In cybersecurity, humans are often seen as the weakest link, as attackers use social engineering techniques to infiltrate organizations, so they can launch ransomware or cause a data breach. According to the ENISA Threat Landscape 2020, 84% of cyberattacks rely on social engineering.
So what can we do to protect against the human factor? Well, we all have a part to play in order to flip our role from being the weakest link, to becoming the strongest defense in our fight against cyberattacks.
NIST SP 800-63-3 defines social engineering as “the act of deceiving an individual into revealing sensitive information, obtaining unauthorized access, or committing fraud by associating with the individual to gain confidence and trust.” Attackers use different methods, tools, and tactics to deceive, ranging from spamming emails, to very personalized and targeted attacks on particular individuals.
Phishing attacks and social engineering may target anyone. As such, we need to be aware of the risks of such threats. If your social media is hacked, there could be a message sent to all your friends or contacts, from you, which includes a malicious link. To mitigate such risks, it is recommended to comply with strong password policies.

COVID-19 changed the theme of phishing emails, but not the methods. The attacks still preyed on human nature and psychology to manipulate individuals into doing something or revealing information that would compromise the security of their organization.
The types of malicious actors who use phishing techniques are opportunists and will adapt the attack for different situations, individuals, and current events.
What is phishing?
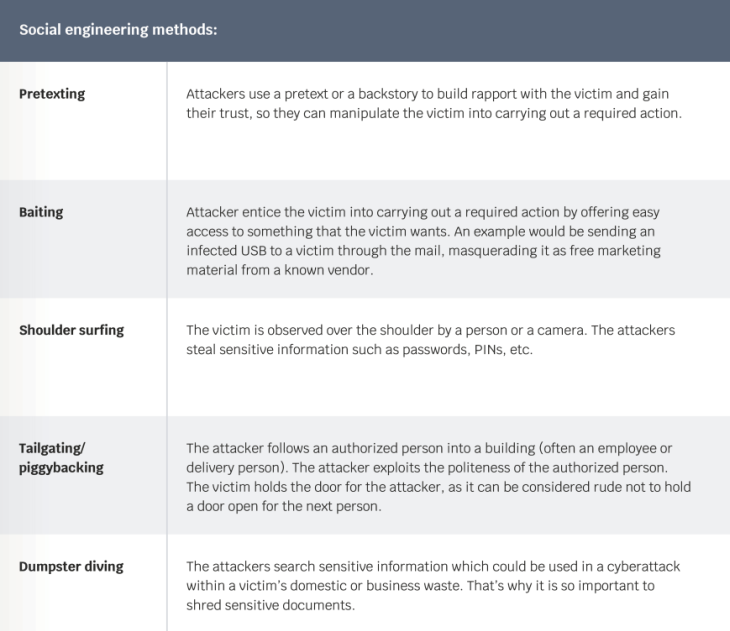
Phishing is a tactic to persuade victims to reveal sensitive information or carry out an action. Usually involves a combination of social engineering and deception. Attackers use different methods for phishing attacks, such as email, text, phone calls, URL redirects, and social media. Often these attackers await for the victim’s response so will communicate in real time often impersonating a person known to the victim.
An example of a phishing attempt is that convincing email from your energy service provider telling you that you will be cut off if you don’t pay in the next hour.
Other examples would be an SMS text message from a courier for an upcoming delivery, or even a phone call from your work IT Department asking if you recently changed your password. While social engineering and phishing attacks are getting more advanced and sophisticated, the good news is that there are certain flags we can look out for to protect ourselves.

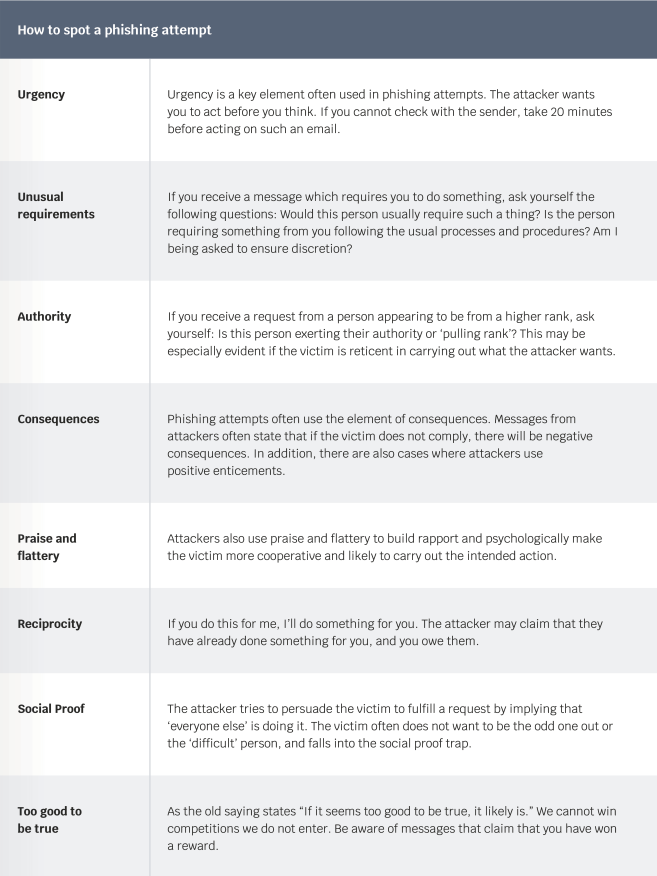
How to spot a phishing attempt
Most of us can identify the obvious bad spelling and outlandish stories, however, we recommend to trust your instinct too and look out for these red flags:
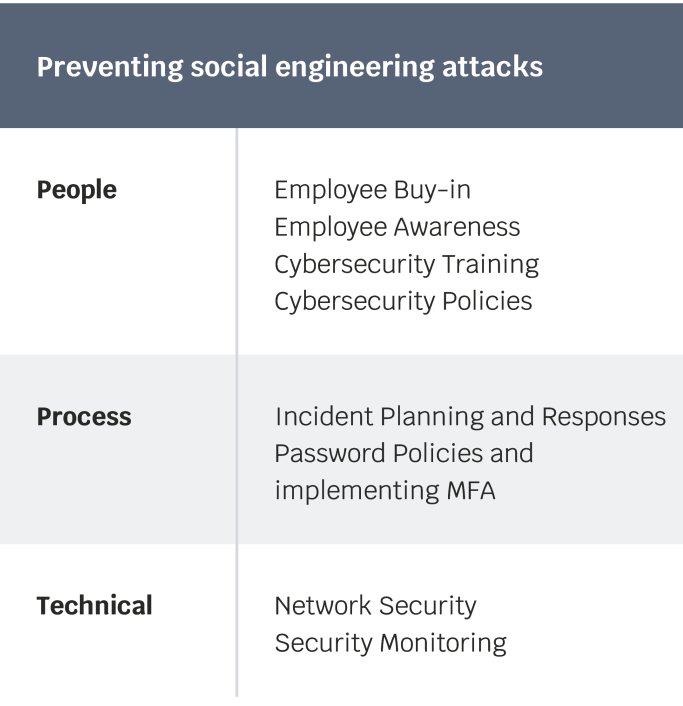
Preventing social engineering attacks
Preventing social engineering attacks requires a combined effort of people to implement processes and ensure technical support as much as possible. Implementing administrative, physical, and technical controls does not suffice, organizations must also fill in the gaps with training to raise the awareness of employees regarding social engineering attacks. The best social engineering attackers will manipulate humans to override the controls in place. As such, to prevent social engineering attacks, organizations must take preventive measures for the following:
Security Culture
In organizations, a security culture is one of the best methods of minimizing the impact of attacks and increasing your organization’s security posture. Maintaining a security culture in an organization means that cybersecurity is everyone’s problem, not just a problem of the IT team. While the CEO is ultimately responsible for the security of the organization, everyone within the organization or interacting with the organization can do their part. Make security awareness engaging and reward employees for doing the right thing regarding security.
Training and awareness
Regularly conduct relevant training and awareness sessions for everyone in the organization. Ensure your employees are cyber aware citizens, as attackers do not clock off at 5 p.m., so employees should be aware of cybersecurity risks even after they leave the organization.
Employees should be aware of phishing attacks and social engineering attempts that target them, but also the organization where they work. This ensures that individuals are cyber aware all the time and extend that awareness to their families and communities, which in turn, makes the whole society safer from cybercrime. There are resources from organizations such as the Cyber Readiness Institute which provides training regarding passwords, phishing, updates, and removable media. Such trainings can be an excellent starting point for employees on their cyber awareness journey.
No blame
There should be no negative consequences if an employee suspects that an email may be a phishing attempt and they make the call to verify. On the contrary, this practice should be encouraged and rewarded. Likewise, if a client is contacted to verify a change of bank account request, this should be seen as evidence of how seriously the organization takes the client’s business. If an employee does click on a malicious link, there should be no negative consequences, and it should be treated as a learning opportunity.

How can I support my team?
To become a cyber champion and reinforce cyber awareness training among your team, you do not need to hold a technical role. A passion for supporting your team and doing your part in your organization’s security culture is enough. Here are some suggestions to improve the awareness of your team regarding cybersecurity:
- Make yourself aware of your organization’s cyber incident response plans and ensure your team knows what to do in the event of an attack.
- Integrate cybersecurity on the agenda of all your team meetings.
- Encourage your team to stay up to date with current cyber news and incidents. Your National Cyber Security Centre will send a weekly email alert and offer you advice on dealing with incidents.
Conclusion
Social engineering is an enduring attack vector and it will continue to be exploited as long as it remains a successful tactic for cyber attackers.
The role of the human factor is that we all have a part to play in ensuring that attackers do not use our human nature against us to obtain information and use it for malicious purposes. Rather than seeing the employees as the weakest link which attackers exploit, we need to flip that, and the employees the strongest link.
Through trainings and awareness sessions, organizations must prepare their employees on how to deal with cybersecurity issues, as they are often the first line of defense when facing cyberattacks. With constant support, a security culture, and training, employees will get more adept at recognizing, impeding, and preventing social engineering attempts of malicious actors, thus maintaining the security posture of their organization.