The increasing nature of cybercrime
Application services in the cyberspace have gained a huge importance in our lives expanding beyond the business-to-consumers and consumer-to-consumer models to a form of many-to-many
interactions and transactions, called the Internet of Everything (IoE), predicting that by 2020 there will be more than 200 billion devices that will join this group.
In some organizations, the system devices have become quite open and are on the way to lose direct control of data security. The IoE is causing an increase in threats and vulnerabilities; thus, it is becoming the target of cyber crime in terms of sensitive customer information, intellectual property and even the control of key machinery are increasingly being at risk from cyber attacks. The targeting of electronic assets has the potential to make a material impact on the entire organization and its stakeholders.
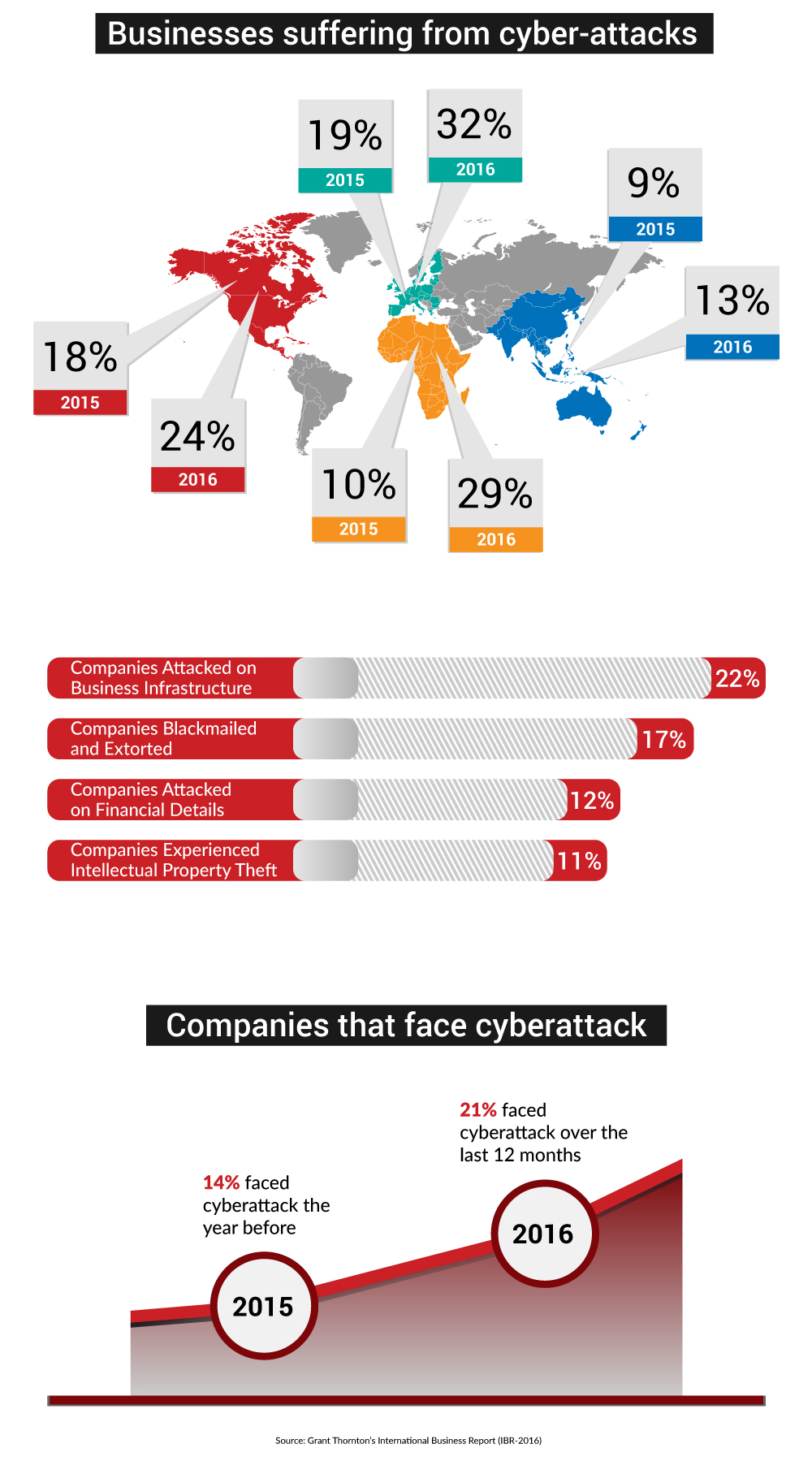
The IBR findings also reveal that globally, of those business leaders who have faced a cyber attack in the last 12 months, nearly one in eight (13%) only realized that the attack had occurred more than a week after the event. For 4% of them, it took longer than a month. Cybersecurity is the preservation of confidentiality, integrity, and availability of information in the Cyberspace. In ISO 27032, clause 4.20 specifically, includes the protection of assets from threats mostly related to malicious and other human activity through a risk assessment and controls selection to counter and reduce risk at the acceptable level.
Cybersecurity depends on information security, application security, network security, internet security and CIIP (Critical Information Infrastructure Protection). There are personal assets (individual consumer’s online identity, bank account, medical data, banking and online payment accounts, email accounts, pictures, videos, music records, personal digital devices, PC) and organizational assets ( networks, servers, works stations, reputation, business plans, intellectual property, brand) in cyberspace. Some threats to personal assets are:
• Person’s online identity is stolen or masqueraded;
• Unauthorized access to persona’s financial information theft of the person’s money and fraud;
• Endpoint being made a zombie or bot virtual theft and virtual mugging
Threats to organizational assets are:
• Website defacement;
• URL stolen by cyber-squatters;
• Information on employees, clients, partners or suppliers disclosed;
• Financial reports breached;
• Unauthorized access to important information on governments
In the assessment of vulnerabilities process the possible reasons that stay behind threat agent activities should be identified:
• Motives (religious, political, economic, etc.)
• Capabilities (knowledge, funding, size, etc.)
• Intentions (fun, crime, espionage, etc.)
The roles of individuals in the Cyberspace may assume different roles in different context and applications and can include the following:
• General cyberspace application users, such as online gamer player, instant messenger user, or web surfer;
• Buyer/seller, involved in placing goods and services on online auction and marketplace sites for interested buyers, and vice versa;
• Blogger and other contents contributor;
• Independent Application Provider (IAP) within an application context;
• Member of an organization;
• Other roles, that a user can be assigned a role unintentionally or without his or her consent.
The government, primarily law enforcement agencies and regulators, may have the following important engagements to play with:
• Advise organizations of their roles and responsibilities in the Cyberspace;
• Share information with other stakeholders on the latest trends and developments in the technology;
• Share information with other stakeholders on the current prevalent security risks;
• Be a conduit for receiving any information, whether close or open, with regard to security risks to the Cyberspace; and
• Prepare the primary coordinator for information dissemination and orchestrating any required resources, both at national level or corporate level, in times of crisis arising from a massive cyber-attack.
Cybersecurity framework
To address cybercrime and social changes, many governments and institutions launched cybersecurity initiatives, ranging from guidance, through standardization, to comprehensive legislation and regulation. There are several cybersecurity frameworks available, where the most known are:
• ISO/IEC 27032:2012 – Guidelines for cybersecurity
• NIST Cybersecurity Framework
ISO/IEC 27032:2012
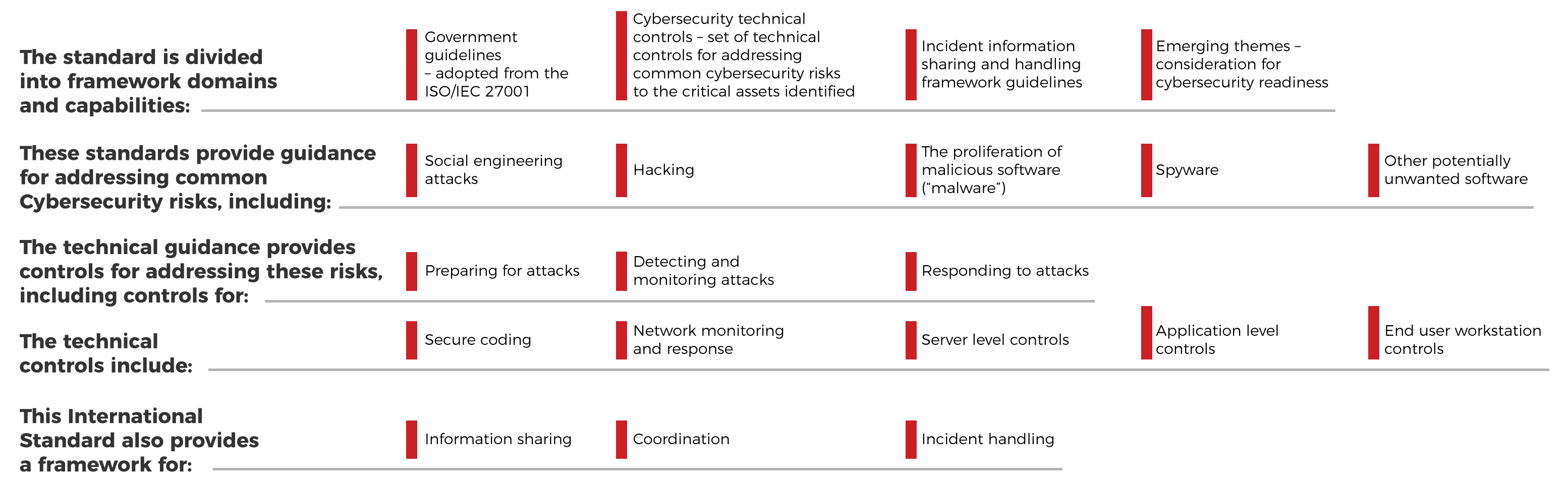
Is an international standard published by ISO, which presents a guideline for cyber security implementation and security practices for Stakeholders in the Cyberspace. It provides an explanation of the relationship between other types of security and also presents a framework to enable stakeholders to collaborate on resolving Cybersecurity issues.
This International Standard gives focus to three main themes of cyber security that intelligence agencies and national bodies concerned with the protection of critical national infrastructure and with the in-depth research necessary to take place, in order to provide practical solutions that organizations can implement to help mitigate these threats:
• Roles;
• Policies;
• Methods;
• Processes; and
• Applicable technical controls.
• Dark Net Monitoring – Attack Detection;
• Traceback – Attack Investigation;
• Sinkhole operation – Attack Response
NIST Cybersecurity Framework
Published by the Commerce Department’s National Institute of Standards and Technology, this framework focuses on using business drivers to guide Cybersecurity activities and considering Cybersecurity risks as part of the organization’s risk management process.
It includes:
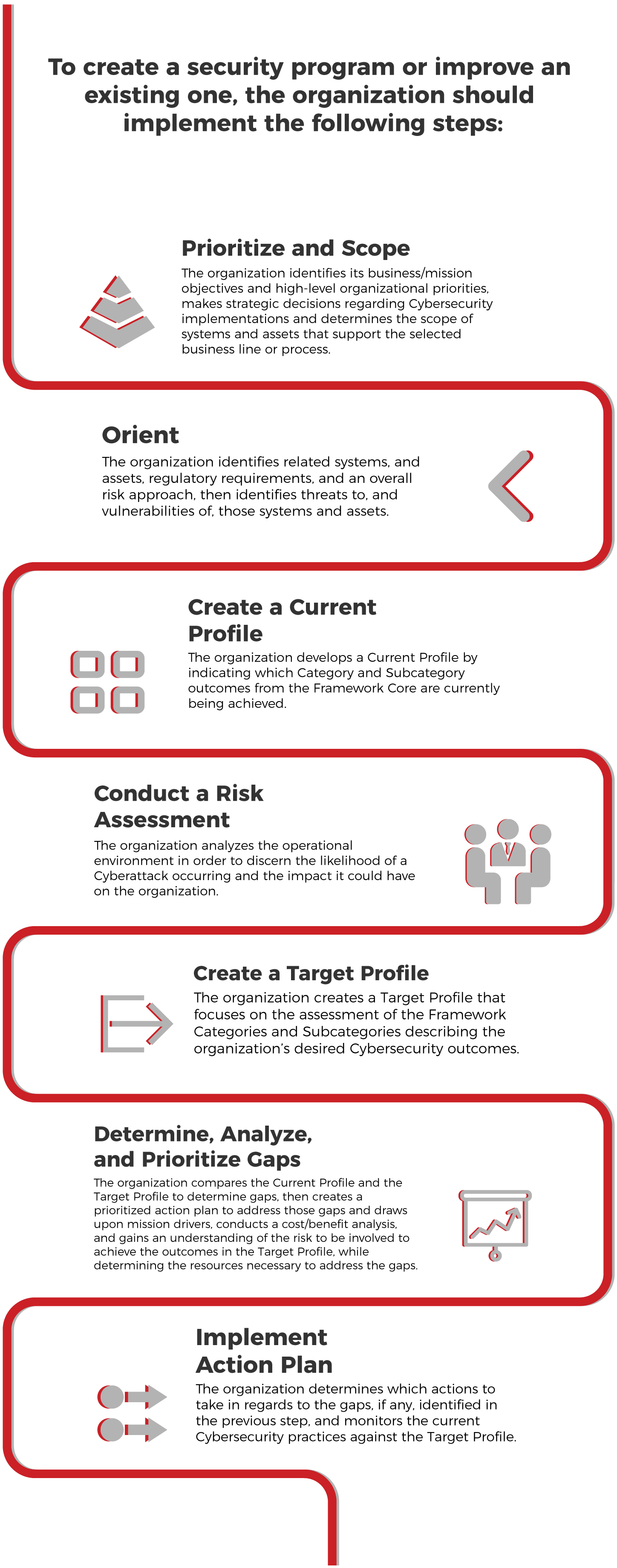
• Framework Core (a set of Cybersecurity activities, desired outcomes, and applicable references that are common across critical infrastructure sectors. It consists of five concurrent and continuous functions; Identify, Protect, Detect, Respond and Recover, identifies underlying key Categories and Subcategories for each function and matches them with example Informative References),
• Framework Implementation Tiers (provide context on how an organization views Cybersecurity risk and the processes in place to manage that risk, and
• Framework Profile (identify opportunities for improving Cybersecurity posture by comparing a “Current Profile” with a “Target Profile”).
The five Framework Core Functions are not intended to form a serial path, they can be performed concurrently and continuously to form an operational culture that address the dynamic Cybersecurity risk.
• Identify – develop the organizational understanding to manage cybersecurity risk to systems, assets, data and capabilities.
• Protect – develop and implement the appropriate safeguards to ensure delivery of critical infrastructure services.
• Detect – develop and implement the appropriate activities to identify the occurrence of a Cybersecurity event.
• Respond – develop and implement the appropriate activities to take action regarding a detected Cybersecurity event.
European Strategy for Cybersecurity
The European Union (EU) and its member states have launched wide-ranging programs and initiatives to strength cybersecurity, responding to the challenges with a defense of cybersecurity initiatives, including the following:
• The European Network and Information Security Agency (ENISA) was formed in 2004 to provide guidance and recommendations for information security;
• The European Commission issued a Cybersecurity Strategy that has been mirrored by a number of national strategies;
• A wide range of cybersecurity related activities in research and development, regulation and governance are occurring in the EU and member states.
• The EU cybersecurity strategy addresses the perspective that cybersecurity requires common definitions, frameworks and a sense of direction throughout all member states and associated states.
• To adequately address the risk and threats of cybercrime, enterprises need to embed cybersecurity, as an integral part, into their overall governance, risk management, and compliance (GRC) frameworks.
Embedding cybersecurity into GRC frameworks includes the following:
• Good governance that is in line with existing principles of corporate governance;
• Comprehensive management of cybercrime risk and threats that are aligned with existing enterprise risk management (ERM) systems;
• Compliance with existing or planned EU-level and national laws and regulations;
• Resilience for organizational infrastructures and personnel;
• Assurance for information, processes, and related controls.
Cybersecurity should also define and maintain appropriate interfaces with related disciplines, such as:
• Critical infrastructure protection
• National emergency management
• Public incident management and disaster management.
NIS Directive and national CSIRTs In December 2015, the Commission, the Parliament of the EU, and the Council of Ministers reached an agreement on the Network and Information Security (NIS) Directive. Chapter 3 describes the cooperation between competent authorities.
The Chapter defines two groups meant to improve NIS-related cooperation between MS. The first is the Cooperation Network, composed of representatives of MS, the Commission, and ENISA. This group is meant to focus on strategic issues. The second group is the CSIRT Network, composed of representatives of MS’ CSIRT and CERT-EU, with the Commission as observer and ENISA as Secretary and as an active supporter. The Security of the NIS of operators of essential services is described in chapter 4, defining security requirements for and duties of operators of essential services. The Security of the NIS of digital service providers is presented in chapter 4a, defining, security requirements for and duties of digital service providers.
Conclusions
Cybercrime is increasing as a cost to businesses due to cyberattacks in the past 12 months. At the same time, the increment of the Internet of Everything (IoE) is resulting in new vulnerabilities to the business and citizens. To respond, governments launched several initiatives to mitigate the cybersecurity risks, including:
• Establishment of cyber defense strategies
• the development of cyber-frameworks such as NIST
Cybersecurity Framework;
• the development of the CSIRT Network, composed of representatives of EU MS’ CSIRT and CERT-EU;
• the development of training and awareness programs;
• the enforcement of legislation
However, those initiates are not sufficient to combat the cybercrime nor to reduce the cybercrime trend. In addition, the ISO 27001 certification scheme does not assure that the controls and guidance established in ISO/ IEC 27032 are implemented and managed. Consequently, the UK Government has developed an industry support certification scheme (Cyber Essentials) providing criteria for organizations to measure their cybersecurity systems aligned with current cybersecurity best practices. Since October 2014 Cyber Essentials certification is mandatory for organizations looking to acquire certain government contracts that involve the handling of sensitive information and delivering particular ICT products and services.
It is necessary to establish an International certification scheme for cybersecurity management systems and the correspondent personnel certification for Implementers, Auditors, and Managers based on ISO 27032 and other cybersecurity best practices. Importantly, public organizations should require all their suppliers and subsuppliers to conform to the cybersecurity certification, as well as the operators of essential services and digital service providers. Likewise, governmental authorities should launch an awareness program regarding the combat and prevention of the cybercrime.
PECB
Certifying against ISO/IEC 27034 (https://pecb.com/iso-iec-27034-lead-application-security-implementer-certification) proves that the used applications within your organization pursue a framework of security. Additionally, competence would be increased to implementing the above-mentioned policies on cybersecurity through ISO/IEC 27032 Lead Cybersecurity Manager certification.