“ISO/IEC 27001, CYBERSECURITY, AND RISK MANAGEMENT – HOW TO AVOID DATA BREACHES”
Cybersecurity risk management is very important when it comes to maintaining the assets of an organization. Simon Lacey and Nick Frost, two renowned experts, came together to provide a comprehensive exploration of the subject matter during August 2022 in the PECB Webinar.
If you missed the live session or have burning questions that remained unanswered during the webinar, this is your chance to gain invaluable knowledge and clarification.
Question: In the case of a risk assessment project in a process where the involved parties could not get to an agreement on how to categorize risk, who should be the one to decide on the risk?
Answer: If it is a case of categorization, i.e. how to describe the risk, then you should refer to the SME, so if it is a cyber risk, then it should be the CISO. However, if it is an operational risk, then possibly the head of operational risk or the CRO. If the categorization is to do with the actual rating or description that is given to the risk, then again it should be the SME for the risk area (e.g., cyber, finance, operational, legal, etc.), and they need to provide the applicable evidence as to why the risk is of a certain rating.
Question: How to successfully execute risk identification according to ISO/IEC 27001 requirements?
Answer: The standard ISO/IEC 27001 states that a risk assessment is to be conducted to identify risk and the controls to reduce likelihood or consequence. However, it does not specify the specific process of a risk assessment – although it refers to guidance, such as ISO/IEC 27036 and ISO/IEC 27005, which are the main ISO documents for information risk assessment. There are many solid approaches to identifying risk using a structured process based on sound risk logic. In my experience, my recommendation for using a risk methodology in the context of ISO/IEC 27001, would be to follow a rigorous approach to ensure that the identification has been based on objective thinking.
Question: In terms of transparency, at what point should you start telling your clients about a data breach?
Answer: There will be legal and regulatory requirements for informing independent bodies that uphold privacy rights, such as the UK’s ICO, so this would be one of the groups to inform first. Many of these bodies can also guide you on how to approach clients as well. But what is important is to ensure you have a plan to investigate how the breach occurred (so you can remediate any vulnerabilities) and understand the extent of the breach (number of records, details, and individuals that may be compromised so you can alert them). In addition, your clients may have clauses in contracts that require you to notify them in a defined period of the discovery of a breach.
Question: Based on your experience, could you provide some insight into the prevalence and adoption of cyber insurance in the context of cybersecurity and risk management, particularly concerning preventing data breaches?
Answer: Five years ago, cyber insurance was considered a key requirement for managing risk. My observations are that organizations are now more aware of what is in and out of the scope of acquiring cyber insurance. A key feature of cyber insurance is that it can provide immediate access to security specialists (forensic cyber professionals) postincident, but it is unlikely that cyber insurance will act as a preventative measure.
Question: Does a CISO reporting to a ‘peer’ chief indicate a lack of priority for cybersecurity? Placing the CISO at an appropriate level within the organization is crucial for effective leadership and accountability in this critical area.
Answer: In very general terms, I would say that it is an example of maturity if the CISO is reporting to senior business management or C-level business representatives. We are all aware that cyber risk is a business risk, but this should be reflected through reporting lines, so the CISO has direct access to leadership. In many organizations we work with cyber risk is the top risk, so you would expect the leadership to want to get access to the CISO or equivalent. It is also important for the CISO to be supported if the reporting lines change so that both parties speak a common language of risk.
Question: What are the recommended steps for conducting a risk assessment of a large organization with hundreds of systems, and how can the process be optimized for efficiency and effectiveness?
Answer: It would be prudent to take a triage approach that would act as a pseudo filter to help distinguish between critical and non-critical systems in a situation such as this. Any system that is identified as critical should then undergo a cyber risk assessment.
Other features of a cyber risk assessment to consider that help streamline an approach would be to develop a set of re-populated data sets (threat templates, impact reference tables) that reflect certain characteristics of a system, i.e., an internet-facing device that contains credit card details will require a specific set of prepopulated threat templates, specific control library, etc.
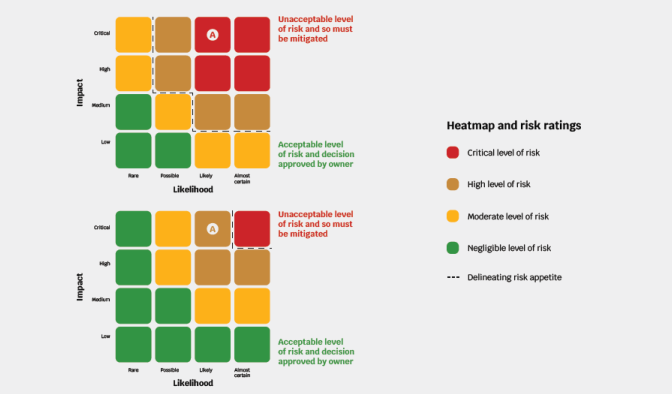
Question: Could you please elaborate on the organization’s high-risk appetite and how it can be documented and approved through the appropriate structure?
Answer: A common way to reflect an organization with a high-risk appetite would be to use a heat map such as below. The first image shows an organization with a lower level of risk appetite (redder) than the second image (less red).
An organization’s risk appetite may reflect a range of factors such as regulatory pressures (likely to have a lower risk appetite), a new venture (likely to have a higher risk appetite), operating in parts of the world that are exposed to more risks such as civil unrest, environmental disasters (and so would have a higher risk appetite).
Question: What is the rationale behind an organization adopting ISO/IEC 27001 for cybersecurity and risk management, and is ISO 9001, which is risk-based, sufficient to cover all aspects of risk management?
Answer: There are many reasons for why an organization would adopt ISO/IEC 20071 – these include requirements of key clients, opening new markets and business sectors, and providing assurance to the existing client base. However, there are other reasons as well, including formalizing existing business practices and enhancing resilience. The easiest way to understand the rationale clearly, is to map interested parties and their requirements of the business and information security.
The standard for information risk management is ISO/IEC 27005, which defines the steps to identify and evaluate risk. ISO 9001 is for quality assurance, although shares many similarities with ISO/IEC 27001 and it is possible to implement both at the same time, despite their different scopes.
Question: Does accepting data breaches reduce reputation risk, or is the greater risk the inability to demonstrate a reasonable state of cybersecurity, which could lead to legal, financial, and reputational consequences for organizations?
Answer: Accepting data breaches and a failure to demonstrate reasonable cybersecurity practices could both lead to reputational consequences.
If a data breach occurs, then it is likely that those individuals that have been affected will notify the information commissioner’s office (or equivalent), complain on social media, notify the mainstream media, and soon, which would not take long for negative attention to focus on the organization in question.
Question: What are the best practices for identifying a business’s threat landscape and creating a risk register? The process can be daunting, with the challenge of knowing where to start. Could you guide an effective and efficient approach to this process?
Answer: It would be best to start with a recognized cyber risk standard.
Any such standards will have a threat list, threat taxonomy, and a process to enable you to assess your threat landscape. But be aware that terms such as threat, vulnerability, impact, and risk need to be well understood to objectively assess risks to the organization.
Question: How can the cybersecurity industry address the issue of victims of cybercrime suffering financial loss and reputational damage with little legal recourse? By creating a more balanced playing field, there is greater potential for collaboration in identifying and prosecuting cybercriminals.
Answer: The cybersecurity community is helping victims of cybercrime as many organizations release threat data into the public domain, and recommend practices to protect yourself and your family from cybercrime. However, I do believe more can be done as we are seeing the cost of cybercrime continue to soar, for example:
- Independent bodies that can collate and analyze sources of threat intelligence to warn citizens of the latest scams
- Addressing barriers when law enforcement agencies are collaborating across multiple jurisdictions to track individuals that are responsible for such crimes
- Free access to technologies that can be used on home laptops – several governments now provide some simple but effective tools that can help address vulnerabilities that could lead to cybercrime
Question: What steps can organizations take to proactively secure more funding for cybersecurity initiatives, rather than relying on a reactive approach after a cyber-attack?
Answer: Establishing an understanding of cyber risks for your organization is key to providing a robust businessfocused argument as to what level of investment is a need and where it needs to target, and as you have mentioned establishing a proactive approach.
Conducting a program of cyber risk assessments over time will generate a rich source of data, that when analyzed, will identify key risk trends (i.e., the most common risk that has the biggest ‘potential’ impact on an organization, most common threat types, etc.).
These trends must be reported to senior management, so they understand the potential consequences to the organization.

Question: Which approach is better for risk management: scenario-based or asset-based? What factors should organizations consider when choosing an approach?
Answer: A hybrid approach would be best. When you are conducting an asset-based risk assessment, you should be using scenarios to enrich discussion when assessing the components of risk nevertheless, i.e. presenting scenarios such as the possible sequence of impacts following a data breach and scenarios when determining the sequence of threats that could occur from a targeted attack.
Question: What are the key areas that organizations in under-resourced regions like the Caribbean should focus on to enhance their cybersecurity posture, and how can they prioritize these areas in the absence of sufficient resources?
Answer: It would be best to focus heavily on scenariobased activities. If there are limited resources and funding to help prevent such cyber-attacks from occurring, then you have to fall back on “what do we do when attacks occur”.
It is something all organizations must do anyway, but for those similar to yourselves that are under-resourced, it is important that the focus is on how to respond to an attack and bring back the systems, and processes back in a minimal amount of time.
Question: When considering assets that matter for risk management, how can organizations factor in availability as a critical component? For example, if a system experiences prolonged unavailability, how does this impact the overall risk posture?
Answer: Assessing availability and the impact should be part of a business impact assessment.
The business impact assessment will consider the types of impact (reputational, operational) and respected levels (critical, high) based on a breach of confidentiality, integrity, and availability. When assessing availability, you need to consider the impact based on the length of the outage.









