Supply chain security activities aim to amplify the security of supply chains, transport, and logistic systems for the world’s cargo and to facilitate legitimate trading. Their objective is combining traditional practices of supply chain management with the security requirements driven by threats, such as; terrorism, piracy, and theft.
Digital supply chain security indicates the efforts towards the enhancement of cybersecurity within the supply chain. Supply chain cybersecurity is a subgroup of supply chain security, its focus is on the management of cybersecurity requirements for information technology systems, software, and networks, which are driven by threats such as; cyberattack, malware, data theft, and the advanced persistent threat (APT). Its most important aim is to defend against supply chain attacks and protect business assets within the supply chain.
A supply chain attack is not limited to certain industries, it can happen in all fields; from financials sectors, the oil industry, to bigger scales such as the government sector. It is a cyberattack that aims to damage an organization by targeting its less-secure components. Cybercriminals often meddle with the manufacturing process of a product by installing rootkits or hardware-based spying elements. A report by Argon an Aqua Security company states that supply chain attacks increased by 300% in 2021.
The Target security breach, Eastern European ATM malware, as well as the Stuxnet computer worm are examples of supply chain attacks.

The Proliferation of Supply Chain Cyberattacks
ENISA (European Union Agency for Cybersecurity) Threat Landscape for Supply Chain Attacks report published on July 29, 2021, aimed at mapping and studying the supply chain attacks that were discovered from January 2020 to early July 2021.
Based on the trends and patterns observed, supply chain attacks increased in number and sophistication in the year 2020 and this trend was expected to continue in 2021, posing an increasing risk for organizations. It was estimated that there will be four times more supply chain attacks in 2021 than in 2020. With half of the attacks being attributed to Advanced Persistence Threat (APT) actors, their complexity and resources greatly exceed the more common nontargeted attacks, and therefore there is an increasing need for new protective methods that incorporate suppliers in order to guarantee that organizations remain secure.
The report presented ENISA’s Threat Landscape concerning supply chain attacks, created with the support of the Ad- Hoc Working Group on Cyber Threat Landscapes. The main highlights of the report included the following:
- A taxonomy to classify supply chain attacks in order to better analyze them in a systematic manner and understand the way they manifest is described.
- 24 supply chain attacks were reported from January 2020 to early July 2021, and have been studied in the report.
- Around 50% of the attacks were attributed to wellknown APT groups by the security community.
- Around 42% of the analyzed attacks have not yet been attributed to a particular group.
- Around 62% of the attacks on customers took advantage of their trust in their supplier.
- In 62% of the cases, malware was the attack technique employed.
- When considering targeted assets, in 66% of the incidents attackers focused on the suppliers’ code in order to further compromise targeted customers.
- Around 58% of the supply chain attacks aimed at gaining access to data (predominantly customer data, including personal data and intellectual property) and around 16% at gaining access to people.
- Not all attacks should be denoted as supply chain attacks, but due to their nature, many of them are potential vectors for new supply chain attacks in the future.
- Organizations need to update their cybersecurity methodology with supply chain attacks in mind and to incorporate all their suppliers in their protection and security verification.
Key Risks of Supply Chain Cybersecurity
Supply chain cybersecurity risks cover a lot of territories. As stated on the National Institute of Standards and Technology some of the concerns include risks from:
- Third-party service providers or vendors, from janitorial services to software engineering, with physical or virtual access to information systems, software code, or Intellectual Property.
- Poor information security practices by lower-tier suppliers.
- Compromised software or hardware purchased from suppliers.
- Software security vulnerabilities in supply chain management or supplier systems.
- Counterfeit hardware or hardware with embedded malware.
- Third-party data storage or data aggregators.
Supply Chain Attack
The term supply chain alludes to the ecosystem of processes, people, organizations, and distributors involved in the creation and delivery of a final solution or product. When it comes to cybersecurity, the supply chain regards a multitude of resources (hardware and software), storage (cloud or local), distribution mechanisms (web applications, online stores), and management software.
There are four key elements in a supply chain:
- Supplier: is an entity that supplies a product or service to another entity.
- Supplier Assets: are valuable elements used by the supplier to produce the product or service.
- Customer: is the entity that consumes the product or service produced by the supplier.
- Customer Assets: are valuable elements owned by the target.
An entity can be individuals, groups of individuals, or organizations. Assets can be people, software, documents, finances, hardware, or others.
As mention on ENISA’s report: Supply chain attack is a combination of at least two attacks. The first attack is on a supplier that is then used to attack the target to gain access to its assets. The target can be the final customer or another supplier. Therefore, for an attack to be classified as a supply chain one, both the supplier and the customer have to be targeted.

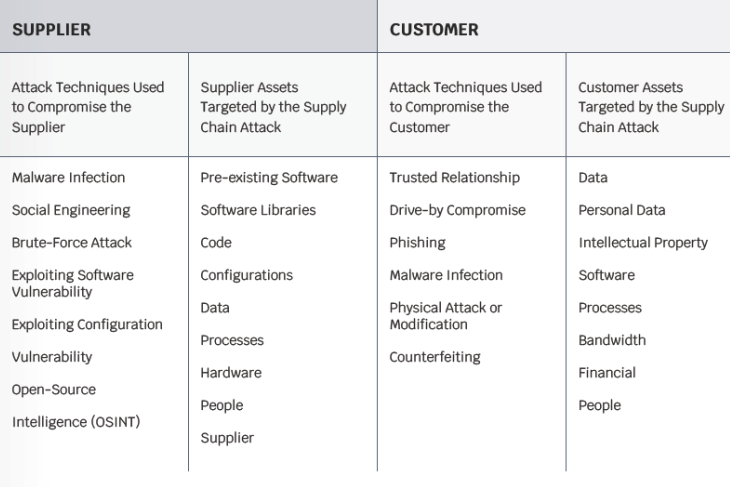
Attack Techniques, Targeted Supplier, and Customer Assets
The risk becomes evident when a vulnerability of an organization’s asset is utilized by a technique to attack or a threat, during this time, the evident risks begin to have a negative effect on the organizations’ assets.
Table: Proposed taxonomy for supply chain attacks. It has four parts:
- Attack techniques used on the supplier,
- Assets attacked in the supplier,
- Attack techniques used on the customer,
- Assets attacked in the customer.
Recommendations for How to Stay Resilient
As stated in an article published by SecurityMagazine: Thoughtful investment in cybersecurity measures goes beyond technology. Not only are digital tools and updated software important, but IT professionals are also essential in building resilient infrastructure.
Industries across the board that utilize cyberspace to any degree are at risk for cyberattacks, so understanding how to use technology and human expertise to both proactively prepare for and reactively combat against threats, is essential.
With experience, both good and bad, comes knowledge. One lesson learned in recent years is how interdependent each section of the global supply chain is on another. If one facility, port, software, or database is interrupted due to a cyberattack, countless companies and consumers can be impacted, resulting in great financial loss and compromised data. In fact, more than 30 billion records were exposed in data breaches just last year.
In an effort to avoid such attacks, individuals and organizations should keep in mind a handful of key steps to becoming more resilient and secure, and senior leadership needs to ensure that they and their team members feel confident in the systems and security they have in place.
On average, about 2,200 cyberattacks occur on a daily basis, so proactive planning is essential in limiting room for threats to come to fruition no matter the source, hence reducing the risks to a level accepted by organizations.

What Should Suppliers and Customers Do?
To manage supply chain cybersecurity risks, customers should:
- Identify and document types of suppliers and service providers
- Define risk criteria for different types of suppliers and services (e.g., important supplier and customer dependencies, critical software dependencies, single points of failure)
- Assess supply chain risks according to their own business continuity impact assessments and requirements
- Define measures for risk treatment based on good practices
- Monitor supply chain risks and threats, based on internal and external sources of information and on findings from suppliers’ performance monitoring and reviews
- Make their personnel aware of the risk
To manage the relationship to suppliers, customers should:
- Manage suppliers over the whole lifecycle of a product or service, including procedures to handle end-of-life products or components
- Classify assets and information that are shared with or accessible to suppliers, and define relevant procedures for their access and handling
- Define obligations of suppliers for the protection of the organization’s assets, for sharing of information, for audit rights, for business continuity, for personnel screening, and for the handling of incidents in terms of responsibilities, notification obligations, and procedures
- Define security requirements for the products and services acquired
- Include all these obligations and requirements in contracts; agree on rules for sub-contracting and potential cascading requirements
- Monitor service performance and perform routine security audits to verify adherence to cybersecurity requirements in agreements; this includes the handling of incidents, vulnerabilities, patches, security requirements, etc.,
- Receive assurance of suppliers and service providers that no hidden features or backdoors are knowingly included
- Ensure regulatory and legal requirements are considered
- Define processes to manage changes in supplier agreements, e.g., changes in tools, technologies.

On the other hand, suppliers should ensure the secure development of products and services that are consistent with commonly accepted security practices. Suppliers should:
- Ensure that the infrastructure used to design, develop, manufacture, and deliver products, components, and services is in accordance with cybersecurity practices
- Implement a product development, maintenance, and support process that is consistent with commonly accepted product development processes
- Implement a secure engineering process that is consistent with commonly accepted security practices
- Consider applicability of technical requirements based on product category and risks
- Offering Conformance Statements to customers for known standards, i.e. ISO/IEC 27001 (or specific ones like the CSA Cloud Controls Matrix (CCM) for cloud services), ensuring and attesting to, at the possible extent, the integrity and origin of open source software used within any portion of a product
- Define quality objectives, such as; the number of defects, externally identified vulnerabilities, or externally reported security issues, and use them as an instrument to improve overall quality
- Maintain accurate and up-to-date data on the origin of software code or components, and on controls applied to internal or third-party software components, tools, and services present in software development processes
- Perform regular audits to ensure that the above measures are met
Moreover, as any product or service is built from or based on components or a software that is subjected to vulnerabilities, suppliers should implement good practices for vulnerability management, as follows:
- The monitoring of security vulnerabilities reported by internal and external sources that include used thirdparty components
- The risk analysis of vulnerabilities by using a vulnerability scoring system (e.g. CVSS),
- The maintenance policies for the treatment of identified vulnerabilities depending on the risk
- The processes to inform customers
- The patch verification and testing to ensure that operational, safety, legal, and cybersecurity requirements are met and that the patch is compatible with non-built-in third-party components
- The processes for a secure patch delivery and documentation concerning patches to customers
- The participation in a vulnerability disclosure program that includes a reporting and disclosure process
Vulnerabilities should be managed by suppliers in the form of patches. Likewise, a customer should monitor the market for potential vulnerabilities or receive respective vulnerability notifications from their suppliers. Some good practices for patch management include:
- Maintaining an inventory of assets that includes patch-relevant information
- Using information resources to identify relevant technical vulnerabilities
- Evaluating the risks of identified vulnerabilities, as well as having a documented and implemented maintenance policy available
- Receiving patches only from legitimate sources and testing them before they are installed
- Applying alternative measures should a patch not be available or applicable
- Applying rollback procedures, effective backup, and restore processes.









