I had no clue what a technology audit was when I was about to complete my Bachelor of Engineering (IT) degree in 2012. I had a few offers already for software developer roles with the usual mass recruiters in the Indian IT market and had selected one of those to be my future employer. Somewhere in January 2012, a lesser-known firm (EY) within the halls of engineering colleges, came to our campus with an offering slightly lower than the offers I had. However, it would be based out of Mumbai where I already was and where some of my good friends were going to be. A senior had joined last year and was happy with the role. I was still not convinced. Then he mentioned that after one year the total compensation would double and triple after two years. Now I was definitely intrigued.
Coming from a Tier 2 (maybe 3?) city in India, this was big money. Hence, like a lot of Indian graduates, money was the primary motivation for the role, not passion, unfortunately. I somehow managed to secure this job and decided to stick with it. However, I still did not understand what my role would be. Maybe I could have benefited from a note like this but not much was available. Hence, I am taking the opportunity to pen down my thoughts today which hopefully would help someone decide whether this is the career they want for themselves.

What is a Technology Audit?
Most of us know what a financial audit is. In basic terms, an audit ensures that the financial statement of accounts that a company publishes and shares with its shareholders/ stakeholders can be relied upon. An audit is typically performed by independent third parties (external auditors) or an internal audit team (still independent of the business functions). A couple of decades back, most of this financial information would be in hardcopies, excel sheets, or very basic pieces of software. Most of the audit efforts were focused on reviewing these records and ensuring that they balance (LHS=RHS).
The final report will then inform all stakeholders about the integrity of the statements that the organization being audited has published. Based on these reports, the stakeholders could then derive their conclusions as to whether the company is achieving its goals and is on the path to doing the same or better in the future. However, with the advancement in the technology world and the adoption of sophisticated applications to aid financial transactions, maintain records, provide reports, etc., it started becoming increasingly clear that there is a need to ensure that these ‘financial applications’ themselves can be relied upon. In comes technology audit.
Technology audit part of a financial audit focuses on ensuring that the ‘financial applications’ themselves can be relied upon. However, this is easier said than done. As you start peeling through these applications, you find yourself entangled in a web of interconnected ‘systems’ that can provide an entry point to compromising the integrity of the financial statements. These entry points can be abused by internal or external malicious users, an unseen error, or even the leadership teams (Enron, Worldcom, Wells Fargo, etc.). You start with the application, then move on to the underlying operating system, databases, internal/external network, interfaces with other systems, and all the way to supporting tools for managing specialized tasks, such as authentication, scheduled jobs handling, backup, etc. This is where everything becomes challenging, as well as exciting.
Until now we spoke about audits mainly from a lens of financial audits. However, technology audits can have multiple focus areas with an overall aim to ensure that the owners of data/information are doing enough to ensure the security of the same. Let me share a high-level view of a couple of fundamental concepts before delving into the next topic Types of Technology Audits.
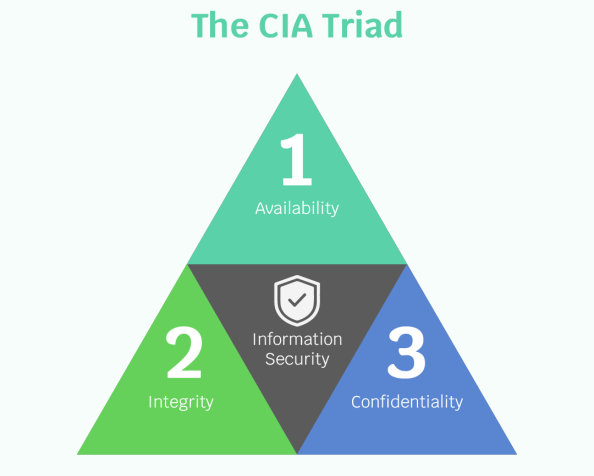
The CIA Triad
This is the most fundamental and important model for any technology audit that you would ever perform. It has three basic tenets:
- Confidentiality: Data should be secured against unauthorized access and should only be accessible on a need-to-know basis.
- Integrity: Data should not be tampered with or altered by any means that would lead to doubts over its authenticity and reliability.
- Availability: Data should be made available to the appropriate/authorized users at all times.
If any of the above principles are violated, we run a risk of security compromise which can range from low to critical severity based on the impact of the compromise. For e.g., a compromise of a database containing customer payment information of an e-commerce site could end up exposing such sensitive information for millions of customers transacting on this website.
The role of a technology auditor is to perform periodic checks to ensure management has the right people, processes, and technology in place to identify and manage such risks. Any gaps noted are highlighted to appropriate stakeholders for further action.
Three Lines Model
To manage risk within an organization, there needs to be an effective divide of roles and responsibilities. The ‘three lines model’ aims to provide a framework for the same. Below is a high-level representation, however, organizations differ in how they implement it.
- Governing body: This will typically be the Audit Committee and Board of Directors. They are accountable to the stakeholders for providing risk and audit oversight to the organization.
- Management: These are the leaders and employees from business units responsible for operational and strategic activities.
- 1st Line: Leads and directs actions (including managing risk) and application of resources to achieve the objectives of the organization. They perform tasks to ensure compliance with legal, regulatory, organizational, and ethical expectations. •
- 2nd Line: These are risk management experts who provide expertise, support, monitoring, and challenges related to the management of risk.
- Internal Audit (3rd Line): Independent team responsible for ensuring that appropriate risk is being managed appropriately by the organizational management. They are accountable to keep the governing body informed.
Armed with the knowledge above, let us delve into the different types of audits we would generally perform.
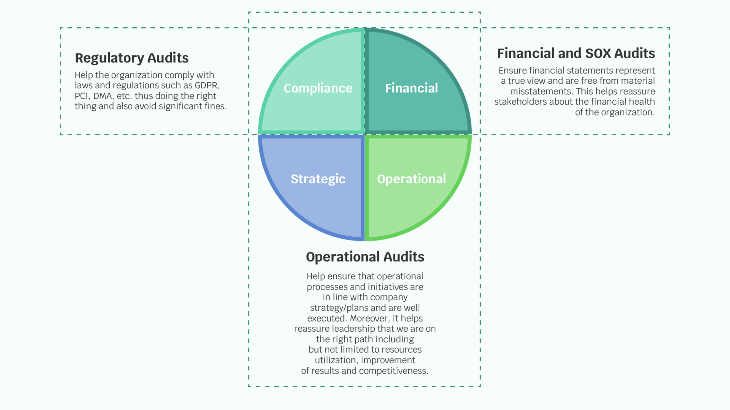
Technology Audits
At a high level, audit services can be categorized into three main buckets around four key risk areas. Combining all of these provides an effective oversight over the overall Enterprise Risk Management.
Any audit will typically have the following stages:
- Audit planning: Defining the ‘why’ of the audit and running it across with the Audit Committee (AC) and Board of Directors (BoD) to ensure we have the right/ relevant topics captured.
- Pre-audit activities: Review of detailed audit scope, agreement on scheduled, information requests, etc.
- Fieldwork: Conducting interviews, performing tests, reviewing evidence, and formulating draft findings.
- Reporting: Discussing and finalizing draft findings, assigning risk ratings, etc.
- Management Discussion and Report Finalization: Validating issues, defining action plans with timelines, drafting conclusions and summaries, sharing final report with appropriate stakeholders, sharing the summary with the AC and BoD.
- Follow-up: Periodic updates to track progress on action plans vis-a-vis timelines and reporting on the status to the AC and BoD.
In my experience, the key to a successful audit boils down to extensive preparation and open lines of communication.
Mapping this back to the ‘three lines model’, the AC and BoD will act as the ‘Governing Body’, management is the auditee (1st line) supported by the risk function (2nd line), and the audit is performed by the audit function (3rd line).
Coming to the CIA triad, the primary responsibility of ensuring the security (CIA) of the systems lies with management. They are supported by the risk function and periodic reviews and audits are performed by the audit function. All audit results are reported to the AC and BoD who eventually own the risk.
Therefore, What Does My Role Entail?
In my current role as Senior Manager – Technology Audit, I lead teams to perform various audits across the technology landscape at my organization. Most of my time is divided into the below key areas:
- Audit Planning: I take the lead in obtaining information from various stakeholders, understanding company strategy, staying abreast of external trends, reviewing risk dashboards, etc., to collate a comprehensive list of key technology areas and programs that may be audited in the next year. This information is then discussed with key stakeholders, such as Leadership teams from LOD 1 and 2, before being presented to the Audit Committee for input and approval.
- Audit Execution: This requires guiding the team through the entire audit execution starting from scoping to reporting. This is to ensure that the key audit objectives are met and timelines are adhered to. It is critical to ensure that the audit report is relevant and helps the business units better manage their risks.
- People Management: This is absolutely essential for a high-functioning and high-delivering team. It requires investing time to understand the motivations, aspirations, weaknesses, and strengths of your team to provide them with opportunities that make them shine, and the tools and guidance that help them in the areas that need improvement.
- Stakeholder Management: Another important pillar to establish visibility and credibility across the organization. Every person working in the organization wants to do the right thing, however, all of them operate under practical constraints, such as lack of resources, conflicting priorities, changes in strategy, ad hoc activities, firefighting, etc. Unless you understand these constraints and explain how your work would benefit them, helping them achieve their BU goals and setting them up for success, you will not be able to drive through meaningful changes.
Besides these key areas, there are many other things, such as continuous self-learning, team activities, new initiatives for improvement of efficiency and deliverables, etc. that would make up for the rest of the time. Also, not to forget some well-deserved time off across the year to keep myself focused and energized.
Key Challenges
While technology auditing can be quite rewarding, it comes with its fair share of challenges. I have tried capturing the major ones below:
- Constantly evolving technology and regulations: Technology stacks in organizations are constantly evolving and so are the laws around the use of technology. Large-scale adoption of generative AI is very recent and we are already looking for an agreement to be reached around the EU AI Act by the end of 2023. Such changes in technology and associated regulations require audit professionals to keep updating themselves constantly. This requires investment of time in understanding the risks in an ever-changing landscape. Unless you are passionate about what you do, this can become tiring and stressful really quickly.
- Stakeholder Management: This would be true for anything that you do but is even more so for technology audits. You would have to ensure you have good working relations and are respected by your peers and leaders across the organization. Otherwise driving impactful and sustainable changes would be next to impossible.
- Communication (Spoken and Written): Similar to stakeholder management, this one is true for any role that you might end up with. Keeping key stakeholders informed at all times, understanding your audience, and tailoring your communication to the same, whether in meetings or in reports or e-mails, is absolutely essential to ensure you have the support to perform your job effectively and efficiently.

Summing It Up
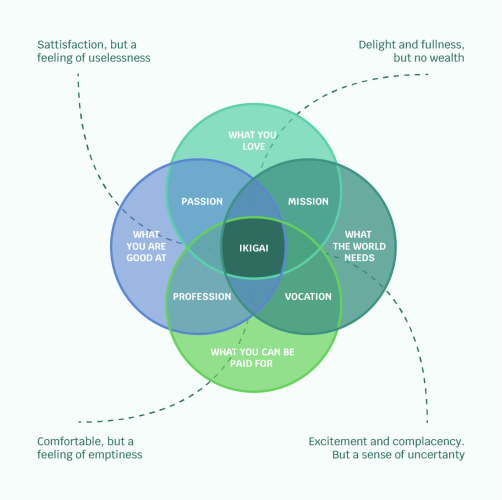
For me, what started by chance and a pursuit of financial gains, ended up turning into passion and unwavering commitment to showing up every day and doing my best. Some of you may have heard about the Japanese concept of Ikigai. To summarize, it states that you can find the best-suited role for yourself if it includes the below:
- What you love
- What you are good at
- What you can be paid for
- What the world needs
Through this article, I hope I have been able to explain what technology audit is, why it is in demand, and why the world needs it. Based on this information, you may decide whether this is something you would love and whether you would want to put in the effort to be good at it. Because if the answer is yes, then you may just have found your calling.









