This article will present cybersecurity vulnerabilities exclusive to the Internet of Things (IoT) and develop a corporate strategy to mitigate them and their impact. This article references risk and technology lifecycle management frameworks to help organizations plan and implement an effective cybersecurity strategy with technology, people, and processes. Additionally, this article develops a risk management framework to identify vulnerabilities, periodically review a strategy’s efficacy, implement corrective action plans, and address evolving trends or vulnerabilities.
Many discuss common technology solutions to protect enterprise assets, e.g. network, proprietary information, and client data. Vendors publish white papers to highlight its technology’s efficacy. Others recommend corporate governance to improve cyber compliance and policies. However, no one has proposed a comprehensive cybersecurity plan with staff and budget constraints.
Current State of IoT
IoT has been widely adopted to improve business strategy, augment human capabilities, automate industrial processes, and enhance public services. The technology is a fairly broad product classification which includes sensors, consumer wearables, such as smartwatches, and interconnected command and control systems. Catalysts for adoption are advances in wireless technology, improved processing power, and technology cost. It is estimated that 55 billion IoT devices will be in use in 2025, producing 79.4 zetabytes (1 zetabyte = 1,000 terabytes = 1,000,000 gigabytes). In 2023, the IoT market was worth $269 billion with 12% projected year-over-year growth in 2024.
Unfortunately, IoT security has not kept pace with technology integration. Only 2% of the IoT spending is allocated to security.
That spending (approximately $3 billion using the above market capitalization) is spread across staff training, cybersecurity tools, and compliance (if applicable). Executives have a fiduciary duty to shareholders to return value on investment.
Cybersecurity is not part of corporate strategy and has become an inherent cost of business. Corporations only mention cybersecurity in the event of a network or data breach. Wall Street and Canary Wharf rarely inquire about cyber defense during earnings calls. Investors and financial analysts rarely pressure corporations to improve their security posture.

Unique Security Challenges to IoT
Investigation into recent security breaches has identified critical vulnerabilities exclusive to IoT technology:
Poor Asset Management – Policies to maintain the IoT security posture are not properly developed. Documented cases show compromised systems were managed by non-Information Technology (IT) organizations (such as facilities) who lack the critical cybersecurity knowledge, skills, and abilities to mitigate threats. Traditional IT best practices and industry standards define Identity and Access Management (IAM), security and incident management (SIEM), and operations and management procedures. A commonly exploited vulnerability is when the component’s password is never changed from the manufacturer’s default password.
Diversity – IoT components and systems vary in complexity, capabilities, and resources. Cost and simplicity are principal drivers for IoT adoption. Many components are limited in memory and power, thereby, limiting the opportunity to implement security features such as access control and encryption. Further, many designs integrate obsolete components and legacy systems into IoT systems. These components are typically no longer supported with software updates and lack modern security features.
IoT architecture and security configuration are also defined by the application requirements. For example, a data collection system tracking consumer behavior in a shopping center has different security requirements from a climate control system.
Data encryption is necessary to protect consumer identity for the data collection application, however, climate control is less reliant on data integrity.
This diversity limits the application of best practices and industry standards typically applied to traditional IT networks. A systems engineering approach is required to effectively plan the cybersecurity architecture and policies.
Limited Industry Standards, Best Practices, and Government Regulations – IoT adoption has accelerated during the past decade. Economies of scale, simplicity, and scalability have catalyzed use cases for the technology. Historically, IoT components were selected for cost, scalability, and functionality; cybersecurity features were not part of the selection criteria.
Components vary in complexity from simple sensors with limited resources to complex modules with encryption, IAM features, and capabilities to add custom software controls. In many designs, IoT systems never incorporated cybersecurity best practices, security engineers review designs, or recommend best practices.
To date, the United States only regulates IoT cybersecurity for components and systems sold to the government. Excluding the state of California, which has enacted its own IoT cybersecurity law (SB-327) requiring manufacturers to include reasonable security features, the United States has not passed additional cybersecurity protections.
On April 29, 2024, the Product Security and Telecommunication Infrastructure (PSTI) regime became law in the United Kingdom. PSTI bans weak default passwords, mandates security vulnerability disclosure, and periodically updates software to improve security features.
The EU has recently adopted the Cyber Resilience Act, which is similar to the PSTI, however, it will not be enforced until the calendar year 2027.
Limited Defense in Depth – Traditional IT utilizes a defensein- depth approach to physical security. For example, the data center is housed within many layers of security: the first layer is typically a facility perimeter with limited access points such as a guarded entrance. The next security layer is typically key-card access control.
The final security layer to the data center is typically access controls, such as a separate access card. Network governance also follows a defense-in-depth Identity and Access Management (IAM) model with guests segmented into a secure network, employees’ requirement username and password for access, and administrators requiring a PKI card for enhanced access. IoT typically does not follow the defense-in-depth approach.
IoT components are deployed outside the first security layer where physical access is not controlled. Private wireless spectrum can be expensive to manage, hence, data is transferred across the shared spectrum. IAM is typically managed through a third-party application or cloud site. Finally, components can be constrained by limited processing and memory which limits capabilities for a security management layer.

Best Practices for Securing IoT Devices
A corporate cybersecurity plan requires people, processes, and technology. Technology alone does not eliminate all security threats. People require training to identify security events and implement countermeasures to reduce a breach’s damage. Processes are policies and procedures that govern and guide staff behavior to strengthen the security posture and implement best practices to react to security events. From a corporate perspective, improving cybersecurity reduces profitability and adds complexity to processes and designs.
Security Design
Previously, this article has shown that IoT components and systems are diverse and a standardized cybersecurity strategy is not effective. A systems engineering approach incorporates security as a design constraint. This approach analyzes a cybersecurity architecture’s efficacy and its potential cost, complexity, and effects on other design variables such as power, size, and data processing.
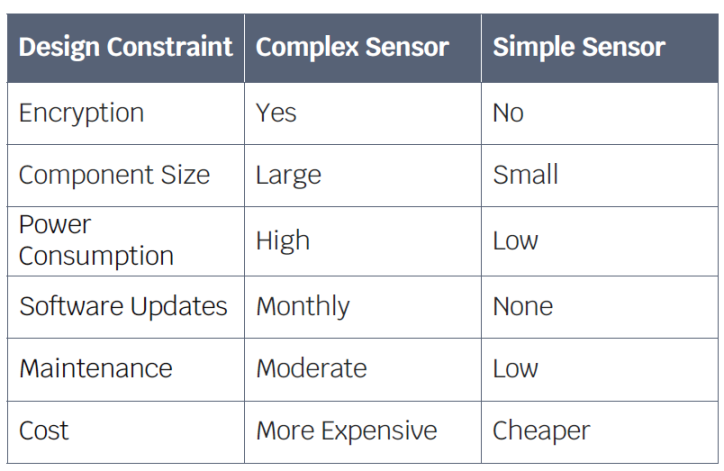
A simple notional example in Table 1 highlights a design trade-off study between two sensors. The complex sensor is suitable for systems that exchange sensitive data (due to data protection) while the simpler component is suitable for nonsensitive data exchange. The complex sensor requires additional power and space for additional components such as memory expansion. Further, the complex sensor requires periodic software updates which take it offline, as part of the planned maintenance.
Risk Management Strategies
Risk management is an effective approach to determine critical vulnerabilities and develop mitigation strategies.
Risks can be qualitatively analyzed using a risk matrix, shown in Figure 1. Risk likelihood is estimated along the X-axis while the potential economic damage is estimated along the Y-axis.
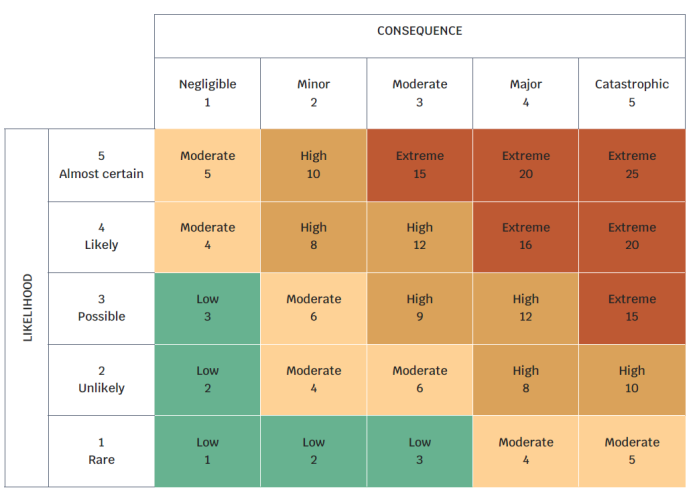
Figure 3: Risk Template
Multiple security vulnerabilities can be simultaneously assessed on a risk matrix to determine the greatest need. A risk assessment can be performed anytime throughout the system lifecycle.
For example, potential vulnerabilities can be assessed during the design phase or in response to an evolving security threat exploiting a previously unknown vulnerability.
This analysis is based on an understanding of the attack surface and trending exploitation. Based on each vulnerability’s severity and likelihood, the vulnerability is addressed through one of the four strategies:
Mitigate – This strategy actively plans to mitigate the vulnerability and minimize the overall impact.
Transfer – Transferring risk is typically an insurance policy that minimizes the financial impact when the vulnerability is exploited. Even though the financial impact is minimized, this strategy does not improve the reputation after an adverse event occurs. This strategy is utilized if it is a cheaper option than mitigating the risk.
Accept – Accepting risk is applicable to events that have minimal probability of occurrence and limited potential damage. Limited preventative measures are employed to mitigate the event probability. This strategy is sometimes referred to as ignoring the risk, however, this categorization is misleading since analysis have been completed to develop a response to the vulnerability. This strategy is utilized for risks located in the green-colored areas of Figure 1.
Avoid – This strategy is applicable to vulnerabilities that are too costly to remediate, have a high likelihood of occurrence, and cause significant damage. Avoiding the vulnerability means discontinuing the service or capability, or not pursuing the opportunity after analyzing the risk impact. This strategy would be executed for vulnerabilities located in the dark red areas of Figure 1.
System Development Lifecycle
A system development lifecycle is a conceptual model highlighting the event sequence from initial concept through obsolescence.
Implementing cybersecurity best practices into a system lifecycle is shown in Figure 2. Key cybersecurity contributions are highlighted throughout the system lifecycle.
During the design phase, security tools are integrated into the system design. The tools consist of both hardware and software platforms that strengthen the system’s security posture.
After the prototype has been implemented and is ready for a pilot phase, cyber tools scan the infrastructure, for vulnerabilities and best security practice compliance. These security gaps must be remedied before the system is activated for use.
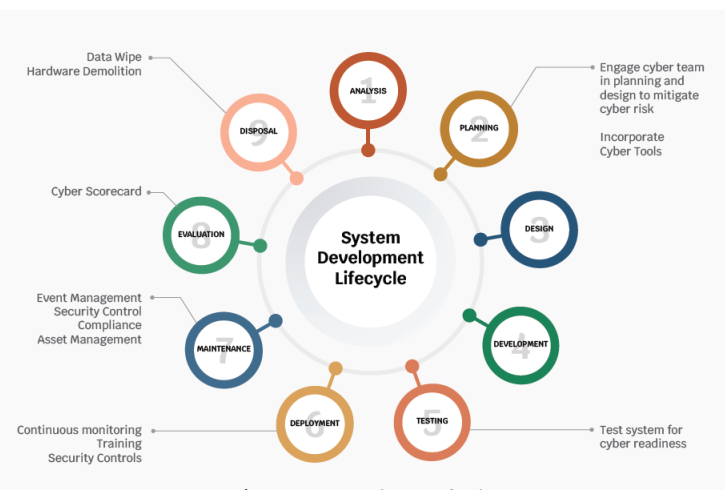
Figure 2: System Development Lifestyle
Event management is a critical gap in cybersecurity. When a data breach or virus infection occurs, key players must react to isolate the affected areas, remedy the vulnerability, collect lessons learned, and recommend strategies to mitigate future risks. To prepare for events, roles and responsibilities must be clearly defined and processes must be planned and broadcast to the key players. Periodic simulations or rehearsals with key players help refine event sequences, identify dependencies, and address any discovered gaps.
Asset management has previously been identified as a key defense against cyber risk. IT personnel must track the IoT assets throughout the lifecycle and manage software updates, configuration changes, repairs, and decommission. If properly managed, the sensors can be properly retired when they are no longer useful. The assets must also have their memory wiped and hardware must be demolished so data is not compromised nor can the hardware be repurposed or re-engineered to enable unauthorized network access.

Scorecard
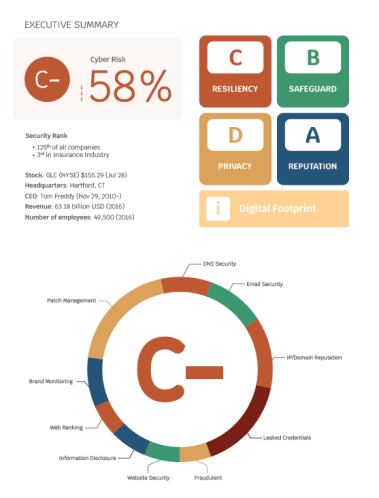
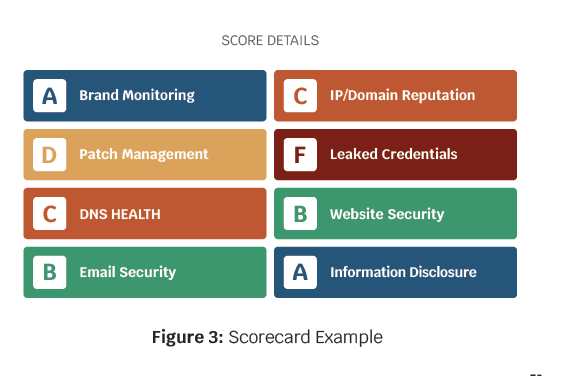
A scorecard is a dashboard used to continuously assess the efficacy of cybersecurity training, policies, and infrastructure. A scorecard should be simple and easy to read, however, it needs to state key deficiencies and critical trends explicitly. Figure 3, shows an example of a simple scorecard. The individual scores for the key success factors are tabulated on the right-hand side of the scorecard. This score decomposition identifies key areas to improve and strengthen the security posture.
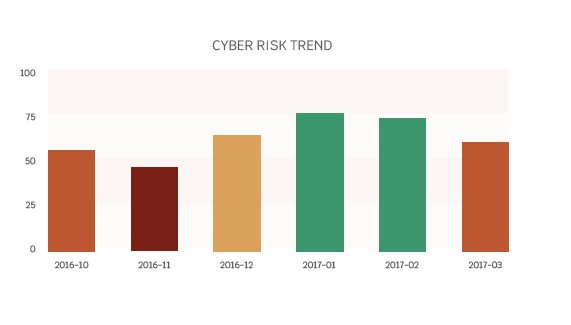
The top center shows the overall score and the score weighting to stress which factors have greater significance in the evaluation. The graph in the bottom center shows the tabulated score over a pre-determined time interval. The left-hand side is an evaluation of how the company’s cyber posture compares to its competitors. This scorecard is just an example, but the key data points are the overall score, the score breakdown to the individual metrics, such as patch management, the score weighting, and the trending score over the past year.
Other data points not presented in this scorecard are key security events, such as a data breach or bullets describing deficiencies. This scorecard also highlights evolving threats for awareness. A generic scorecard template can be downloaded or a custom scorecard highlighting key metrics can be designed in a spreadsheet tool.
Continuous Improvement
Finally, organizations must complete periodic reevaluations and audits should be implemented to identify developing vulnerabilities. Remediation plans are then evaluated and implemented to mitigate risk.
The Deming Cycle (Plan-Do-Check-Act), shown in Figure 4, is a management framework used to assess cyber readiness continuously and implement corrective action. During the Plan stage, multiple strategies are evaluated for cost, complexity, and potential efficacy.
The success criteria is also planned during this phase, as is the fallback plan in the event the strategy is not successfully implemented. The best strategy is selected and the implementation team plans the roll-out. The implementation team then integrates the strategy during the Do phase. During the Check phase, the implementation is evaluated against its key success factors, and lessons learned are also discussed.
Finally, in the Act phase, the next improvement is selected based on the success and lessons learned. The Deming Cycle is repeated as the improvement is planned, implemented, and evaluated.
Conclusion
This article presented the security challenges unique to IoT:
- Poor Asset Management
- Diversity
- Limited Industry Standards, Best Practices, and Government Regulations
- Limited Defense in Depth
Given the diversity across components and system design strategies, standard IT best practices do not evade all vulnerabilities. Different risk management strategies were defined and a risk management strategy was developed. Utilizing a risk management framework will identify known vulnerabilities and continuously reassess a cybersecurity strategy.