Digital Technology use has been steadily rising over the last decade, but COVID-19 significantly accelerated this trend. Due to widespread lockdowns, leading to a rise in “work from home” arrangements, companies and individuals were forced to use digital solutions on a never-beforeseen scale. For example, before COVID-19, Zoom, one of the leading videoconferencing apps, had 82,400 business customers. In 2020, its business customers increased to 470,100, an increase close to 600%. Similarly, neobanks – financial institutions not previously connected to banking infrastructure, are projected to increase their revenue from $3.6Bn in 2020 to $6.8Bn in 2021.
Unfortunately, the increased use of digital technology provides opportunities for legitimate businesses and malicious actors, such as large cyber syndicates, individuals, and small criminal groups. According to ScamWatch, an initiative of the Australian Government, in 2019, there were 53,882 reported attempts for stealing personal information. In 2020 the number rose to 82,182, while for just the first eight months of 2021, the number is 81,618. Malicious actors are targeting not just individuals but also organizations. The Internet Crime Complaint Center reported one successful attack every 1.12 seconds in 2020. At the same, CyberEdge Group says 86.2% of surveyed organizations were affected by a successful attack.
Considering the above statistics, it is easy to understand why individuals and senior managers in various organizations are very concerned. As a result, the budgets for managing digital risks have increased together with the number of approaches in fighting cyber-crime. These approaches include employee training, changes in policies and procedures, and increased use of ethical hacking.
An introduction to cybersecurity and hacking
Ethical hacking involves trained cybersecurity professionals carrying out activities to penetrate an organization’s cybersecurity defenses with the organization’s permission. These cybersecurity professionals are also known as “white hat hackers”. The white hat hackers use the same skillset, approaches, and tools as the black hat hackers. The main difference between the two groups is motivation and intent. Black hat hackers carry out their activities with malicious intent. When a black hat hacker discovers a vulnerability, they exploit that for their gain. Their motivation can be financial, political, or a combination of these. White hat hackers are employed by an organization. While they usually work undercover to obtain a more accurate picture of the situation, their intent is not malicious. Any vulnerabilities discovered by white hat hackers are reported back to the organization to be promptly addressed. White hat hackers sometimes are also known as penetration testers.
The approaches used by all hackers include no-tech, lowtech, and high-tech activities. No-tech activities include shoulder surfing, social engineering, and dumpster diving. A hacker will try to gain valuable information like passwords or personal details during shoulder surfing by glancing inconspicuously at someone’s screen. Dumpster diving involves going through rubbish containers and finding valuable documents that were thrown out instead of being shredded. Finally, using social engineering, a hacker pretends to be someone they are not to get sensitive information from another party. One of the best-known hackers, Kevin Mitnick, used social engineering extensively in his pursuits.
Low-tech hacking involves limited and very often ingenious use of simple technology or gadgets. Examples of lowtech hacking include using aluminum strips from cans to pick locks; standard utilities like ping to see if a specific network address exists and accepts connections; or Google Hacking, where common Google queries are enhanced to provide additional information to hackers.

High-tech hacking, while usually complemented by noor low-tech activities, is decidedly different. This type of hacking involves the use of various tools to automate and enhance the discovery of vulnerabilities and exploiting them. Examples include: installation of various types of malware like rootkits – software providing the highest level of privileges; ransomware – programs blocking device or data access; and botnets – computer networks used to send spam or mount distributed denial-of-service (DDoS) attacks.
An introduction to artificial intelligence
Considering the vast array of constantly evolving approaches and tools used by cybercriminals, it is logical to assume that at least the same level of innovation is required in the fight against cybercrime. One of the technologies steadily rising in popularity amongst ethical hackers is Artificial Intelligence (AI). The main goal of AI is to mimic the behaviors of a human. These include the capability to generalize, learn, and constantly adapt.
Some examples will make the above points more straightforward. For instance, when a human sees digit ‘1’ written in different ways, as shown in figure 1, they will recognize it 98% of the time. The same set of digits, however, will look like five different objects to a software program. We see the same thing because of our ability to generalize, derive characteristics and classify objects based on our earlier experience.

Humans also constantly learn and adapt their behaviors. For example, if a child starts eating hot cereal and burns their tongue slightly, the child will start waiting until the cereal cools down after several such occurrences. In the process, the child will begin grouping or clustering in AI parlance objects into hot and cold and respond appropriately. However, what seems natural to us is anything but to a computer. Replicating human behavior within a computer system is what AI aims to achieve. AI as a field of research and implementation has been around since the mid-1950s. With big hopes and promises, academics, programmers, and engineers worldwide have worked tirelessly to advance AI and make it applicable in everyday activities. This endeavor was not straightforward and contained numerous ebbs and flows. Over the last ten years, the revival of AI applications has been due to the increased computing power available, mainly because of cloud computing advances to individuals and organizations. Current AI technologies are based on several approaches contained within each other, as shown in figure 2.
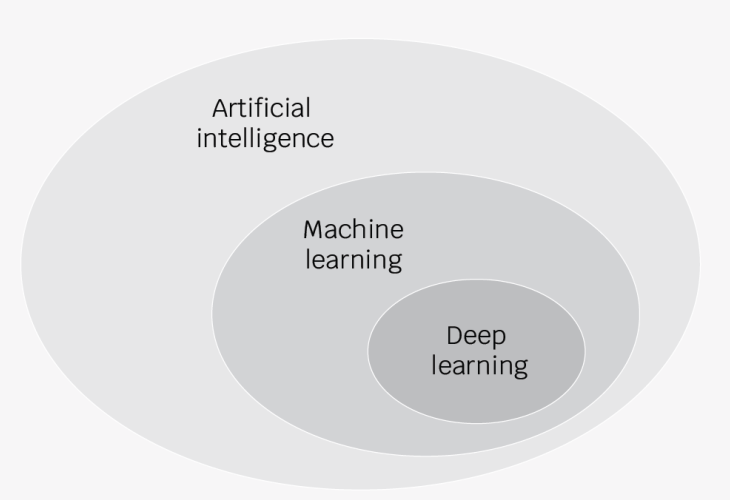
Figure 1.1 Artificial intelligence, Machine learning, Deep learning
(Source: Deep Learning with Python)
Machine learning is one of the most popular types of AI currently in use and includes discovering patterns within datasets. It is a bottom-up approach because a problem is not entirely defined, but it is up to the system to identify missing relationships and patterns. Two of the most widespread machine learning technologies are decision trees and neural networks.
Deep learning is gaining popularity but is still in its infancy. It is a specific type of machine learning, neural networks, and is based on the idea that including additional layers in a neural network will improve its capabilities.
Deep learning became feasible because of the significant increase in available computing power in the last several years.
Artificial intelligence is the broadest concept and, in addition to machine learning and deep learning, includes technologies like expert systems, search engines (Google), speech recognition (Alexa, Siri), etc.
Using artificial intelligence in ethical hacking
As mentioned above, three key characteristics of AI are the ability to learn, the ability to adapt, and the ability to generalize. These characteristics make AI a necessity in ethical hacking activities. The main reason behind this is that black hat hackers constantly change their strategies, tactics, and actions. In turn, white hackers need to adapt to identify issues and vulnerabilities and address these continuously. Here are some examples of how ethical hackers can use AI.
Analyzing user activities
One of the activities ethical hackers do is send phishing emails to all employees to test their awareness and attention. Hackers widely use phishing emails to obtain sensitive information or to gain unauthorized access to a system. A phishing email entices users to click on a link or visit a web page through promises, threats, or both. Once they do that, either a piece of malware is installed and executed, or confidential information is requested.
When a phishing awareness campaign finishes, user responses are analyzed, and policies and procedures are adjusted accordingly. By using machine learning, specifically decision trees, ethical hackers can identify the characteristics of users more likely to become victims of phishing and, therefore, represent a high risk to the organization. For example, employees from specific departments, particular age groups, or certain educational backgrounds may be twice more likely to be deceived than the rest of the organization. In such cases, these employees will have to undergo additional training to reduce their susceptibility to fraud.
Identifying new attack patterns
All computer networks management tools currently include a logging mechanism. Log files are rich information sources that record and show user activities, network access attempts, system, application issues, etc. When a successful attack occurs and is subsequently detected, its characteristics, such as origin, time, type of hardware, and others, are recorded in the log files. By analyzing those attacks using decision trees, a kind of machine learning, ethical hackers can identify specific vulnerabilities and address those.
For example, if all successful attacks on a network originate in Sierra Leone, a recommendation would be to restrict all traffic from Sierra Leone in some way. Of course, this is an oversimplified example, but it demonstrates how the approach works in an actual situation. Due to its effectiveness, this type of analysis is already part of all popular intrusion detection systems (IDS).

Increasing cyber defense accuracy
It is a well-known fact that no cyber defense is 100% effective. There always will be cases when legitimate access is classified as hacking and blocked; so-called false positives or actual intrusions are allowed through – false negatives. Over time, these occurrences accumulate, and a library of them exists in an organization. By using neural networks, a type of machine learning, it is possible to build and train a parametric model of an intrusion. Afterward, the neural network will automatically classify network access as legitimate or not, improving the overall accuracy of ethical hackers’ activities.
In addition, a system based on neural networks will be highly adaptable. This adaptability will be achieved by including all the new mistakes in a training dataset and training the neural network again. This approach is valuable since black hat hackers are constantly changing their actions, and ethical hackers are doing the same to remain effective.