Cybersecurity poses a continuous risk for organizations of all shapes and sizes. Navigating the sector’s challenges and instilling a watertight cybersecurity culture is no simple task.
Strong leadership is not optional—it is essential. In recent years, many companies have come to recognize this and have reshuffled their IT security structure.
It is now common to see the role of ‘Chief Information Security Officer’ (CISO) spearhead cybersecurity efforts. It is easy to understand why—it centralizes both accountability and authority with a dedicated executive.
This article will introduce you to what CISOs do and why you need one. We will explain their responsibilities, areas of expertise, and how they can shape a culture of cybersecurity within your organization.
What is ‘cybersecurity culture’?
Cybersecurity culture encompasses the values, attitudes, knowledge, and norms that people in an organization hold in common to keep their data secure.
It is a measure of how well your business is positioned to deal with current threats and how resilient you will be to emerging threats in the near future.
Effective cybersecurity culture is not just about ticking off the boxes on a security checklist. Of utmost importance is staying up-to-date with news, trends, and updates, as well as staying ahead by noticing potential threats and reporting them, prior to them becoming a serious issue for the organization.
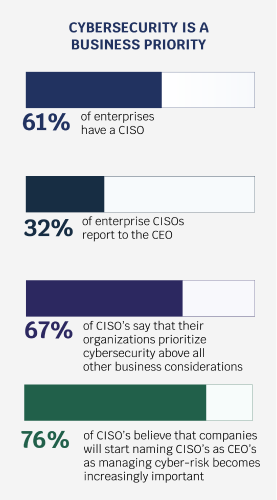
Why is cybersecurity culture so important?
Many businesses have experienced a ‘digital transformation’ in recent years—moving their data and assets from physical formats (e.g., paper documents, checks, payslips) to digital formats (e.g., cloud storage, digital IDs, eSignatures).
Digital transformation has been something of a miracle for productivity. Businesses can complete accounting, sales, and marketing processes faster and with less staff than ever before, increasing their margins and improving their bottom line.
However, this shift has also made data more accessible— both for employees within your organization and, sadly, malicious external actors. Instead of physically breaking into your store, hackers can now steal your sensitive documents simply by manipulating the right person, injecting malware, or even guessing the right password.
It is a growing problem, too. The cost of cybercrime is expected to grow exponentially in the coming years, with the global cost predicted to reach $23.82 trillion per year by 2027.
The truth is that we do not know where the cybersecurity industry is headed next. It is a constantly changing landscape, with hackers discovering new tools, exploits, and techniques all the time. For example, 94% of CISOs say that the speed of AI adoption is having the biggest impact on their roles. There is a constant battle being fought between cybersecurity experts and hackers. The only way to prevent the inevitable from happening is to take computer security seriously and create a solid cybersecurity culture in your team.

What are the weak points in an organization’s cybersecurity framework?
A fair assumption is that malware, ransomware, and computer viruses are the biggest threats facing the digital security of enterprises. Understandably so—as this style of hack is the most common depiction that we see on TV and in the media. But what if I told you that the weakest point in an organization’s cybersecurity is often the employees themselves? And no, this is not to say that your staff is actively malicious, just that they may be victims of ‘social engineering’ cyber-attacks.
One such type is phishing, one of the most common ransomware methods, where someone pretends to be someone that they are not. To demonstrate this with an example, suppose you are using phone interviews as part of your recruitment strategy.
The biggest risk when phone hiring is not that your wires could be tapped and your conversation snooped on, but rather that your recruitment officer is tricked into saying something they should not by a malicious actor on the other end of the line.
Another example is tailgating, where an attacker physically follows someone into their place of work and bluffs that they lost their ID card or something to that effect.
Cyber threat types responsible for business compromises (2020)
Methodology: The figures are based on the survey conducted in Q4 2020. The survey features data from 3,659 respondents who hold the ISACA Certified Information Security Manager certification. The responses “Don’t know”, “Prefer not to answer” and “Not applicable” are omitted from this figure.
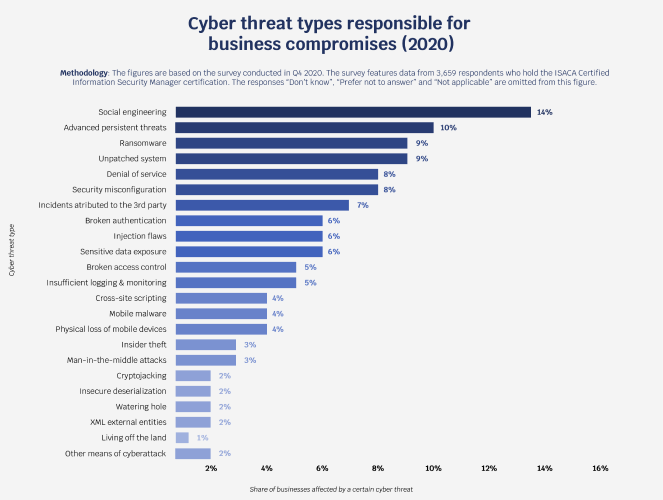
Source: www.atlasvpn.com
One you might not have heard of is the USB drop attack, where USB sticks with malware are left lying around outside a building. If they are plugged in, your organization’s data is already in jeopardy.
What role do CISOs play in shaping cybersecurity culture?
Therefore, where do Chief Information Security Officers (CISOs) come into the cybersecurity framework?
Let us start with a definition: A CISO is an executive company member who is responsible for keeping an organization safe from cyber threats. Typically, they report directly to the CEO, or sometimes, a group of CISOs may report to one Chief Information Officer (CIO).
In larger corporations, it is common for CISOs to focus on their niche of cybersecurity, including areas such as:
- Network security
- Incident response
- Security governance and policy
- Vendor risk management
- Employee training
In smaller companies, it may be up to one CISO to manage all of these responsibilities. This makes it a broadly varied role, tying together aspects of business leadership, IT security, HR, and resource planning.
Seven steps to implement a strong cybersecurity culture
1. Emphasize a leadership commitment
Leaders play a distinctive role in creating a cybersecurity culture.
The first thing a CISO should do is host a meeting and introduce themselves to the whole team. From now on, they will be the point of contact for cybersecurity matters, the voice of authority, and the person accountable.
They should emphasize the risks involved with data handling and how it requires a team effort to keep sensitive data out of a cybercriminal’s hands.
2. Implement clear action procedures
The next step is to create a clear framework of company policies related to data storage and transmission. This should act as a guide for employee behavior, both in and outside of the workplace.
Start by creating a set of escalation procedures that outline the steps employees should follow in case of a security incident or breach. These procedures should specify who to contact, what information to provide, and how to contain and report the incident promptly.
Additionally, you should develop access control policies to limit who can view, edit, or delete files. For instance, you may want to keep highly sensitive files related to employee personal information or payroll on a separate, encrypted drive.
3. Train your team accordingly
In this phase, you should spread common base knowledge of cybersecurity best practices among your team members. Certainly, you will need to arm yourself with the most up-to-date information first. Find out what you need to know to shield your business from ransomware and other common cyber-attacks, and be sure to stay abreast of changing guidance and share this with staff.
Whether it is taught in your employee onboarding or you need to provide some catch-up sessions, your program should at least cover these basic practices:
- Always be suspicious of unsolicited communication
- Verify someone’s identity before disclosing sensitive information
- Double-check whether an email has been spoofed by reading the sender’s address
- Hover over links to see if they lead to recognized websites
- Avoid downloading files from email
- Report websites without HTTPS to your security team (i.e., missing the ‘lock’ symbol to the left of your URL)
- Lock doors
- Never plug in unrecognized USB sticks
- Create strong passwords
Being aware of these common cybersecurity red flags will protect your organization from the vast majority of attacks. For more targeted training, use a WFM workforce management platform so you can easily see the progress and skills employees have already developed and schedule time for training sessions on their timesheets.
4. Conduct incident response planning
You can do everything right with cybersecurity and still be compromised by a sophisticated attack or a genuine mistake from a team member. In times like these, you will wish you had an incident response framework to follow. This provides clarity on the steps needed to follow, meaning everyone’s on the same page to ensure the cause of the damage is rooted out and quickly repaired.
Generally, a cyber incident response cycle goes as follows:
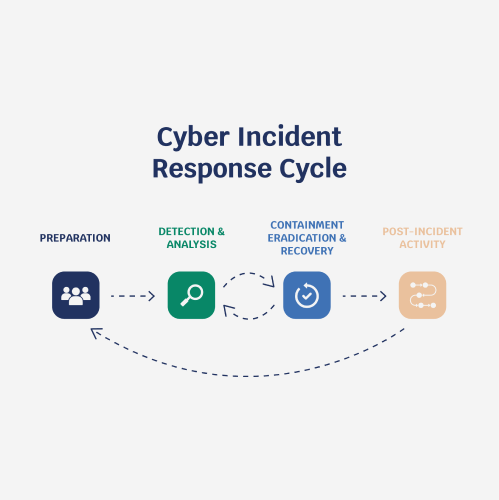
- Preparation: Creating a team with clearly defined roles and responsibilities
- Identification: Detecting signs that your systems have been compromised and classifying the incident according to the level of severity and urgency
- Containment: Preventing the attack from spreading and causing further damage
- Eradication: Removing the malware or root cause of the attack
- Recovery: Restoring systems to normal operation and testing the vulnerabilities
- Reflection: Understanding why the attack happened and taking steps to avoid it in the future
5. Secure your infrastructure
Communications infrastructure is a common target of attack, and it is obvious as to why—because it often hosts a business’s most sensitive data on clients, staff, contracts, and accounts. As such, your cybersecurity is only ever as good as your infrastructure is.
On the hardware side of things, businesses should keep their server rooms under lock and key, with strict controls on who can enter. It might seem obvious, but even installing alarms and CCTV cameras can act as a major deterrent against malicious activities.
As for software, businesses should be installing firewalls and intrusion detection systems to monitor network traffic. The CISO should be regularly updating and patching software to close zero-day exploits and known vulnerabilities.
Pay attention to cloud security as well, as this environment poses a variety of risks. Ensure sensitive data is encrypted with an external key and set up a robust access control policy.
It is worth evaluating all the forms of communication you use. If you use an internal communications platform, make sure you check the security of any third-party plugins and review the permissions your staff has.
Your sales team might use call center software for outreach. You should review your provider’s data policy if it is a hosted or cloud-based solution. It is also a good idea to regularly review communication best practices with all your staff.
Some businesses use dedicated high-security communications services to ensure all of their information is encrypted instead of insecure channels like email or SMS texting. This means that even if a network is compromised, hackers will not be able to make sense of your device’s conversations.
6. Monitor for threats
We have covered the main aspects of cybersecurity induction, but this does not mean that a CISO’s job is completed. Once your systems are secure and running smoothly, they will require constant monitoring to ensure hackers are not probing your business for attack.
CISOs should perform tasks like network traffic analysis to detect unusual requests or unknown devices connecting to a network.
Event management systems should be used to track application data in one centralized system and correlate patterns to highlight potential threats.
Finally, CISOs should regularly encourage team members to report suspicious emails, devices, or people loitering around their building. It does not matter how insignificant the threat may seem; being proactive is always the best course of action.
7. Focus on continuous improvement
It should be clear by now that cybersecurity is not a onetime event but rather an ongoing process to always stay at least one step ahead of the criminals. As new threats and lines of attack emerge, it is crucial that CISOs respond and educate employees on how to best respond to them.
There should be constant communication between the CISO and the wider team and regular meetings with the CEO and the board on potential new threats. Attending industry events and reading widely on cybersecurity news is essential to know of the evolving dangers.

Protect your organization by fostering a proactive cybersecurity culture
To wrap up, implementing a cybersecurity culture is paramount for organizations to protect the data of their customers, clients, and employees—and it is your CISOs who will see this to success.
Ignoring the risk of cyber-attacks is simply not an option. It could be disastrous for your company and destroy relationships with your customer base or even invite legal action. When the stakes are this high, employing a CIO or CISO is the obvious choice to preserve your business.









