In order to completely fulfill the business needs driving the development of 5G by the 3GPP standard organization, 5G uses and introduces technology enablers that transform 5G networks into cloud-based, programmable, software-driven, service-based, and holistically-managed infrastructures, utilizing enablers such as cloud technologies, Artificial Intelligence, open APIs, and Multi-access Edge Computing.
Although 3GPP standard specifications have increased the security of 5G relative to 4G, the use of those enablers, some of which are not in the scope of 3GPP, have introduced new security threats and vulnerabilities that cannot be addressed solely by the 3GPP security framework. With such a diversity of technology enablers composing the 5G solution eco-system, the overall 5G security framework looks fragmented.
This article presents the technology enablers introduced or used by 5G, with their respective security vulnerabilities. It also presents the contribution of key organizations, government, and industry groups that work on securing 5G enablers via security standards, vulnerability analysis, and best practice recommendations.

1.0 5G Business Drivers
Four generations of cellular technologies were all about connecting people, whereas 5G is about connecting people and everything else.
In line with this vision, the 5G business objectives are:
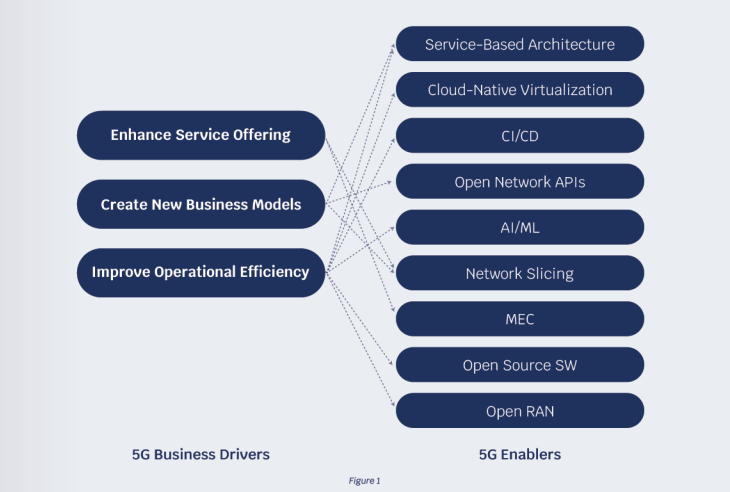
- Enhancing Service Offerings – relative to 4G with improved network performance, a wider range of types of devices supported, and more vertical segments being better served
- Creating New Business Models – beyond connectivity provider by fostering an open and agile ecosystem of partners and allowing customers to self-manage their services
- Improving Operational Efficiency – by shortening the time-to-market and time-to-customer of new services, by simplifying network operations, and reducing the cost of services
Taken together, those objectives will accelerate the digital transformation of pivotal economic sectors.

2.0 5G Enablers
This figure shows the dependency between the 5G business drivers and the 5G technology enablers.
2.1 Service-based Architecture
The biggest contribution towards a Cloud-Native 5G comes from the 3GPP-proposed Service Based Architecture (SBA) in all control-plane, user-plane, and managementplane Network Functions. This architecture makes the development of the 5G network far more modular compared to legacy systems and enables functional and service agility. With SBA, 5G network functions communicate using HTTP 2.0 messages, with REST API calls to each other on their well-defined interfaces.
To protect the SBA, 3GPP TS 33.501 introduces a new security domain for 5G SBA domain security composed of a set of security features that include:
- Network function registration, discovery, and authorization security aspects
- Authentication (TLS 1.2 or 1.3), authorization (OAuth 2.0), and encryption (TLS 1.2 or 1.3) of API calls between the 5G NFs
3GPP has been also working on specifying hardening of network nodes so that their security can be tested and certified. Security requirements and test cases for network equipment implementing 3GPP 5G network functions are specified in 3GPP Security Assurance Specifications.
2.2 Cloud-based Network Virtualization
One of the most important innovations in the 5G architecture is the complete virtualization of the core network. Whether virtualized as Virtual Network Functions (VNFs) or Container/Cloud-native Network Functions (CNFs), the 5G network can now be deployed on any public, private, or hybrid cloud infrastructure.
As a result of virtualization, network resources can be configured, possibly without human intervention, and allocated to service the needs of specific customers or service categories, without needing physical adjustments or dedicated infrastructures. This enables service and network automation.
Although container-based cloud-native architecture provides some inherent security protection due to isolation and containerization, the virtualization of network functions will introduce new and complex security vulnerabilities that can be categorized as:
- Container vulnerabilities
- Container networking vulnerabilities
- Hardware & host vulnerabilities
Some solutions for the abovementioned include:
- Hardening of the NFV and CNF Infrastructure
- Implementing strong security mechanisms for authentication, authorization, encryption, and validation in the virtualization management layer
- Securing the Orchestration and Automation layer responsible for managing the VNF/CNF
The following organizations have made significant contributions to cloud security:
- ETSI Network Function Virtualisation Security (NFV SEC) working group: NFV security specifications
- NIST: guidance and recommendations
- 3GPP: security assurance for virtualized products; security impacts of virtualization
- ENISA: security aspects of virtualization
- ONAP: VNF API Security Requirements
- NSA-CISA: Security Guidance for 5G Cloud Infrastructures
- CSA: Best practices for mitigating risks in virtualized environments
2.3 CI/CD
Although used extensively in the IT domain, CI/CD is relatively new to the telecom domain. CI/CD will become a necessary part of the network life cycle management to achieve automation and agility, ensuring carrier-grade stability, and improving operational efficiency. A CI/CD pipeline could span multiple organizations, originating in the SW vendor domain and terminating in the operator domain, thus increasing the security risks.
Security aspects must be integrated into the design of the end-to-end CI/CD pipeline from start to finish and should be incorporated in security best practices. NIST SP 800- 204C provides guidance for implementing CI/CD pipelines with high-security assurance.

2.4 Open Network APIs
3GPP standardization defines the following network exposure capabilities to enrich the collaboration between network operators and the eco-system of third-party service and application providers:
- The Network Data Analytics Function (NWDAF) collects network data, performs analytics, and provides results to the operator’s analytic engines.
- The Network Exposure Function (NEF) in 5G provides the ability to convert network capabilities and network APIs into special service APIs that can make network capabilities discoverable and available at the application level.
The uses of these new Open Network APIs introduce new threat vectors, but 3GPP has taken steps in enhancing the security for the external API communication by introducing security features and security mechanisms for the common API framework (CAPIF) as specified in 3GPP TS 33.122. 3GPP TS 33.501 covers security aspects of Network Exposure Function (NEF).
2.5 Artificial Intelligence & Machine Learning (AI/ML)
AI/ML is a key enabler for 5G in the automation of network planning, network operations, and service assurance across all network layers i.e. 5G RAN, the backhaul transport, and the 5G Core. However, this enabler is also available to the attacker, and AI-driven attacks are anticipated.
5G being increasingly dependent on AI/ML for critical functions and services will not only create greater incentives for attackers to target those algorithms, but it also brings the potential for each successful attack to have more severe consequences. In addition to providing generic software and hardware security for the AI/ML applications, the integrity and confidentiality of the AI models and data need to be protected to prevent attackers from stealing the data or changing the inference results.
The ETSI Industry Specification Group on Securing Artificial Intelligence (ISG SAI) develops technical specifications and reports focusing on three key areas; using AI to enhance security, mitigating against attacks that leverage AI, and securing AI itself from attack.
ETSI GR SAI 004 describes the problem of securing AIbased systems and solutions. ETSI GR SAI 005 summarizes and analyses existing and potential mitigation against threats for AI-based systems.
NIST is currently working on an AI Risk Management Framework that aims to foster the development of innovative approaches to address characteristics of trustworthiness.
2.6 Network slicing
Network slicing is a key architectural feature in 5G that enables multiple virtual networks to be created on a single physical network infrastructure. A network slice is effectively a logical network serving a defined business purpose or customer consisting of all required network resources configured together. With network slicing, the 5G system is capable of simultaneously supporting multiple combinations of reliability, latency, throughput, positioning, and availability requirements.
However, improper network slice management may allow malicious actors to access data from different slices or deny access to prioritized users. Network slices are intended to be configured with different levels of security depending on the user SLA requirements. Therefore, the security model for each slice should be adapted to the specific use case and should consider the following categories of measures:
- Slice Access Security: to complement network-level authentication mechanisms with network-slicespecific authentication and authorization mechanisms
- Slice Isolation: of traffic, of bandwidth, of processing, and storage
- Slice Management Security: management of networkslice- specific log information to support post-incident and root cause analysis
3GG TR 33.811 and 33.813 present studies on the threats, potential security requirements, and solutions for the 5G network slicing management, and they include identification of key security issues and recommended mitigation measures.

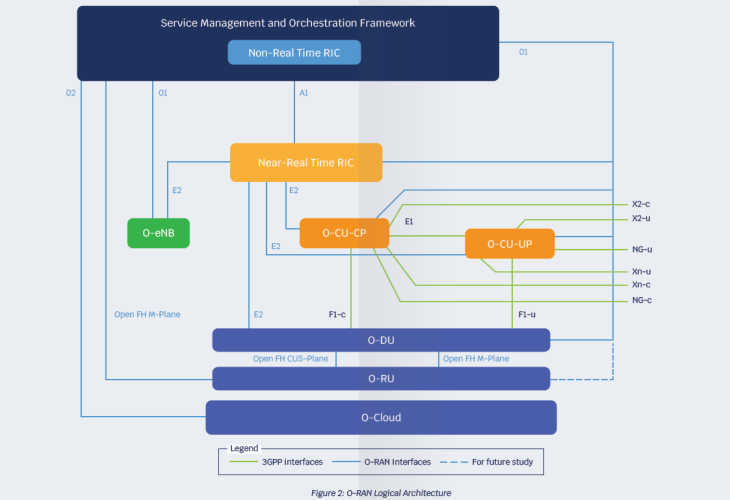
2.7 Open RAN
The ambition for Open RAN is to create a multi-supplier RAN solution that allows for the separation between hardware and software with open interfaces and virtualization, hosting software that controls and updates networks in the cloud. The promised benefits include supply chain diversity, solution flexibility, and new capabilities leading to increased competition and further innovation.
As shown in the figure, the O-RAN Alliance architecture introduces additional interfaces, functional splits, and disaggregation.
The expanded attack surface from additional RAN network functions and open interfaces creates additional security vulnerabilities.
The O-RAN Alliance Security Focus Group (SFG) develops solutions to counter threats, and it sets security requirements and protocol specifications for each O-RAN release to guide the development, deployment, and operation of an O-RAN:
- O-RAN Security Protocols Specifications v2.0
- O-RAN Security Threat Modeling and Remediation Analysis 2.0
- O-RAN Security Requirements Specifications v1.0
2.8 Multi-access Edge Computing (MEC)
In the context of 5G, Edge Computing is a concept that enables services to be hosted close to the service consumers, with 5G network elements and application servers potentially installed on customer premises.
MEC provides a significant reduction in end-to-end latency and on load on the transport network, which is key to addressing several new and enhanced use cases – including Industrial IoT, Industry 4.0, autonomous driving, etc.
By having network elements and MEC application servers hosted on customer premises outside the security perimeter of the operator’s network, the key security threats to MEC are related to physical security, software tampering, MEC nodes overload, abuse of MEC open APIs, and vulnerabilities related to virtualization and containerization infrastructure hosting the MEC. Because the various elements of the MEC system can be deployed, managed, and operated by different stakeholders, MEC environments are intrinsically heterogeneous, which increases the security risks.
Furthermore, the overall MEC system security design heavily depends on the security practices and specifications of closely related 5G enablers e.g. cloud infrastructure, Open Network APIs.
- ETSI White Paper No. 46 MEC security presents the status of security-related standards, such as:
- ETSI ISG NFV for infrastructure virtualization and management
- Trusted Computing Group (TCG) for physical platform security
- IETF specifications for securing access to MEC services
- ENISA 5G Threat Landscape identifies the potential threats related to MEC
- 3GPP TR 33.848 on security consequences of virtualization applies to many MEC use cases where the need for additional security controls is higher than in core network data center
2.9 Open-source SW
The use of software from open source is common in a range of initiatives driving open architectures and virtualized telecoms infrastructure such as Telecoms Infrastructure Project (TIP), Open-Radio Access Network (O-RAN) Alliance, Linux Networking Foundation, and Open Networking Forum. Most of those initiatives sponsor open-source projects upon which 5G commercial solutions rely.
Open-source code has a number of advantages, most notably:
- The transparency of code reduces software complexity, fragmentation, and bug count
- It increases interoperability across commercial products by creating de facto standards
- Contributes to a wide community of developers that can accelerate telco cloud implementation.
- It facilitates security testing by independent third parties
Risks
- The integrity of the software, especially from open-source locations and the overall software supply chain, is an area of vulnerability
- Malicious developers can introduce intentional backdoors
- Attackers can review the code and identify vulnerabilities
The use of open-source software requires a higher level of due diligence, which organizations can implement by using tools and applying industry best practices for supply chain management, secure software development, and secure software maintenance, including:
- Software composition analysis (SCA) tools are used to generate the software bill of materials (SBOM), a documented list of third-party software suppliers, including free and open-source software; SBOM is an industry best practice for a secure Software Development Lifecycle (SDLC) process to properly and safely handle software vulnerability notifications and updates
- Static & dynamic application security testing (DAST & SAST) to analyze and test applications for static code-based and dynamic run-time security vulnerabilities
- The Linux Foundation Core Infrastructure Initiative (CII) has a Best Practices Badge for open-source projects to self-attest
- OWASP has made available many automated vulnerability detection tools available to open-source projects
- NIST offers valuable guidance for open-source software security:
- NIST’s recent white paper “Mitigating the Risk of Software Vulnerabilities by Adopting a Secure Software Development Framework (SSDF)” recommends that open-source software consumers ensure that software modules are vetted for vulnerabilities and actively maintained for remediation.
- NIST SP 800-161 “Supply Chain Risk Management Practices for Federal Information Systems and Organizations” provides guidance for OSS to be continuously evaluated, monitored, whitelisted, inventoried, supported, and remediated.
3.0 Conclusion
This article has presented an overview of references to key security standards, vulnerability analysis, and best practice recommendations with regards to the 5G technology enablers.









