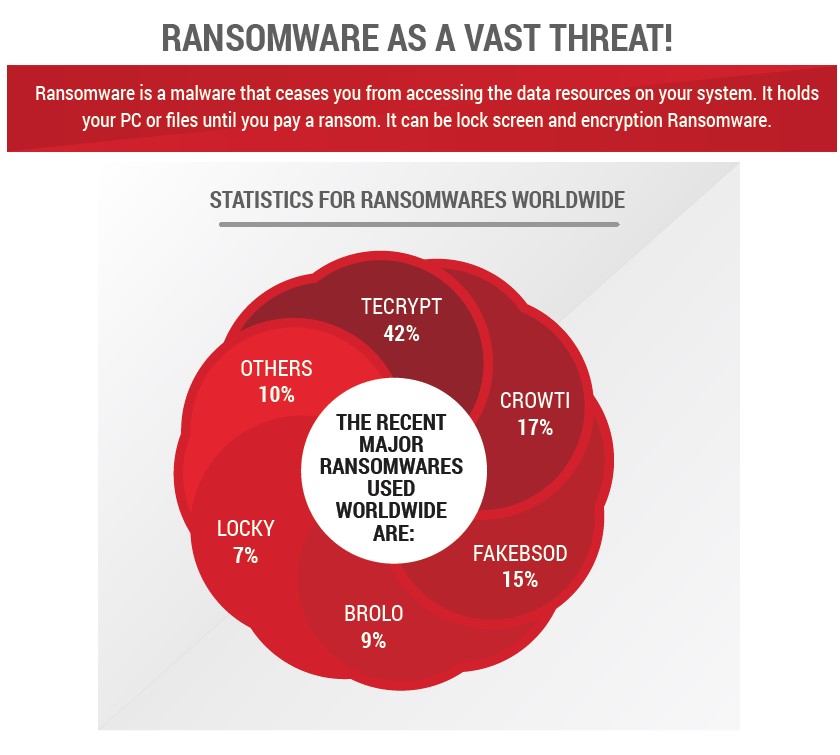
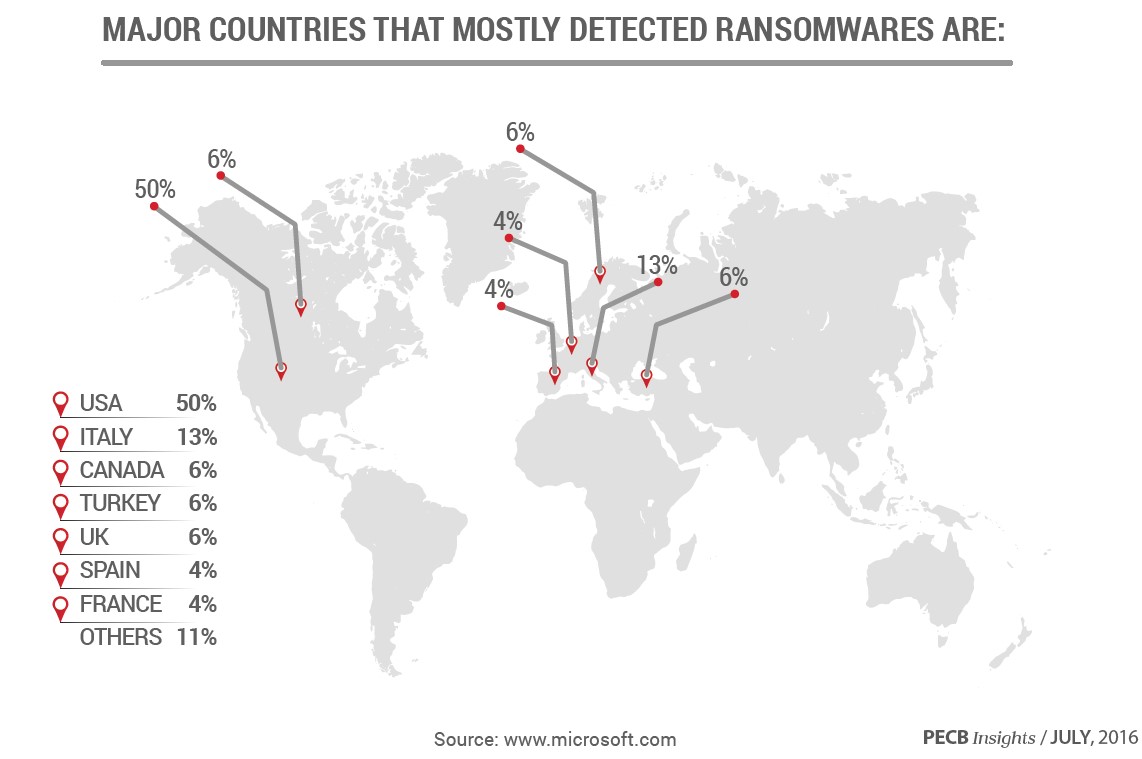
Recent reports have shown that many companies and institutions pay a ransom in order to regain access to their data. Citizens all around the world could find themselves in the same kind of situation. It is widely known that attacks are not only about gaining access to information for any specific purpose, but also about limiting data usage. This is a quite sophisticated process and intruders are using it wisely.
What is RANSOMWARE?
Ransomware is a type of malware that propagates through networks and infects the computer systems with the intention to restrict data usage by encrypting files of any kind. Once the files are encrypted, it will communicate to the victims that they have to pay a ransom in order to get the password to decrypt their own files.
It is different from other attacking techniques and victims tend to cooperate with the attackers because they think that they can decrypt the files only by paying the ransom. This might make them even bigger victims as it is not guaranteed that they are going to have their data unlocked after paying the ransom. It must be also noted that in many cases, it works out just fine and after paying the ransom you will get the unlock code and you can access your data again. Oddly enough, certain attackers even establish a helpline to assist the victims on how to make the payment and decrypt the files afterward.
Facts
Ransomware is not a selective attack only targeting corporations that are working with high volume of data. There can be different sorts of attacks. Anyone of us can be a victim of ransomware while we are surfing on the internet or trying to open an email that we did not expect (including hyperlinks or files of any kind). Concerning the latter, phishing email is one of the means to spread onto the victims’ computer through malicious content within the email. With the smartphone penetration on the market, the Android devices are becoming more and more targets for such attacks.
The facts are showing that huge profit has been made from malicious activities using ransomware. They target individuals just as well as businesses. The individuals who created the ransomware usually say: ‘it was never their intention to release the code and that their intention was not to have financial gains from their usage’.
Kaspersky reported that 36.232 users attacked in 2012 by some sort of ransomware, which number increased to 179.209 in 2015. This is close to a five-fold increase over a course of 4 years.
This financial ‘gain’ was quite incentive for intruders to try to find more sophisticated variants to reach the intended outcome. In 2013, other ways of advanced Ransomware techniques were introduced. The latest breeds of ransomware that have been introduced are called “Locky” and “Samas”. “Locky” was targeting hospitals and healthcare facilities in the United States, New Zealand and Germany. It spread widely through spam email within attachments. The same was the intention of Samas, another type of Ransomware where the whole network is targeted through scanning for possible entry points to exploit.
The Data Breach Investigation Report (DBIR, one of the largest information security investigation reports worldwide released by Verizon every year) states that ransomware became the 2nd most widespread crimeware and this type of threat is increasing exponentially.
How it can infect your system?
Any malware might seem legitimate. In case a person clicks on a link or on an attachment, a malware can start running in the background without any visible indication to the user. In case of a link, it will take the user to the destination URL that might appear as a legitimate site of one organization, whereas it is a fake site with malicious content. On such sites, the code could activate by exploiting outdated flash versions or getting the user to click on an action button to activate the code. This might not even trigger an alert even when a firewall is actively running, because this action was initiated by the user and it might seem as a legitimate action to the system. In the other case by clicking to open the attachment, the malicious code activates itself.
Either way, the malware could infect the machine, even if there is a firewall and virus scanning software running on the PC, and it will start encrypting all the data on the local drives as well as all other resources attached to the same network. Users on the network are not aware that they are infected with such a malware until their access to their files and documents will be denied. They will soon receive a message tdrivehat says something around: the access to the destination is impossible until you pay a ransom. The victim will be urged to arrange for the payment using bitcoins (purely electronic money), an option that is close to untraceable as a result of anonymity of the currency
Taking measures to avoid RANSOMWARE!
Looking at the recent facts and incidents, there seems to be a strong commitment to try to find a preventive solution for ransomware threats. One of the most recent cases is the ransom that a Canadian University had to pay in the amount of 20,000$. This university paid it because they couldn`t afford to lose their credibility. At the same time, they took preventive action to avoid this happening again. These actions included user awareness training amongst their students and warn them not to click on links or file attachments that they were not expecting and they have no idea what they contain. But such incidents have also happened in Europe within some public and profit-oriented organizations.
FBI and a few security agencies give recommendations on how to be aware of these threats, as follows:
• Pay more attention to security awareness sessions and trainings, relating these security issues.
• Apply security properties to the web browsers and email platform.
• Maintain direct contact with responsible persons and the department when it comes to suspicious cases.
• Implement overall business continuity plan, including scenarios for how to handle such cases.
• Take backups regularly and store it off-line (like on an external drive or USB storage). Not bringing the backup media off-line is crucial, otherwise the backup could also be compromised.
Conclusion
Every security issue is important. It would be ideal to know each fraudulent and malware techniques. Unfortunately, this is impossible as the techniques are always evolving and changing so it becomes more and more difficult to keep abreast of all kinds of threat sources.
A couple of tips beyond the above recommendations (more from individuals’ point of view):
Be mindful of what you do while you use any PCs. Be cautious when clicking on links and opening attachments (allowing macros). When you receive emails with links and files that you were not expecting, it is better to check with the sender over the phone to validate that it was she or he who really sent it. Always open sites by typing in the link yourself in your browser. Keep your system up-to-date with security patches (including but not limited to operating system, browsers and flashes, firewall software and office applications).
Some companies say that they have never been compromised and therefore they feel it will not happen to them. They might be wrong, because even if they have good security measures and systems in place and those are configured and operated correctly, one user insufficiently trained can still click and cause the problems with the consequences above described. So after all, unfortunately ransomware is less about the preventive security measures and more about the weakest link, the human factor when awareness gains one of the highest importance to prevent this kind of incidents.
The final piece of advice, make sure that you follow what is happening around the world concerning information security, think about how to avoid those from happening to you and your organization, and always make sure that you have competent security professionals assisting the operations in your organization.
PECB is entitled to deliver ISO/IEC 27001 courses and management system audit worldwide. Companies that implement an ISO/IEC 27001 framework show that they can treat better all security issues and efficiently respond to security matters. What is crucial for a company is to provide training and awareness sessions for employees so they can be well-informed regarding ransomware and other malware prevention.
About the authors:
Gezim Zeneli is an Account Manager for Information Security at PECB. He is in charge of conducting market research while developing and providing information related to Information Security Standards. If you have any questions, please do not hesitate to contact: marketing.sec@pecb.com.