Finding the “bad guys” sooner has never been more important.
Historical Perspective
To understand the need for the next generation in breach detection, we should go back just a few years. In 2013, very few governments or businesses put much discussion into cybersecurity other than putting anti-viruses on their computers and getting a dedicated firewall on the company network at the advice of their IT department. AV and a first-generation firewall should be more than adequate for a layered defense. What was hidden until late 2013 was the massive Target breach and some sobering statistics from an annual Verizon Data Breach Investigation Report. In that report, there were a few statistics which point to the need for breach detection in a serious way. The breach is only detected by corporate internal IT staff 6% of the time. A breach goes undetected for an average of 210 days. The time to hack into a corporate network, in 75% of the cases, took under 15 minutes. Is it any wonder that breach detection has not been promoted more aggressively by cybersecurity experts?
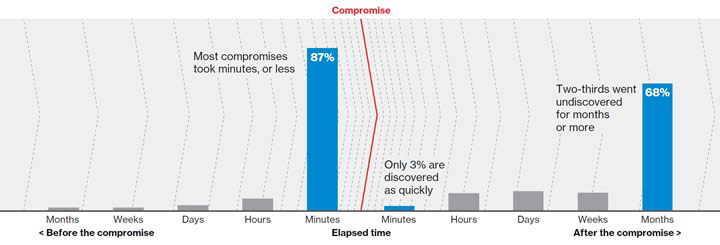
Fast forward to 2020. We have had 7 years to better perfect our detection, right? Well, the criminals have had 7 years to find much more sneaky ways to hide on our computer networks. The stats bear out who is winning the war of attrition. In 2020, the average days to detect a breach have decreased only 4 days in 7 years, to 206 days. The costs of breaches have increased steadily over the last 2 decades, so it is inevitable that breach detection needs to step up to the next generation to counter the hackers. Although the graphic presented below is from the 2018 Verizon Data Breach Investigations Report, it graphically shows the battle we have at hand.
Current Breach Detection Methodology
There are several technologies in use now that should reduce dwell times for hackers on government or corporate network systems. Most of these have been around quite some time, particularly in enterprise environments.
One such technology is known as an SIEM (Security Information and Event Management). Don’t ask me the proper pronunciation of the acronym as no matter how I say it, I am immediately corrected by the nearest systems engineer. The idea is quite sound, gather in all the logged actions taking place on every PC, networked device, and server in the environment, and review them by a security professional every single day. Given that there are literally millions of actions recorded in the logs every day, this is quite a daunting task.
This is where the SIEM tool comes into play. Parse down the meaningless actions (at least as far as finding a hacker in the environment is concerned) and allow the security professional to review only about a dozen of actions that should be investigated. The problem is that there’s no Red Alert Deflector Screen that pops on to protect your network. We will have to wait until the 24th century for this, I’m sure. (Geeky Star Trek reference) If you only have a single professional tasked with reviewing these actions, they will quickly get fatigued with tracking down false positive alerts. There are also vacations, sick days, and a myriad of other reasons this task is nearly impossible for a single person. A Security Operations Center (SOC) monitoring an SIEM is almost always desirable. The cost of an SOC & SIEM combination has made this option costprohibitive in the past, but given the rise in cybercrime and the detrimental effects after a breach, the cost may well make much more sense in the Boardroom and Government offices.
Next Step to the Next Generation
The business problem becomes how to reduce the cost of this very labor-intensive process and at the same time increase finding the elusive hacker while diminishing false positives that take time away from real threats. Just as Ransomware was a brilliant leap forward for criminal organizations to use instead of just adding more hackers, the solution is automation. Through machine learning and artificial intelligence, the machine can be trained to see certain patterns which MUST take place for a hacker to plant his flag inside a network. They need to keep some way to regain access to the same corporate network. Even if the attack is automated itself, through AI or scripted, the fact remains that the human hacker will need future access. The hacker will also need time to perform reconnaissance on what level of access they have, where they can travel within the network, and most importantly, how to increase their authority to have full access to all data, both on premise and in the cloud.

New vendors are taking advantage of this machine learning and creating agents for PCs that are similar to SIEMs, but which are specific to looking for the hidden hacker on your network. They often have an SOC behind them to perform the analysis and investigations needed to determine if an anomaly is a real threat or simply a false positive. The cost is significantly reduced since they are only looking for that needle in the haystack and not pins, thimbles, and other pieces of thread to go into the needle.
One More Security Tool, Is It Really Worth It?
For full transparency, I should admit we use two different breach detection tools working within our internal network. So, obviously, I believe they are worth the investment. But let’s look at it just based on the evidence at hand. Given the statistics of the hidden hacker threat, is there a reason as to why it isn’t worth it? Enterprise level breach detection does not have a small price tag, but neither does the cost if you really have a breach and the hacker has 6 months to go through your entire network. That single action could put your business out of business.
When I perform vulnerability assessments, the largest gap I see is the lack of serious security awareness training, but followed right behind it is no breach Detection at all. So, yes, I believe it is well worth the investment with today’s Advanced Persistent Threat. I would not use these tools without the experts in the SOC. These folks work 24/7 and understand the threats intimately. Without the proper expertise in interpreting the data, the value is lost.
Are these tools perfect? No, but this is one layer of protection that has been missing from way too many networks, both government and corporate. This is the tool IT doesn’t even know they need, YET.
Conclusion – There’s No Silver Bullet
No matter what defenses we create or how diligent we are at doing all the little things associated with a defense in depth, we will get outsmarted sooner or later. The SolarWinds Orion debacle should be the best example of this. When I give presentations on cybersecurity, I often use the analogy of a thief breaking into your home. Given enough desire and tools, no matter your defenses, the determined thief will gain access to your house. The best approach is to better protect your critical data, focus on its defense, and understand you are going to lose the battle elsewhere. Just don’t lose the war.









