that could be exploited
- Predict the effectiveness of additional security measures to protect information resources from attacks
Typically, vulnerability scanning tools search the network segment for IP-enabled devices and list systems and applications.
4. Technical security audit and penetration testing
At this stage and in this context of major crisis, vulnerability scans are not sufficient to protect information systems. That is why organizations must also conduct technical audits and penetration tests to test computer systems by putting themselves in the postures of hackers by using other techniques to exploit vulnerabilities not identified by vulnerability scanners.
It is therefore recommended to conduct security audits and penetration tests in order to identify configuration flaws and complex vulnerabilities by analyzing the attack scenarios envisaged by cyber-malicious agents.
The security assessment through security audits and penetration tests aims to identify configuration defects, vulnerabilities that exist on assets at the level of the organization’s information system before they are exploited
by malicious actors.
Penetration testing consists of simulating malicious attacks on your
information system, network, or organization in real conditions. Its
objectives are to determine the level of resilience of your computer system against attacks from inside or outside your network.
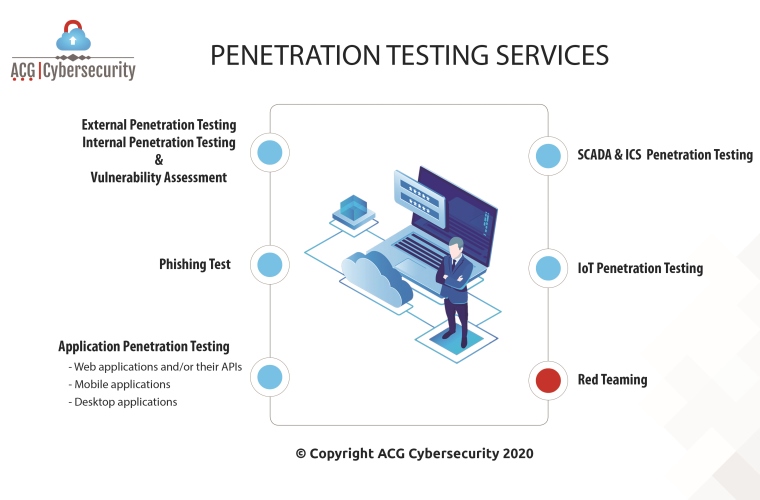
There are several levels of pen testing services to deal with cyber-attacks in such situations:
Internal intrusion test: Simulated attacks are employed by a person wishing to commit a malicious act by being present on your company’s internal network.
External intrusion test: Simulated attacks will be carried out from the outside, with or without knowledge of your organization’s infrastructure. The objective is to mimic the real actions of a hacker who does not have access to your internal network.
Phishing test: The purpose of phishing tests is to carry out an inventory of the level of awareness of your employees by launching one or more phishing test campaigns.
Technical security audit: Configuration or compliance audits allow you to evaluate the IT security of your network by analyzing the configuration of your technical bases, including operating systems, software, application servers, and network equipment. The source code audit allows you to exhaustively detect vulnerabilities affecting an application, in order to validate the respect of good development practices.
The architecture audit allows you to identify global technical flaws on your information system, and to validate the relevance of technological choices and the respect of good security practices.
In conclusion, neither zero risk nor absolute security exists, and companies remain perpetually exposed to the risks of cyberspace. They must nevertheless know how to anticipate and prepare scenarios and major risk situations that can lead to crises making companies even more vulnerable.
Organizations must ensure the effectiveness of their information systems and guarantee continuous improvement to ensure adequate protection of their most sensitive assets.
In addition, the simulation of cybersecurity attacks through penetration tests as well as the review and testing of continuity and crisis processes becomes essential to ensure that the most relevant scenarios have been taken into account in the risk analysis.









