IoT and Blockchain have become buzzwords in the current technological era. Every new technology solves some problems and generates new challenges. Cybersecurity is one major challenge that is hindering the fearless usage of technology. The solution lies in how effectively these technologies are integrated and implemented. Hence, this article is an overview of the integration of IoT and Blockchain to ensure cyber safety. It also discusses the essential security measures and lists the IoT security challenges.

IoT Overview
The network of physical electronic devices, or machines, are implanted with sensors and software for the purpose of communicating and exchanging data with other devices and systems through the internet, each of these devices has an IP address, is referred to as the Internet of Things (IoT). Today IoT plays a major role in transforming our lives. As technologies are enhancing, hackers and cybercriminals are developing new, high-tech ways to breach secure and private data. However, with significant advancement in the IoT range, the issues related to data and information security needs to be addressed.
IoT has enormous advantages but they often lack security. User data must be kept private and safe. Better security must be created, maintained, and made the norm for IoT and linked devices to keep the data secure. In addition, IoT makes it possible to share data and information via Blockchain.
Highlighting some of the major IoT security challenges:
- Visibility and Transference
- Data Privacy, Confidentiality, and Integrity
- Authentication, Authorization, and Accounting
- Secure Communications
- Data Encryption
- Middleware Security

Blockchain Overview
Blockchain is an indispensable technology that is hitting headlines due to the popularity of cryptocurrencies, such as Bitcoin and Ethereum. Is Blockchain only concerned with cryptocurrencies? The answer is an emphatic no. Blockchain technology has moved beyond cryptocurrencies to another level.
Blockchain is a distributed, decentralized, immutable ledger that can be used to record transactions and track assets with Blockchain, the intermediary in digital transactions is eliminated. In a Blockchain, each block in the chain represents a record, and the chain links all of the blocks together.
Key Security Features of Blockchain:
- Cryptographic Security: Hash functions are one-way functions where it is simple to go ahead (from input to output) but computationally impossible to move backward (output to input).
- Identity Management: Blockchain identity management systems address current identity issues such as: inaccessibility, data insecurity, and fraudulent identities.
- Multisignature: Blockchain uses digital signatures to ensure the authenticity and integrity of transactions; Multisignature requires multiple private keys to generate a valid digital signature, allowing multiple parties to approve a transaction. Furthermore, in blockchain technology, it is infeasible to break public key cryptography even by brute force guessing.
- Data Privacy: As data in blockchain is imputable and blockchain network can be configured in Private/Public or Permissioned/Open Blockchains
- Secure Communication: Blockchain can ensure that an attacker cannot monitor and change the communications occurring between nodes.
IoT and Blockchain are both fantastic innovations on their own, but when they are combined and implemented, they get astounding outcomes that are beneficial for cyber safety.
Below are the use cases for integrating IoT and Blockchain to ensure Cyber Safety.
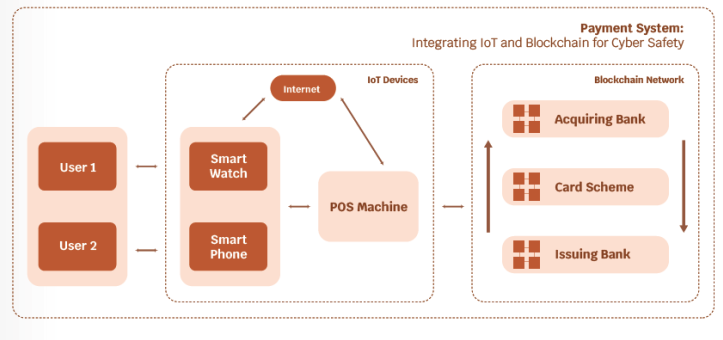
Use case A: IoT Payment System: Integrating IoT and Blockchain for Cyber Safety:
Use case B: Health System: Integrating IoT and Blockchain for Cyber Safety:
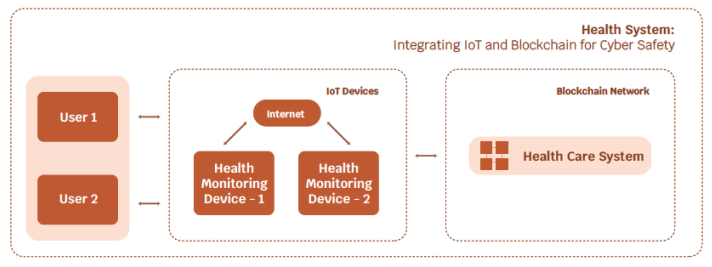
Currently, IoT technology is used with conventional databases. The above high-level block diagrams (Use case: A and Use case: B) the Payment and Health Care systems can be replaced by Blockchain technology.
However, the process and flow remain the same.
By adopting Blockchain technology, it is possible to address the following IoT cybersecurity concerns:
- Blockchain is based on peer-to-peer network in which all nodes have the same copy of records which solve the Data Integrity issues.
- Blockchain can be implemented in Private/Public or Permissioned/Open Blockchain. It ensures access control and prevents unauthorized access to Data Privacy. Furthermore, Blockchain can keep track of data gathered by sensors and prevent fraudsters from duplicating it with other harmful types of data.
- ECDSA (Elliptic Curve Digital Signature Algorithm) solves the limitation of IPv6 address
- Blockchain network can track every transaction and record, which addresses the problems with trusted accountability.
- Blockchain network will be connected to multiple nodes, it will be resilient, and fault-tolerant, this solves the problem of single points of failure.
- Blockchain hashing function generates a unique ID, that can be assigned to each IoT device. Furthermore, each transaction and record will be tracked in the blockchain network which will solve the problem of identifying the trusted origin of data.
- Blockchain operates on reading writing operations only, data in blockchain is immutable, which will address the data compromise and data manipulation issues.
- Blockchain technology is third-party and risk-free, as it can perform operations without the intermediary.
- Smart contract programs help to develop access rights and customize the policies based on the requirements.

Conclusion
The future of the financial sectors and other industries is becoming increasingly digital, which makes the process more convenient for end consumers. Internet of Things (IoT) and Blockchain technology are part of this rapid transition towards the bank of the future, both end users and financial sectors as well as other industries need to adapt to these trends for cyber safety.
Thus, with the development of high-speed networks and sophisticated network devices, IoT is unquestionably an emerging technology. IoT currently faces security limitations and concerns, some of which can be addressed by incorporating Blockchain technology.
The challenges of technology and cybersecurity are two sides of the same coin. The importance of cyber safety increases as technology evolves.
Disclaimer: The views and opinions expressed in this article reflect those of the author and not of his organization, company, or colleagues.









