What we refer to as Cyberspace is
Insider attacks – Typically initiated by employees or contractors who get access to a computer or network within an organization. It could be unintentional misuse or intentional abuse. Some examples of this kind of attack are: access to users’ password information by the authorized system administrator; using packet sniffer software; acting as middleman in non-protected Wi-Fi networks; using some malware that use the loose situation of a network interface of the infected computer in order to eavesdrop on traffic through the private network, etc.
Attacks from outside – There are different types of attack from outside the private network. They can be divided into:
- Attacks for financial purposes – It could be achieved by hackers as well as by different people who enable attack for others, such as distributed denial of service (DDoS). It is often used by organized criminal groups that blackmail an organization etc. For
these kind of attacks different methods and approaches could be used: port scanners, buffer overflows, IP Spoofing, botnet, phishing, etc. - Industrial spies – This category of attackers usually work on behalf of competitors and try to gather information such as production capacity, technologies involved and plant architecture. Also, it could be initiated by foreign governments to steal industrial secrets, disrupt production, exploit safety hazards, etc.
- Hacktivism – Hacking for a politically, socially or environmentally motivated purpose.

Due to the many possible threats, the most important challenge today is to preserve the confidentiality, integrity
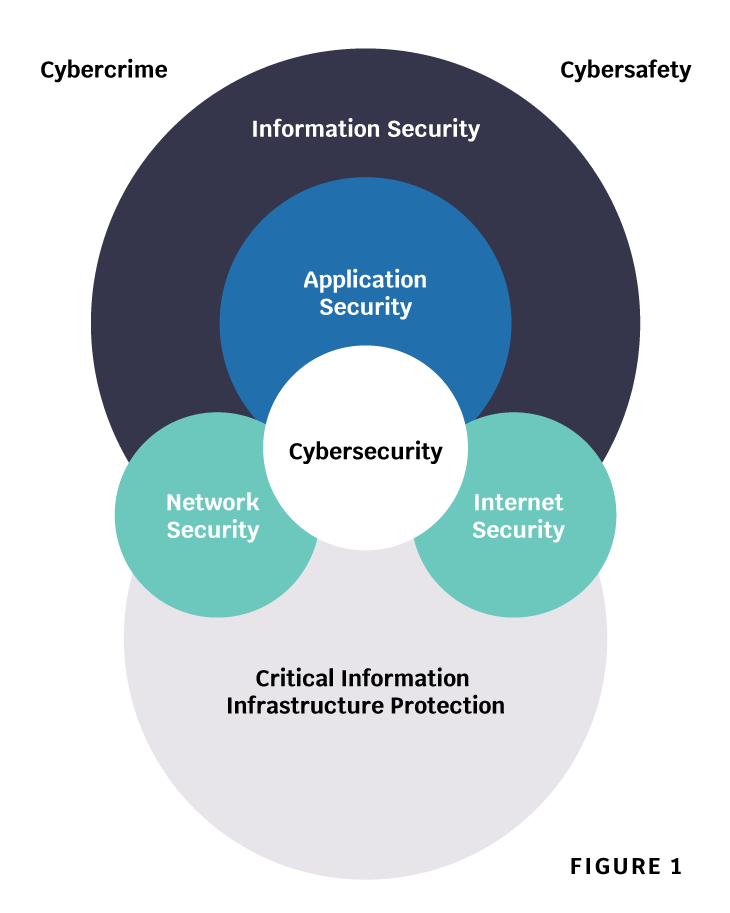
Cybersecurity is, however, not synonymous with Internet security, network security, application security, information security, or CIIP (Critical Information Infrastructures Protection). It has a unique scope requiring stakeholders to play an active role in order to maintain and improve the usefulness and trustworthiness of the Cyberspace (Figure 1).
Security technology has not kept pace with the rapid development of IT, leaving systems, data, and users vulnerable to both conventional and novel security threats. Cybersecurity standards improve security and contribute to risk management in numerous imperative ways.
Standards help in establishing common security requirements and the abilities necessary for fast responses and safe solutions. The importance of having a framework isn`t a question, however, which framework works best for the organization is something to be decided with caution because there are about 250 different security frameworks used globally, developed to suit a wide variety of businesses and sectors
- Develop cyber defense policies and capabilities
- Achieve cyber-resilience
- Reduce cybercrime
- Support industry on cybersecurity
- Secure critical information infrastructures
Published by the US National Institute of Standards and Technology in 2014, NIST Cybersecurity framework provides a common language for understanding, managing, and expressing cybersecurity risks both internally and externally. This is a tool that helps align business, policy, and technological approaches to manage the risk and it can be used in identifying and prioritizing actions for cybersecurity risks reduction. The framework is a risk-based approach to managing cybersecurity
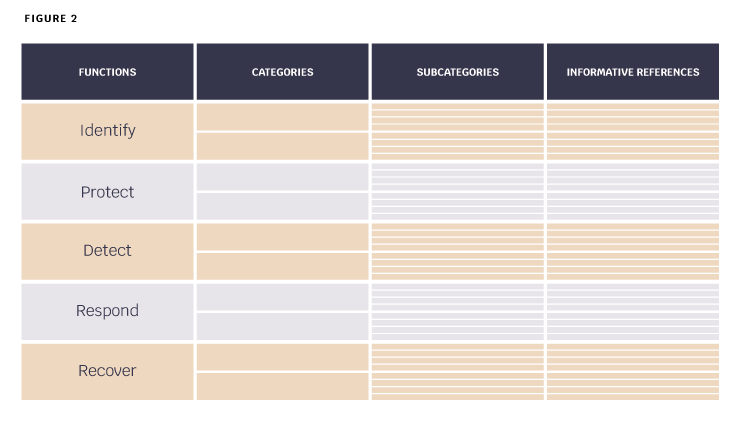
The Framework Core is a set of cybersecurity activities, anticipated results, and applicable references that are common over critical infrastructure sectors. The Framework Core comprises of five simultaneous and continuous functions – Identify, Protect, Detect, Respond, Recover. When taken together, these functions provide a high-level, tactical view of the lifecycle of an organization’s management of cybersecurity risks. Then for each function, it identifies main categories and subcategories and matches them with example Informative References such as existing guidelines, standards, and practices for each subcategory (Figure 2).
ISO/IEC 27001 could be used as a cornerstone of an Information Security Management System (ISMS) and expanded with ISO/IEC 27032 which is helpful in preventing potential cyber-attacks and protection in case of cyber incidents. The first step is the identification of all physical and virtual, personal and organizational assets. One of the main virtual assets is an individual consumer’s online identity.
Online identity is considered an asset since it is the key identifier for an individual consumer in the Cyberspace. Other individual consumer’s virtual assets include references in virtual worlds
In virtual worlds, members often use virtual avatars to represent or identify themselves or to act on their behalf. Often a virtual currency is used for virtual transactions. These avatars and currencies can be considered as assets belonging to an individual consumer. IT hardware and software, as well as personal digital devices or endpoints that allow a consumer to connect to and communicate in the Cyberspace, are also considered as assets in the context of this international standard. ISO/IEC 27001 could bring many benefits besides the fact that it comes with a higher cost of certification. It is accepted as a global benchmark for the effective management of information assets. On the other hand, a BCMS aligned with ISO 22301, will ensure that your Business Continuity Plan remains up to date and becomes part of the organization’s culture. It will support the efficient management of a BCMS and ensure the minimization of Business Continuity Management risks. But as it maps well into other frameworks it can be supplemented with other frameworks such as CIS Top 20 CSC, which is not as comprehensive as other frameworks but gets updated every 2 years.

Both NIST and ISO/IEC 27001 are technology-neutral, applicable to any type of organization, and both have the purpose of achieving business benefits while monitoring legal and regulatory requirements, and the requirements of all the interested parties. The biggest similarity is that both are based on risk management: meaning that they both require the safety measures to be executed only if cybersecurity risks were identified. The NIST Cybersecurity Framework is better when it comes to structuring the areas of security that are to be implemented and when it comes to defining exactly the security profiles that are to be achieved; ISO/IEC 27001 is better for making a full picture: for designing a system within which security can be managed in the long-term. The next and very important step is risk assessment that means identification and analysis of threats and vulnerabilities.
The results of risk assessment could be used for the determination and implementation of the appropriate cybersecurity measures. There are different kinds of cybersecurity controls, such as:
- Application-level controls
- Server protection controls
- End-user controls
- Controls against social engineering attacks
- Cybersecurity readiness
controls Other controls
Some examples of application level controls are:
- Display of short notices, which provide clear, concise one-page summaries of the policies
- Secure handling of sessions for Web applications (cookies)
- Secure input validation (prevention of SQL-Injection)
- Secure Web page scripting (prevention of Cross-site Scripting)
- Code security review and
testing Ensuring that the consumer can authenticate the service (subdomain, https credentials)
Also, it is very important that end users take certain security measures, such as:
- Use supported operating systems, with the most updated security patches installed
- Use anti-virus and anti-spyware tools
- Enable script blockers – accepting only the scripts from trusted sources
- Use phishing
filters Enable a personal firewall and HIDS Enable automated updates – ensure that systems are updated with the latest security patches whenever they are available
Cybersecurity frameworks provide organizations with useful templates to guide their cybersecurity efforts. By leveraging the work which has already been done to develop these frameworks, an organization can achieve a better improvement in cybersecurity more rapidly than would otherwise be possible for a given resource expenditure. Frameworks are available in varying degrees of focus