Implementing ISO/IEC 27001 in your organization entails that you formally document the scope of your Information system which means that you want to know the exact information that you want to protect and will be prepared to protect it. This way, you are keeping safe your organization’s information’s system by assessing and preventing threats such as ransomware attacks. 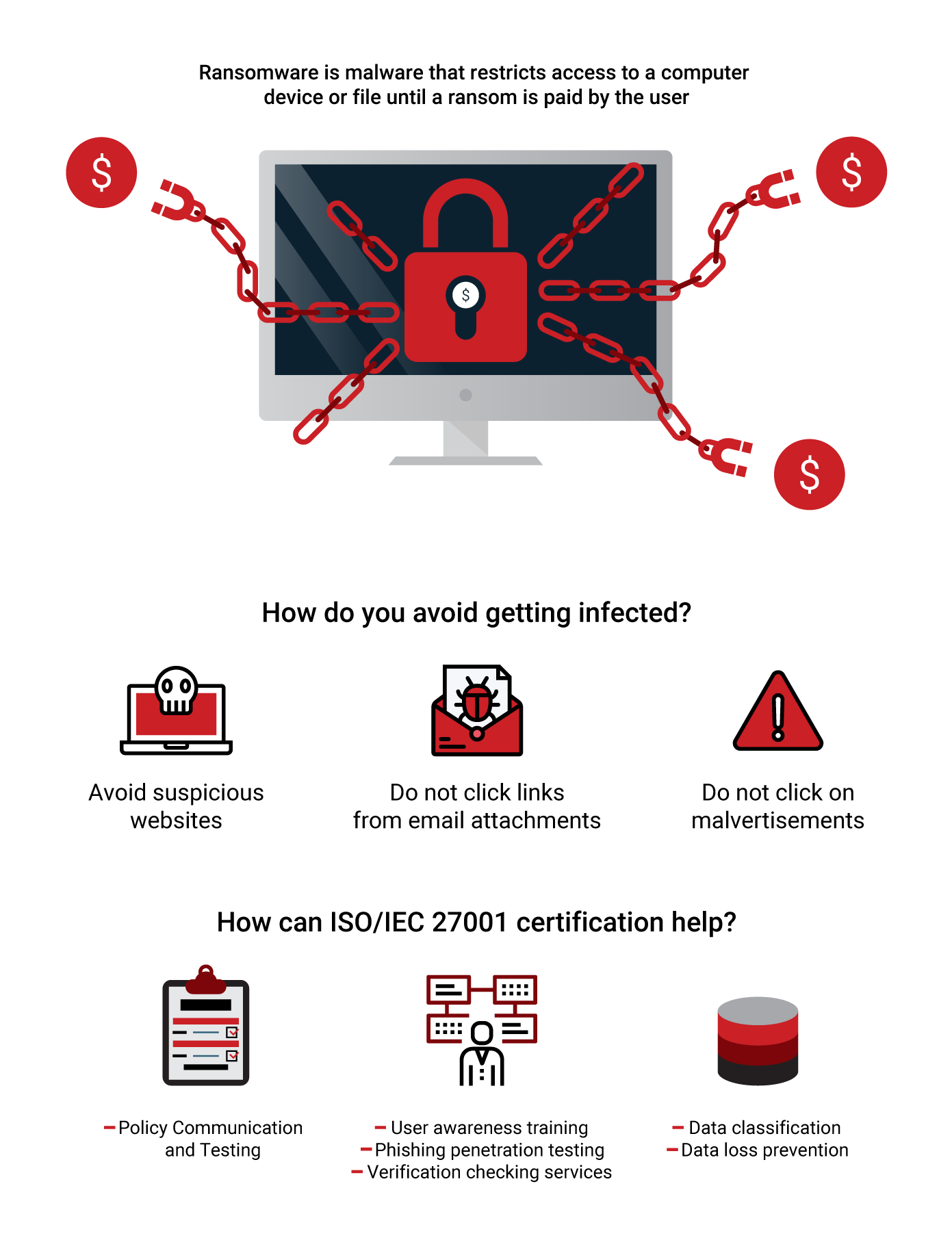
How dangerous is a ransomware attack?
A ransomware attack exposes vulnerabilities in user’s side, more specifically to their incorrectly configured systems such as browsers and their operating systems. This malware will potentially obstruct the clients’ entry into their records using encryption. If that occurs, the attackers will most likely request to be paid in order to unlock the infected computer. Thus, when we deal with a ransomware, once your files are encrypted, what you can do is to cut your losses or pay up to the hacker. These types of attacks are also classified as organized crimes which have evolved technologically, and most of the times large amounts of money are included. What users need to know is that it is not enough to install an antivirus in order to protect your operating system from these types of attacks. In spite of the fact that ransomware has been known as a technique for attack for quite a while, there are still no barriers that can 100% eliminate this attack. So, how can we be best prepared for these kinds of attacks? One of the best protections against this malware includes an arrangement of security layers where organizations ought to look towards technology, as well as individuals and process-like solutions. One of the most efficient ways to fight this sophisticated threat to our information system is the implementation of ISO/IEC 27001.
Why implementation of ISO 27001 is the best malware protection?
Implementing ISO/IEC 27001 means that your Information system is classified and is organized in such way that it makes it difficult for the attacker to infect the organization. Thus, being certified with ISO 27001, it means that the possibility of a ransom attack will be vastly minimized. Whilst applying ISO/IEC 27001, the part of the implementation which actually has the highest efficacy of detecting and preventing ransomware is a risk assessment. During the risk assessment process, organizations can identify risks and threats such as ransomware which may harm their operating system. If the identification procedure of malware is performed correctly, the process of their prevention/treatment becomes easier and more efficient. Moreover, the implementation of ISO/IEC 27001 in organization’s ISMS provides controls security layers that impede the exploitation of different weaknesses that each organization might have.
ISO 27001 Annex A controls include:
1. Control A.7.2.2 (Information Security alertness)
This section of the Information Security implementation is conducted for the sole reason of training the employees in the organizational rules, methodologies as well as procedures. If these kinds of awareness sessions are not held on a regular basis, the ransomware attacks would be a lot more dangerous because of the disorganized and untrained personnel. Some of the most regular ways in which these threats occur are attachments, spam e-mails, messages and so on.
2. Control A.12.4.1 (Event logging)
What this control tells us is that in view of the damage that the malware can do to our system, we should be able to create event logs and also conduct a regular review in order to detect the threat as earlier as possible.
3. Control A.12.3.1 (Information backup)
In view of the fact that the ransomware has the ability to spread in our network drives as well as our security copies, we should do regular tests to our backup copies to ensure that we are risk-free.
4. Control A.12.6.1 (Management of technical vulnerabilities)
This section exemplifies the importance of being aware of the exploits and vulnerabilities that our operating system has. This is crucial for our organization because when we are attentive of these vulnerabilities we can direct our attention towards finding best practices on how to protect and secure these flaws.
5. Control A.13.1.3 (Segregation in networks)
In this control, we are guided towards separating networks to protect the organization from malware threats. This means that if our network is separated into segments, the ransomware attack can be locked and controlled easily. To conclude, organizations that implement ISO/IEC 27001 seek to protect the confidentiality, integrity, of their customers’ information. The major reason why ISO/IEC 27001 certification is so efficient is because it does not only focus on IT controls, but also on the training of the personnel on how to operate in certain situations when they face suspicious threat attacks. Last but not least, ISO/IEC 27001 certification can lead to increased profits and reduced costs. Thus, in this case, it can reduce costs by preventing and assessing risks which may have a disastrous impact on the organization’s financial costs.
PECB
Surely, there are various incident costs which can be caused by malware that require a lot of financial measures to be taken in order to fix them. However, if an organization is ISO/IEC 27001 certified, incidents are assessed and prevented, which results in reduced costs. PECB provides training and certification services for ISO/IEC 27001 certification which can result in preventing and assessing malware such as ransomware attacks.









