In 2016, data breaches remain one of the most significant challenges facing law firms and government agencies. Cybercriminals target law firms and government agencies due to the value of the intellectual property and sensitive information that they maintain.
Since 2013, for the industries being tracked, approximately five (5) billion data records have been reported as either lost or stolen. Of this amount, over 14% of breaches were government related. The reality, however, is likely much higher since the Breach Level Index only tracks publicly disclosed breaches. Unfortunately, law firms are not tracked since this information is not public.
In assessing the impact and likelihood of the related risks, people are considered the wild card due to their unpredictable behavior in complying with security policies. They are the weakest link in security compliance and pose one of the most difficult challenges faced by cybersecurity professionals and easiest target of hackers. The malicious employee, whether motivated by money, hatred, or both, is one of the most difficult challenges faced by cybersecurity professionals.
Evidently, a technical cyber solution can be implemented, such as a security information and event management (SIEM) process. However, without sufficient training, incidents can occur and not be detected on a timely basis. One survey cited that on average, it takes 206 days to detect a cybersecurity event and respond. People must know how to detect and respond to cybersecurity incidents on a timely basis.
Although cyberattacks continue to grow, in 2016, law firms have not placed a major business priority on managing cybersecurity. This is alarming since the significant financial and reputational damage resulting from a hack can impact law firms, client-attorney relationships, political and judicial systems.
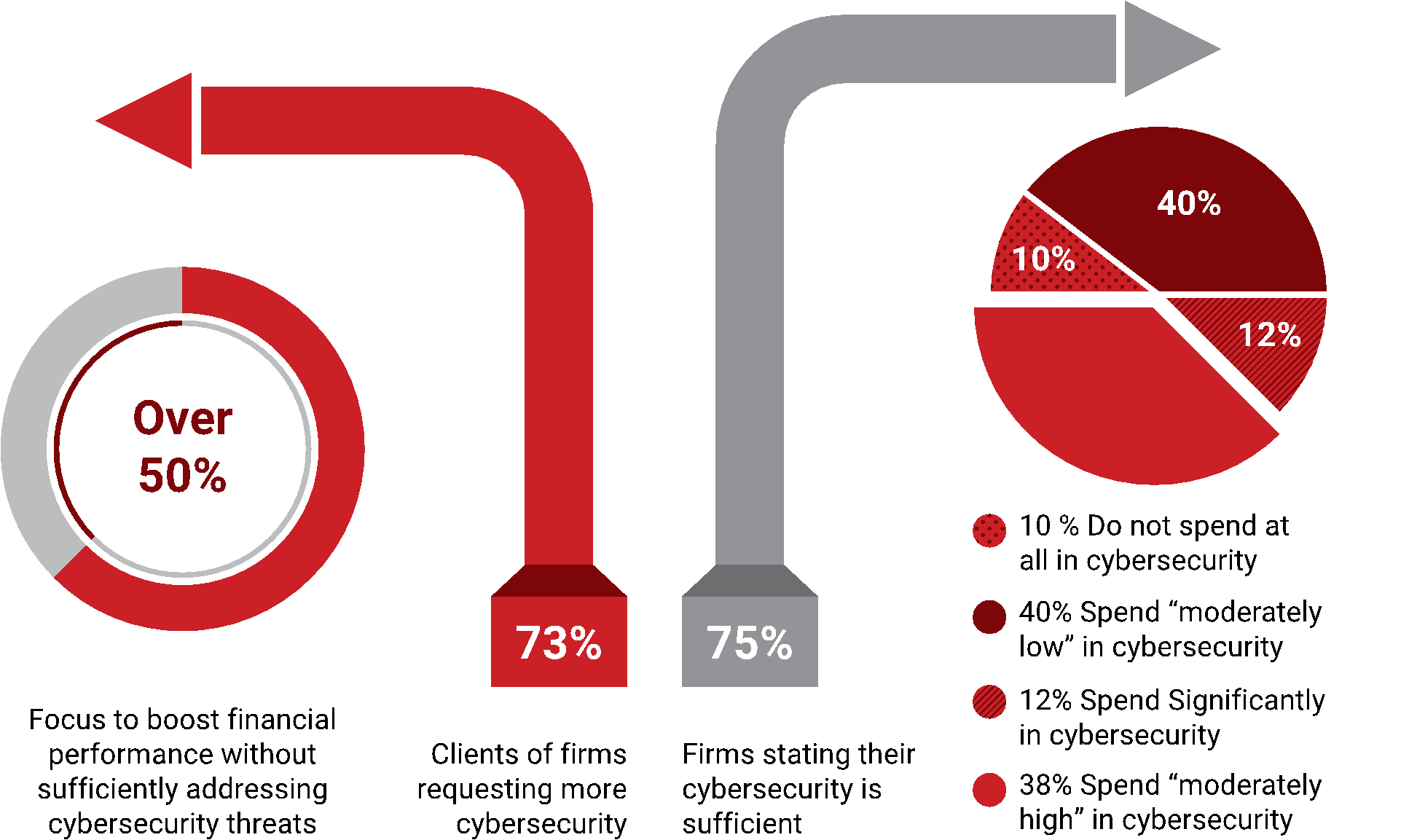
A recent survey of law firms and legal professionals cited that over 50% of the 800 law firms surveyed stated that they were continuously focused on bolstering their financial bottom line and operations without sufficiently addressing cybersecurity threats. In fact, law firms continue to lag behind in funding their cybersecurity programs. The survey found that 10 % of firms did not spend any of their budgets on cybersecurity, while 40 % described their cybersecurity budget as “moderate” compared to 12 % describing their cybersecurity investment as “significant”.
The survey also revealed that despite 73% of firms receiving demands from clients to boost their cybersecurity, over 75 % of law firms are confident that their cybersecurity procedures are sufficient. The fact is that most failed to create and test a cybersecurity incident response plan, or have an unqualified audit opinion on security, or do not have security certification by a professionally accredited certification body such as PECB.
Despite the survey, recently the USA Department of Justice (DOJ) mentioned instances of insider trading based on the hacking of law firms. One example is that three Chinese hackers have been charged in the USA with insider trading after stealing confidential trade information on proposed mergers and acquisitions from American law firms. With this information, the group bought shares in the target businesses and made approximately $4 million in illegal profits.
Governments are moving in the right direction. Recently, New York State proposed a regulation effective March 1st, 2017, stating that financial institutions must establish a program capable of ensuring the confidentiality and integrity of its information systems. This is a complementary to the existing U.S. Government requirement, which states that all federal agencies must develop and adhere to cybersecurity policies and practices which address the following minimum requirements.
Starting with, identifying internal and external cyber risks as well as using a defensive infrastructure is marked as an initial requirement. Additionally, organizations are required to implement a cyber security policy to protect nonpublic information from unauthorized access. Also, they will need to detect and respond to cybersecurity events while ensuring the resumption of normal operations following such events. Further, developing written procedures to assess and test the security of externally developed applications is yet another prerequisite; followed by establishing risk-based policies, procedures and controls to monitor the activity of authorized users and detect unauthorized access. A timely destruction of personal data lines up here as well. Competent staff and the employment of a CISO (Chief Information Security Officer) to implement and control cybersecurity policies is a requirement.
To provide an in-depth defense, ISO\IEC frameworks can be used as a tool to identify vulnerabilities, and threats using a risk-based approach. Cybersecurity controls have been defined and can be utilized. The ISO\IEC frameworks emphasize that cybersecurity is a business risk and not just an IT risk.
In summary, the need for an effective cybersecurity strategy continues to be important in order to achieve success. ISO\IEC frameworks are here and can help.
PECB
Complying with cybersecurity policies will not only continue to be a necessity at the state level but will also benefit the organization and protect their network and information Security. Thus implementing ISO/IEC frameworks; relevant to cybersecurity will greatly aid organizations to achieve such prerequisites. As a global provider of training, examination, audit, and certification services, PECB offers its expertise in multiple fields, including ISO/IEC 27000 Information Security training courses.