For a long time now, communication has been considered the fundamental way that allows people to share anything between them. If in the past communication was made via only month or percussion instruments, nowadays, technology continues to bring new ways for people to communicate, passing any distance or obstacle between them with the invention of the mobile phone, internet, GSM, cloud, etc. The technology evolution brings the creation of network infrastructure from small, medium, and large enterprises. Today, enterprise networks allow personnel or employees within the organization to collaborate, meetings, calls, trainings, etc., and to easily share in a timely manner things such as information, documents, images, videos, etc., among each other.
An Enterprise Network can be defined as an infrastructure, hardware, and software, which connects a number of an organization’s devices. E.g., hardware devices, such as computers, servers, routers, switches, firewalls, and load balancers. These devices support software applications such as operating systems and network management software, as well as procedures and processes that work together to help organizations exchange data or information.
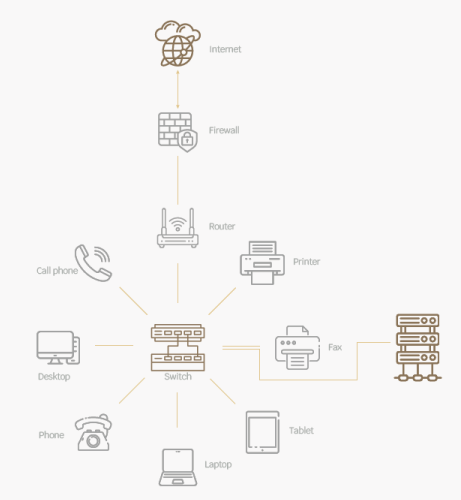
Figure 1. Enterprise networks
While Risk Management process is a systemic application of management policies, procedures, and practices to the activities of communicating, consulting, establishing the context, and identifying, analyzing, evaluating, treating, monitoring, and reviewing risks. [Source: ISO Guide 73: 2009, 3.1].
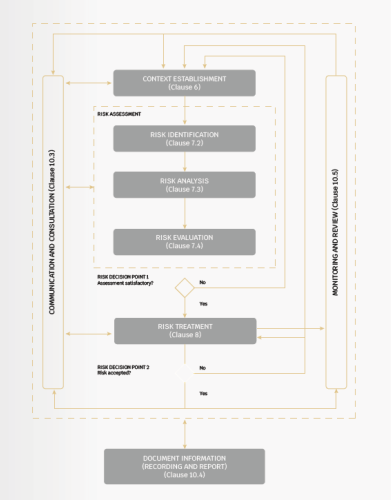
Figure 2. Information security risk management process (source: ISO/IEC 27005:2022)
ISO/IEC 27005 based on the information security risk management that promotes two main approaches: one side “event-based approach”, and another side “assetbased approach”. An event-based approach underlines identification and assessment of risk through an evaluation of events and consequences. Otherwise, events and consequences can often be determined by a discovery of the concerns of top management, risk owners, and the requirements identified in determining the context of the organization (ISO/IEC 27001:2022, Clause 4). While an asset-based approach underlines concepts of the risk identification and risk assessment through an inspection of asset, threats, and vulnerabilities. In addition, an asset is anything that has value to the organization, and therefore, requires protection.
ISO/IEC 27005 Within Enterprise Networks
Referring to the description above, enterprise networks match with asset-based approach for the risk management process. Each component of the enterprise networks, such as laptops, telephones, servers, switches, routers, printers, software, etc. are considered supporting assets, for which risks should be identified and assessed, because they support information or processes within the organization. As these are considered primary business assets.
Enterprise networks are so critical that the risk assessment should be performed on regular basis so that organization or business remain resilient. Therefore, ISO/IEC 27005 formalizes and standardizes the enterprise networks risk management process within the organizational information technology system. ISO/IEC 27005 ensures information security risk management by providing minimum baseline controls so that integrity, confidentiality, and availability of the enterprise networks can be maintained at an acceptable level in case of any security incident occurring within an organization’s information system.
Furthermore, ISO/IEC 27005 relates to risk management within enterprise networks by assessing and evaluating risk on each network component following typical criteria:
- Consequences
- Likelihood
- Level of risk

Consequence criteria: ISO/IEC 27005 is concerned with the consequences that are directly or indirectly affected by the preservation or loss of confidentiality, integrity, and availability of the enterprise network assets.
Likelihood criteria: ISO/IEC 27005 is concerned with the likelihood that promotes the probability of the event to occur in each time frame within the enterprise networks. There are many aspects that likelihood criteria could depend on, such as accidental or natural events, level of exposure of assets, technology failure, human acts, omissions, etc.
Level of risk criteria: ISO/IEC 27005 gives the opportunity to the risk owner of enterprise networks to decide about retaining or otherwise treating risks, and to prioritize them for risk treatment. Therefore, the level of risk can be determined qualitatively toward enterprise networks (critical, high, medium, low) or quantitatively (1, 2, 3, 4, or value of money lost, amount of time lost, fatalities, etc.)
ISO/IEC 27005 by its fourth edition published on October 2022, underlines information security, cybersecurity, and privacy protection guidelines on managing information security risks. The scope of ISO/IEC 27005 covers security guidelines from data, applications, systems, and networks within the organization.
Many organizations do not systematically handle risk management within enterprise networks, as they are constantly preoccupied with considering mainly business or financial risks on a daily basis. They formalized risk management processes mainly around business or financial risks, giving less importance to technology risk management, as well as operational risks related to technology operations. As concerned with risk in the technology landscape, ISO/IEC 27005 remains the standard that can help organizations assess and evaluate information risks around their technology assets to stay ahead of any breach of security.
In most organizations, risks are not considered to be on the same level of importance, i.e., some organizations might prioritize financial risks or operational risks, while others prioritize legal or technology risks. However, all prevail the fact that the business of the organization in its activities pursues objectives that depend directly or indirectly on financial, legal and fiscal, environmental, but also technological means.
Technological risks have been less considered by organizations in comparison to financial, operational, legal, tax, and environmental risks. Very often, the technological risks are not even documented or formalized, which, unfortunately, are only dealt with when a security incident occurs in the technological environment of the organization.
Technical staff is responsible to communicate clearly and in an understandable manner all presentations of technological risks while making sure that employees are updated and know their responsibilities.
In the absence of a formalized technological risk management framework, organizations in Central Africa have been using SIEM (security information and event management) tools or independent SIEM contractors for almost 10 years to monitor events taking place in their technological infrastructures, in turn, the enterprise networks.
For instance, SIEM services have been used by most Telco organizations to monitor events occurring within their infrastructure’s networks. Banks, for example, are now more interested in international security requirements, as such SWIFT Customer Security Program (CSP), Payment Card Industry Data Security Standard (PCI DSS), ISO/IEC 27001, etc.

Conclusion
ISO/IEC 27005 within risk management processes for enterprise networks requires taking into account the following steps, based on ISO/IEC 27005: 2022:
- Define the scope of the enterprise network by:
- Identifying network assets, such as network personnel, network devices, contractors, a business process supported, legal entity, etc.
- Formalizing risk management process (assessment, treatment, etc.)
- Define risk acceptance criteria by determining:
- Consequence criteria, such as loss, failure, damage to assets, etc.
- Likelihood criteria, such as probability or frequency of accidental or natural events
- Criteria for determining the level of risk that combines consequence criteria and likelihood criteria
- Define the risk impact level.
- Identify and describe information security risks that involve the identification of risk sources and events. It is possible by two approaches commonly used to perform risk identification:
- Event-based approach: Examine risk sources to develop strategic scenarios and how impact-interested parties can help achieve risk-desired outcomes
- Asset-based approach: Identify operational scenarios, which are detailed in terms of assets, threats, and vulnerabilities
- Identify risk owners that will be associated with the list of identified risks. This person will:
- Be accountable and have the authority of managing the risks they own, i.e. they should have a position in the organization that allows them to actually exercise this authority
- Understand the issues at hand, and be in a position to make informed decisions (e.g. regarding how to treat the risks)
- Evaluate the information security risks by comparing the results of risk analysis with the risk criteria afterward, prioritizing the analyzed risks for risk treatment.
- Select appropriate information security risk treatment options based on the list of prioritized risks with events or risk scenarios that lead to those possibilities.
- Determine all controls that are necessary to implement the information security risk treatment options referring to prioritized risks with the selected risk treatment options.