5G deployments have grown exponentially during the last 24 months, according to industry reports the world will reach +1 billion 5G connections in 2022, and +4.87 billion connections by 2027, combined with the fact that 6.5GB average consumption per subscriber, with the reach of 15GB in 2022. This is a scale of networks the world has not seen before and the risk of not knowing what we are going to manage is greater than any value that will come from technology advancements.
The biggest concern, doubt, or customer requirement to migrate services fast on these next generation networks largely depends on how the Security Architecture will address the following key points:
- Data Control and Security
- User Rights and Privacy
- Network Security
This discussion must be the first starting point for any Future Network architecture plus with early beta type 6G networks expected to be in 2027 era, we are just at a 5 year gap from something, we in the Telecom industry, have not been prepared for.
This is why I have selected this important topic of “Network Security Architectures for 5G, Cloud, and Disaggregated Telecom Infrastructure” to share my view on how we can address these requirements, what we have accomplished, and where there are gaps that need to be addressed promptly.

Why Secure Connectivity is Vital
Telecom systems since the time of inception are trusted and believed to deliver societal value but mostly the trust in security is assumed which raises questions when it comes to 5G Networks which are based on Cloud connectivity models.
Alone in 2021, the Network attacks rose by 31% , this is why Telco’s spending on security infrastructure to build future Networks.
It is not only the security of Networks but also data, as per industry progress 73% of Telco’s data remains untapped to deliver business value. Therefore, one important aspect of delivering security is enabling the right End-to- End data architecture that enables security as a service solutions across the Networks all the way from Cloud, to Core, to Edge.
5G Security Challenges
There has been a long debate on what should be the right architecture for 5G and future Networks, and already within ITU and 3GPP this domain is well addressed. However, the real challenge of the new technology wave will only come once we deploy it in a distributed fashion at scale.
This is because almost every real-use case of 5G and monetization sits outside the data center or a central colocation. Large scale deployments of 5G means that typical Telco will need to deploy thousands of mini 5G networks for enterprise, each of which will have unique needs. In addition, they cannot afford data aggregation in datacenters, so it must be broken out and processed at the nearest point of value, which mostly will be near to the source at the Edge.
This makes Telecom security discussions more challenging because Edge is where IT&OT really meet the Telco world. It also means that simply Telecom security architecture will not be enough and that to make any real-use case from this complexity there is only one promised deployment model which is based on “Network Disaggregation”.
Understanding of this End-to-End story is of critical importance before we devise any architecture or solution.
In an Open and Disaggregated world there are just too many entry points for any security breach. The vital importance of security and how it should be approached was experienced in 2022 by Toyota motors who were forced to halt operations across all of its plants in Japan, following an attack on Kojima Industries, which supplies the auto giant with vital parts.
What it really entails is that merely one view on security is not enough, it also means we need to enable new and agile methodologies in Telecom around security with “intrinsic security” as a base and foundation to design and build any network.

Data Architecture Challenges
During the time the world was shut down due to COVID-19 what kept it still functional behind closed doors was Telecom’s critical infrastructure and the systems that made it possible to access the needed services in a secure way.
Therefore, although government support to accelerate new technology rollouts like 5G and Edge was created, what came natively was increased spending on security.
Alone, the global spending on network security has reached $168 billion in 2022 which is over 15% in comparison to the previous year. What is obviously causing this is the horrendous growth of “data” to a level that we can safely say today’s business is all about data and an organization’s unique capability to manage it in a secure manner.
- Google does it by knowing people search habits
- Facebook does it through social circle
- Uber by navigating world’s traffic
- Telco’s by monetizing their Pole position
In one way or another Telecom Networks will be designed with more “data Driven Architectures.”

Cyber Resilient Networks
The biggest problem I have seen in Telecom Network evolution since the time of NFV is what we call an “Air Gap” problem. What it really means is that we want to keep existing security architectures and tune or reshape it to fit the IT and Cloud world.
Maybe it would have been nice if we started off from the IT world and brought the latest and greatest to meet Telco service needs. This could mean a more pragmatic approach to an operating model as 5G and future networks will scale.
In future networks of 5G, Edge, and Open RAN will be built on cloud native architectures, building secure products will not be enough but rather E2E secure data architectures will be required; “End-to-End Security Architecture based on intrinsic security will be the foundation of Next generation Telecom Networks.”
Such an architecture should be based on the following principles;
- Intrinsic Security – Which will mean security in each layer starting from silicon to supply chain to product retirement
- Automation – Which means real time security insights and security SoC before anything boils up
- Intelligence – As the frontier of data decade where we empower ML and AI on a trusted data to a level where we can make best-informed decisions
- Orchestration – Which means all the unnecessary details are abstracted to give a tenant only what it needs to know
Security Framework for 5G and NextGen Networks
Security requirements and challenges will be wider in 5G than in previous generations, reflecting the far broader range of potential use cases and potential threats.
Further contributing factors will come from the way 5G meets the need for higher speed and lower latency combined with power efficiency needs, a wider variety of actors and device types, and more use of the cloud and virtualization.
5G will be built upon network slicing and the “network of networks” concept. Any security measures must take both this and edge computing requirements into account. Below are the security dimensions in 5G:
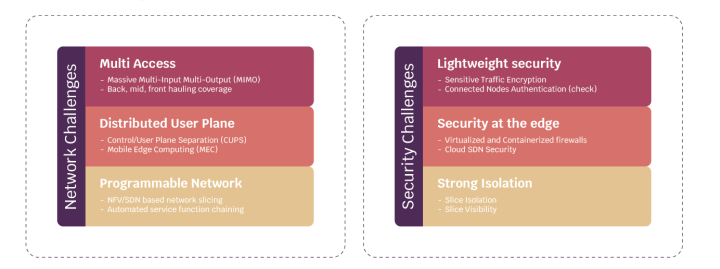
The main security requirements to secure the upcoming IoT/5G services fall under the following main categories:
- Identity Access Management and Authentication
- Communication Security
- Data Security (Confidentiality, Integrity, Availability)
These security requirements should be distributed over the below security layers:
- Network Layer Security: This layer can be split in two parts: network access (part of the control plane) and network application (user plane). Different types of access, i.e. 3GPP (5G, LTE-M, NB-IoT, etc.), or non 3GPP (Wi-Fi, Zigbee, etc.) can be considered. Under the umbrella of 3GPP, 5G/IoT will benefit from all the security and privacy mobile features, such as support for user identity confidentiality, entity authentication, confidentiality, signaling protection, and data encryptions. Although 3GPP defines several key security methodologies into its specification, CSPs still need to do the provisioning and configuration.
- Service layer security: Services can be split into those that are defined by 3GPP, i.e. 3GPP services and services that are provided by service providers or third parties. As such, service layer mechanisms are defined within the domain of the service provider and cover aspects, such as service authentication, confidentiality, integrity protection, and privacy.
- Application layer security: Service providers implement their services by providing applications to their subscribers. In addition to the security provided by the service layer, each application may implement additional or different security mechanisms. These could cover security mechanisms, such as end-to-end data encryption and integrity protection.
- Device or Endpoint security: Certain devices are required to implement security mechanisms in order to make sure only authorized users have access to device resources and in order to make sure that assets, such as the device identifier cannot be manipulated. Those mechanisms are covered within the device security layer. In addition, aspects as provisioning the UE with service or network access subscriptions, device theft, device integrity, and grouping of devices (e.g. for bulk authentication and management) are covered.
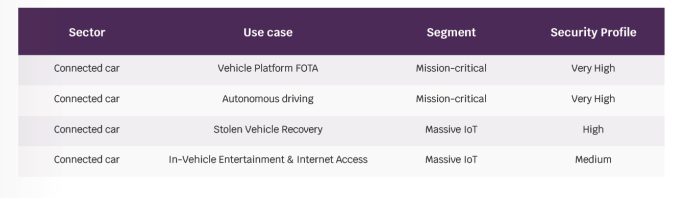
The security requirements should be defined per use case, but at the end it follows the CIA triad (Confidentiality, Integrity, Availability), the below are different use cases for connected cars with the required security profile level, as shown below:
Cloud Infrastructure Security
With the future networks based on open and standard open infrastructure it is important that security is enabled as a standard foundation in infrastructure that promises and guarantees SLA for the secure infrastructure, the foundation of such a resilient architecture should comprise of following reference architecture blocks:
- Safe BIOS: mitigates the risk of BIOS tampering with integrated firmware attack detection
- Safe ID: protects an IT and cloud infra using biometric security
- Cloud Security: all the way from TPM to HSM
- UEFI Secure Boot Customization: will protect your infrastructure from security vulnerabilities during boot
- SafeSupply Chain Tamper-Evident Services: verify nothing happens to the device during transport. These tamper-evident seals are added to the device and the box at the factory, prior to shipping. Pallet seals can also be added to increase security
- SafeSupply Chain Data Sanitization Services: prevent spyware or illicit agents from being injected into the hard drive
- Data control: using NIST 800-88 standards to ensure even in the case of 5G networks that are hosted on Public Clouds, the customers can manage to keep their data secure and control it
- RSA Secure ID and remote attestation: to cryptographically determine the identity of Baremetal servers
- Cyber Recovery for Sheltered Harbor: is a fast, costeffective, and efficient mean to protect critical data by adopting the vault mechanism and to recover the data in case of a network security attack
- Network Endpoint Security SafeGuard: will be needed to detect, prevent, and respond to the full spectrum of modern cyber-attacks with the least amount of administrative effort. It applies artificial intelligence (AI) and machine learning (ML) to streaming telemetry data to proactively detect and block network attacks

Multi Cloud Security
5G and Future Networks will follow different and diverse types of cloud to deliver services ranging from Telco cloud, to IT Cloud, to Public Cloud Providers, in such a case it is important to both reliably define security and also give tenants a real time visibility as it traverses across different clouds.
Based on GSMA FASG and Linux Foundation – Anuket, work and definition in MITRE framework the Multi Cloud Security Architectures should address the following needs:
- Policy controls: where Telco’s can declare the intent or policy, and workloads can traverse across clouds while complying to that policy SLA’s
- Real time visibility: where a common data model approach to capture events and behaviors across all infrastructures
- Security SoC: where all security related features are monitored to give both the end-to-end view and also enable a timely response
- CI/CD of Security Pipelines: which will focus on end-to-end automation of critical activities focusing on continuous security assessments, compliance monitoring, and security configurations control. “Finally, the most important piece will be the Operational model because there will be workloads that will be distributed across different cloud environments in such a case how we can ensure a consistent single pane of glass.”
Below is one holistic view on how Dell Technologies is supporting customers to deliver secure infrastructure and security solutions, like cyber recovery, to enable true Multi Cloud Era Security Architectures:
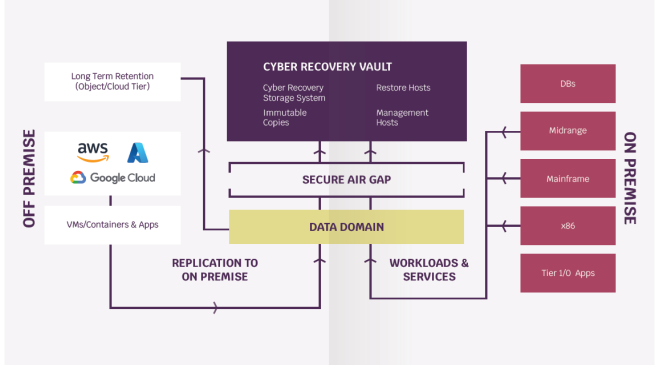
Conclusion
As 5G and future networks are scaling and more services are being migrated, the “Security” and “data control” become a central discussion.
However, there is no one standard that fully captures the Security requirements that can fulfill the unique requirements of Telecom and vertical industry, it is, therefore, important to build and define a holistic endto- end architecture based on “Zero Trust architectures” using a data driven approach and automation.
This also means that security must be designed intrinsically in every layer and then orchestrated to deliver, as a service, with unique characteristics required by different services and workloads, in a manner that will accommodate accordingly multiple fields and industries.
We, as an industry, still have a lot of work to do, especially by bringing all the Modern Edge and Hyperscaler architectures to the Telco works in a secure and reliable manner, however, it is worth mentioning that we have certainly solved certain issues and have seen and are seeing some early deployments that prove the fact that the Open and Modular infrastructures will be the foundation to deliver a seamless secure connectivity experiences in the new digital world.