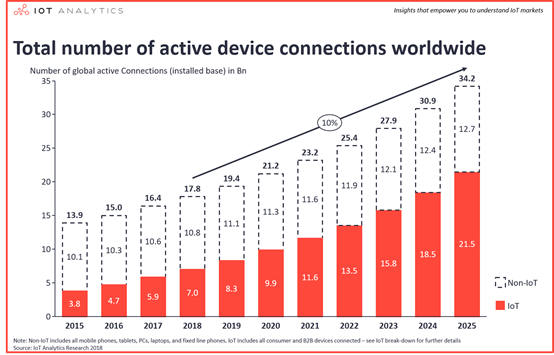
In today’s world, where our daily life is surrounded by smart devices, wearable electronics, IoT, and smart phones, cyber threats are always there (see Figure 1). Moreover, at the corporate level it has become something very normal to find the majority of the organizations depending on cloud solution which is usually hosted and/ or operated by a third party. This, however, represents a lack of governance and may also involve weak controls, which is why both individuals and organizations are facing a very wide attack surface along with tens of attack vectors. All these technological advancements with their connected risks and threats highlighted the sudden need and importance of ethical hackers as the first line of defense. They are working proactively to detect vulnerabilities that could exist in networks, operating systems, applications, middleware, databases, physical controls, and even human factors which often represent the weakest link in the chain.
Who Is the Ethical Hacker?
An ethical hacker, also referred to as a white hat hacker, is an information security expert who attempts to penetrate a computer system, network, application, or other computing assets in a legal way (with the owner’s permission and in accordance to a predefined scope) to find security vulnerabilities that a malicious hacker could potentially exploit. With different wording, we can say that it is a simulation of an attack for a defensive purpose.
Cyberwarfare/cyber operation also has a great impact on the exponential increase on the demand of ethical hackers. During the last ten years, tens of countries including the United States, Germany, the United Kingdom, China, France, Iran, and many more have announced that they started to establish their “Cyber Army.” This was mainly to protect their national security, critical infrastructure, and confidential data against cyberattacks that could be initiated from other countries (Nation Sponsored Attacks), organized criminals or cyber terrorists. In addition, in some countries like Germany they restructured the armed forces to include a sixth branch in the German military; the new branch includes 13,500 “Cyber Soldiers.”

Cyber operations with both offensive and defensive targets became a necessity for all modern armies. However, based on the context of this article, I will ignore the offensive side since it is not relevant to our topic here. Cyber operations’ importance will increase greatly with the release of 5G technology M2M (Machine to Machine) since billions of devices will be connected together, representing the widest ever attack surface. With the 5G technology, almost everything will be connected to the internet with hundreds of embedded systems and vendor-specific applications where control will be indeed very difficult.
Last but not the least, ethical hacking and penetration testing are necessary to achieve a wide range of certification for organizations in general or for some specific sectors, such as ISO/IEC 27001 (Information Security Management System), PCI (Payment Card Industry Standards), HIPAA (Health Insurance Portability and Accountability Act), or maybe some regulatory requirements such as GDPR (General Data Protection Regulations) where it is a must for every organization to conduct vulnerability assessment or penetration testing at least once a year.
Vulnerability Assessment versus Penetration Testing
Vulnerability assessments search systems for known vulnerabilities, while penetration testing attempts to actively exploit weaknesses — we could say that it is about checking the exploitability of the detected vulnerabilities. While a vulnerability scan can be automated, a combination of automated and manual techniques is usually utilized in conducting a penetration test where it requires a more advanced level of expertise along with a proper planning and risk assessment. Unprofessional penetration testing could result in service failure or complete denial of service.
Ethical Hackers or Penetration Testers’ Skills
According to NICCS (National Initiative for Cybersecurity Careers and Studies) and NICE (National Initiative for Cyber Education) the following KSAs (Knowledge, Skills, and Abilities) and tasks are needed for those who will conduct vulnerability assessment (Ethical Hackers and Penetration Testers)

ABILITIES
- A0001: Ability to identify systemic security issues based on the analysis of vulnerability and configuration data
- A0044: Ability to apply programming language structures (e.g., source code review) and logic
- A0120: Ability to share meaningful insights about the context of an organization’s threat environment that improve its risk management posture
- A0123: Ability to apply cybersecurity and privacy principles to organizational requirements (relevant to confidentiality, integrity, availability, authentication, non-repudiation)
KNOWLEDGE
- K0001: Knowledge of computer-networking concepts and protocols, and network security methodologies
- K0002: Knowledge of risk management processes (e.g., methods for assessing and mitigating risk)
- K0003: Knowledge of laws, regulations, policies, and ethics as they relate to cybersecurity and privacy
- K0004: Knowledge of cybersecurity and privacy principles
- K0005: Knowledge of cyber threats and vulnerabilities
- K0006: Knowledge of specific operational impacts of cybersecurity lapses
- K0009: Knowledge of application vulnerabilities
- K0019: Knowledge of cryptography and cryptographic key management concepts
- K0021: Knowledge of data backup and recovery
- K0033: Knowledge of host/network access control mechanisms (e.g., access control list, capabilities lists)
- K0044: Knowledge of cybersecurity and privacy principles and organizational requirements (relevant to confidentiality, integrity, availability, authentication, non-repudiation)
- K0056: Knowledge of network access, identity, and access management (e.g., public key infrastructure, Oauth, OpenID, SAML, SPML)
- K0061: Knowledge of how traffic flows across the network (e.g., Transmission Control Protocol [TCP] and Internet Protocol [IP], Open System Interconnection Model [OSI], Information Technology Infrastructure Library, current version [ITIL])
- K0068: Knowledge of programming language structures and logic
- K0070: Knowledge of system and application security threats and vulnerabilities (e.g., buffer overflow, mobile code, cross-site scripting, Procedural Language/Structured Query Language [PL/SQL] and injections, race conditions, covert channel, replay, return-oriented attacks, malicious code)
- K0089: Knowledge of systems diagnostic tools and fault identification techniques
- K0106: Knowledge of what constitutes a network attack and a network attack’s relationship to both threats and vulnerabilities
- K0139: Knowledge of interpreted and compiled computer languages K0161: Knowledge of different classes of attacks (e.g., passive, active, insider, close-in, distribution attacks)
- K0162: Knowledge of cyberattackers (e.g., script kiddies, insider threat, non-nation state sponsored, and nation sponsored)
- K0167: Knowledge of system administration, network, and operating system hardening techniques
- K0177: Knowledge of cyberattack stages (e.g., reconnaissance, scanning, enumeration, gaining access, escalation of privileges, maintaining access, network exploitation, covering tracks)
- K0179: Knowledge of network security architecture concepts including topology, protocols, components, and principles (e.g., application of defense-in-depth)
- K0203: Knowledge of security models (e.g., Bell- LaPadula model, Biba integrity model, Clark-Wilson integrity model)
- K0206: Knowledge of ethical hacking principles and techniques
- K0210: Knowledge of data backup and restoration concepts
- K0224: Knowledge of system administration concepts for operating systems such as but not limited to Unix/ Linux, IOS, Android, and Windows operating systems
- K0265: Knowledge of infrastructure supporting information technology (IT) for safety, performance, and reliability
- K0287: Knowledge of an organization’s information classification program and procedures for information compromise
- K0301: Knowledge of packet-level analysis using appropriate tools (e.g., Wireshark, tcpdump)
- K0308: Knowledge of cryptology
- K0332: Knowledge of network protocols such as TCP/ IP, Dynamic Host Configuration, Domain Name System (DNS), and directory services
- K0342: Knowledge of penetration testing principles, tools, and techniques
- K0344: Knowledge of an organization’s threat environment
- K0624: Knowledge of Application Security Risks (e.g., Open Web Application Security Project Top 10 list)

TASKS
- T0010: Analyze organization’s cyber defense policies and configurations and evaluate compliance with regulations and organizational directives
- T0028: Conduct and/or support authorized penetration testing on enterprise network assets
- T0138: Maintain deployable cyber defense audit toolkit (e.g., specialized cyber defense software and hardware) to support cyber defense audit missions
- T0142: Maintain knowledge of applicable cyber defense policies, regulations, and compliance documents specifically related to cyber defense auditing
- T0188: Prepare audit reports that identify technical and procedural findings, and provide recommended remediation strategies or solutions
- T0252: Conduct required reviews as appropriate within environment (e.g., Technical Surveillance, Countermeasure Reviews [TSCM], TEMPEST countermeasure reviews)
- T0549: Perform technical (evaluation of technology) and nontechnical (evaluation of people and operations) risk and vulnerability assessments of relevant technology focus areas (e.g., local computing environment, network and infrastructure, enclave boundary, supporting infrastructure, and applications)
- T0550: Make recommendations regarding the selection of cost-effective security controls to mitigate risk (e.g., protection of information, systems and processes)
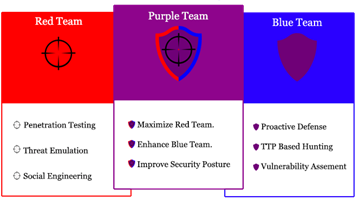
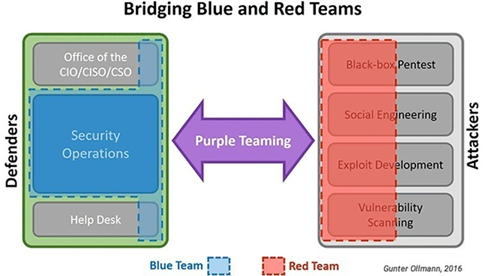
Blue Team, Red Team, or Purple Team?
Although it is obviously clear that ethical hackers, pen testers, or even malicious hackers share a very wide and common portion of knowledge and skills, they do have quite different mindsets and objectives. This is why, practically speaking, we have different teams of ethical hackers who can, for instance, work separately or coordinate to continuously detect weaknesses and improve the security posture of the organization.
Blue team: It is an internal security team that defends against attackers. Blue team works proactively to protect the organization and defend against cybersecurity threats. It performs full-knowledge assessments of networks, systems, and applications looking for security weaknesses. It could be an internal or external (outsourced) team.
Red team: It performs no-knowledge simulations of an attack against the organization’s assets with specific objectives in mind. It is sometimes staffed by people who normally work for the organization. Usually, it is authorized by the Chief Executive without notification to others within the organization (blind test/double blind test)
Purple team: It is known as the conceptual team (not a must to be a physical team). Its mindset is more towards coordinating and managing a shared goal involving red and blue teams. These coordinated joint activities improve the effectiveness of security controls, testing methodologies, and the organization’s overall security posture.
The world is witnessing a very high shortage in ethical hackers. According to many statistics, we have around two million vacancies in cybersecurity in general where ethical hackers/cybersecurity engineers are identified as one of the five most in-demand cybersecurity jobs for 2020 with an average of yearly salary of $106,000.
Related NICE Work Role IDs: PR-INF001, SP-SYS001
Another survey from ISC(2), an international, nonprofit membership association for information security leaders, produced a research in 2018 which estimated the cyber worker shortage at nearly 3 million — on the heels of a report they put out just a year earlier, which stated a drastically lower 1.8 million figure by 2022. By no means, the main concern when hiring ethical hackers is their qualification and practical skills.
However, well-educated and certified ethical hackers who have deep understanding of the technical and scientific concepts are representing an additional value and competitive edge for organizations from the credibility point of view. Some security guys may have great skills in one or more specific areas, but when it comes to the business perspective, this may represent a very high risk if the ethical hacker does not have sufficient knowledge, that could lead to a big problem.
To put it simply, this is the difference between a professional pen tester and a script kiddie who is using hacking tools. The latter may accidentally launch an actual attack without knowing what is happening at the underlying layer, conducting a destructive test without understanding the impact on the business or the service dependencies model which could lead to denial of service or system failure. It is also worth to mention that the different teams (red, blue, and purple) mentioned earlier, need to be connected or have joint activities and shared knowledge base with other teams such as, but not limited to, Forensics Investigators, incident handlers, or SOC (Security Operations Center) engineers.
Security has to be handled in a holistic way in order to oversee the big picture. In other words, if you have a secure operating system and a secure database in addition to secure applications, this will not, by default, lead to having a secure system since some vulnerabilities will not appear until you connect things together. My last advice for everyone is to always work in all pillars of successful security systems which are (people, process, and technology). In my humble opinion, the “People” component has a great impact on the other two.









