Human survival has always depended on the ability to identify threats and react to them accordingly. Also, the whole process needs to be quick and cost-effective; the undertaken countermeasures shouldn’t require too much energy, resources or time. Otherwise, avoiding the threat or its consequences could become a pyrrhic victory.
The same rules apply to incident management within organizations. Companies may not implement a comprehensive Business Continuity Management System (BCMS), but they always have in place plans on how to respond to the most common or the deadliest threats. Some types of incidents – like cybersecurity threats – are required by law to be managed in a professional and standardized way.
Incident management is the beginning of the emergency response not only historically but also functionally. We tend to forget that every emergency response starts with incident management. Hence, it should not be an independent domain, detached from Business Continuity. It’s an integral part of resilience-building activities.
Incident management is still often managed in silos, which means that different business units manage different types of incidents: health & safety, physical security, cybersecurity, frauds, employee misconduct, product tampering, equipment malfunction, external service provider unavailability… the list goes on and on. The problem is that we may lose the perspective on all important interdependencies and in effect, also the consistency of the procedures. It is a good practice to apply a holistic approach to incident management. It improves information flow and escalation, allowing the crisis management team to contain the incident before it will develop into the full-blown disaster.

To make sure that our incident management strategy addresses the most probable incidents to which the company is exposed to, procedures should tackle risk assessment results. It means that for each identified threat, there is a dedicated procedure describing how to handle such an incident.
The risk assessment must be conducted with attention to detail. For our purposes, we need information on the threats which could cause unavailability of critical resources – employees, locations, external service providers, IT or DCS systems, manufacturing and logistics equipment. On top of that, we should scan for the risks which threaten the protective measures and supporting infrastructure (as their failure may result in an incident – i.e. failure of an air-conditioning system in a data center, power supply failure, telecommunication links, etc.).
With regards to the cybersecurity incidents, our risk analysis should focus on potential threats to each of the Information Security attributes: confidentiality, availability, integrity and in some cases authenticity as well.
The probability of such events is mainly of interest to the risk managers, who need to assess the risk and implement adequate controls. However, despite their best efforts, they will never be able to reduce the risk to zero. Therefore, the incident and crisis managers don’t analyze the chance of occurrence of the threat, but they rather focus on its potential impact, since their everyday job is to prepare responses to the events which usually are of low probability, but often of catastrophic consequences.
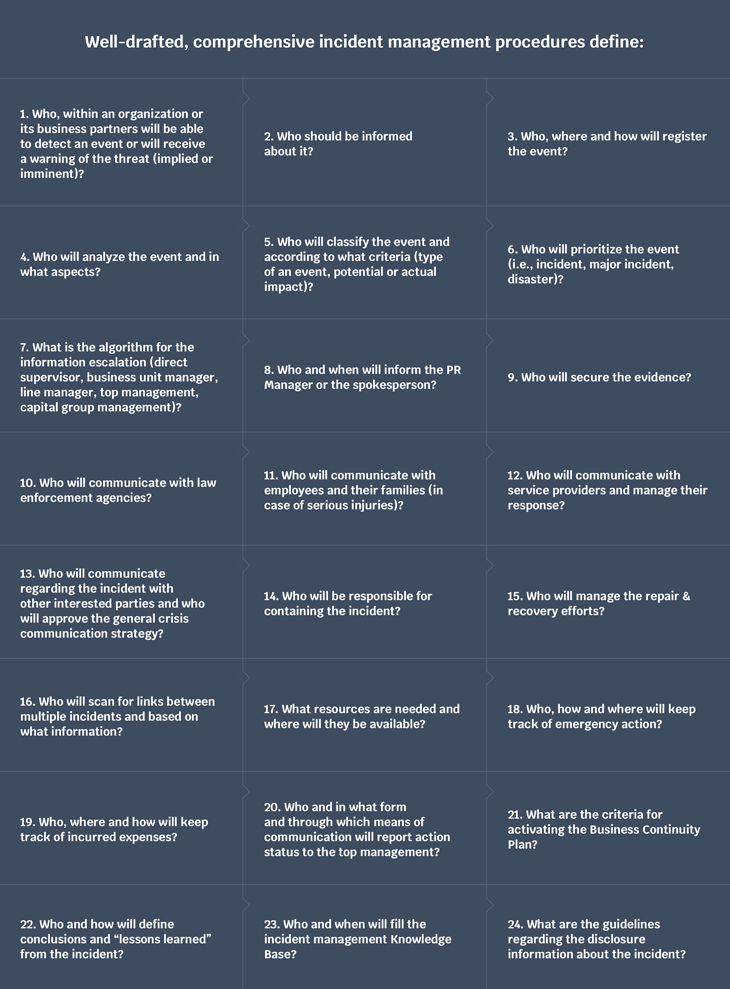
It is essential that there is a single, but interdisciplinary organizational structure, responsible for handling the incident and implementing the Business Continuity Plan. Therefore, the incident management team constitutes a part of the Crisis Management Team responsible for the overall Business Continuity response.
Incident management procedures and the results of the risk assessment are also the best sources of reference for composing the BCM exercise scenarios and inspiration for awareness training courses.
Then again, exercises provide us with suggestions for the additional measures worth implementing in incident management. For instance, incident management procedures often use the linear communication links, which cause the repetition of the same information over and over again – especially when we need to brief the next crisis team members joining the emergency action – spending valuable time and losing the momentum. One solution to this problem could be establishing a conference call at regular intervals, where everybody hears everything being said. The other idea is a written action log, accessible to all the members of the CMT, which helps the persons joining the conference call or a meeting to brief themselves, without interrupting the ongoing discussion
During an incident, people tend to react instinctively to danger. The crisis managers are often left with the difficult task to override the natural reaction and to assure people’s safety. A good example would be an evacuation procedure: the instinct tells people to run away from the danger at all cost and as fast as possible, but the procedure is designed to avoid panic – we need to follow an indicated route to the meeting point, which sometimes is longer than the shortest way outside. We shouldn’t run – we should instead take stairs and not use elevators, even if it takes more time to reach the exit. The procedure is critical but counterintuitive – that’s why it needs to be exercised frequently.
The incident management procedures and Business Continuity Plans are a very specific type of risk control mechanism. When every preventive measure fails, these are our last resorts: incident management and finally, the Business Continuity Management System.