Securing critical business information has become increasingly important for growing organizations. Information Security Policies are effective tools to communicate management’s commitment and expectations from employees and stakeholders regarding security.
The purpose of this article is to provide an overview of information security polices, including their objective, types, and development lifecycle.
Why do we need Information Security Policies? Security policies fulfil several purposes such as: a tool to set the rules and expectations required from users, administrators, etc., authorizes the security team to monitor and investigate, defines consequences of violation, minimizes business risks, and helps to comply with laws and regulations.
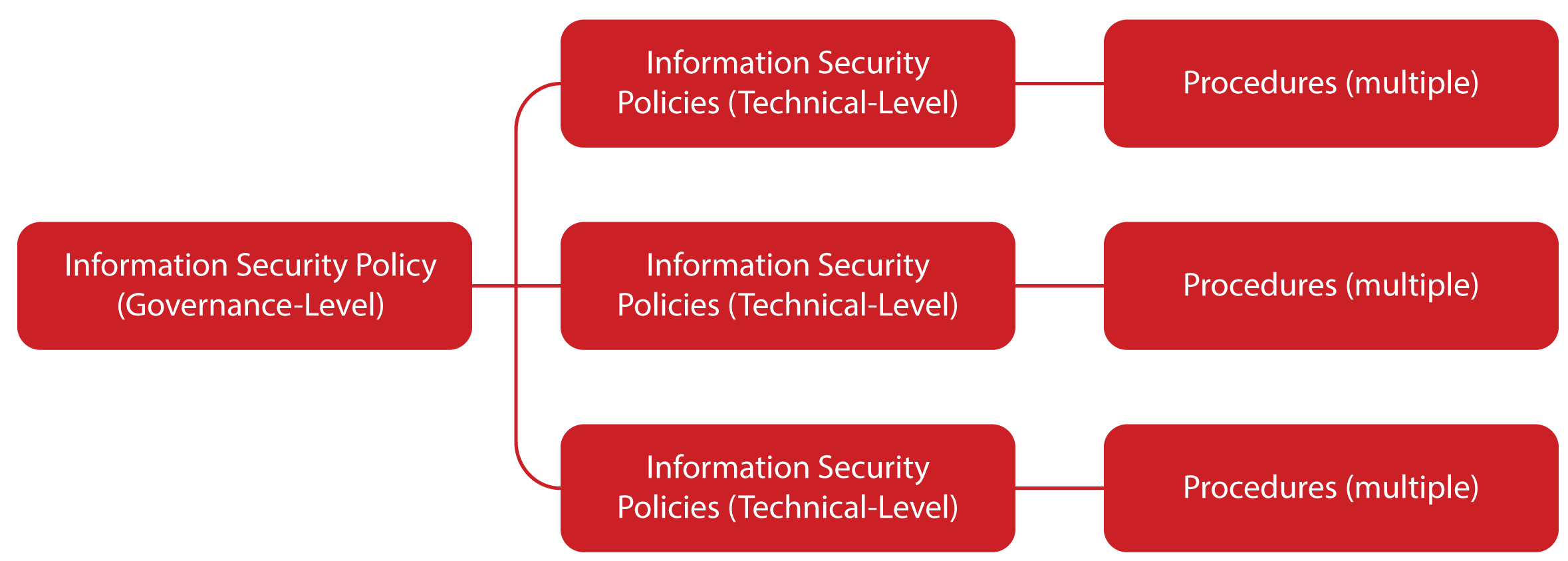
What are the Policy Types? Information Security polices can be classified as Governance-level policy and Technical-level policies. Governance-level policy is the top-most policy, it is a single document, signed and issued by the senior management (e.g. Chairperson or CEO). Technical-level polices complement Governance-level Policy, for example Technical-level Policies are email policy, anti-virus policy, access control policy, etc. and procedures address the “how” part and can be considered as vehicles to effectively execute policies.
What are the Policy Audiences & Contents? Content of a policy is based on its audience and governing Policy is read by all users. Therefore, it should cover information security concepts at a high level, define these concepts, describe why they are important, and detail what your company’s stand is on them. Technical-polices is used by relevant users and should address the “what”, “who”, “when”, and “where” in more detail in terms of the Governance-level policy.
Who Should be Involved? It is important to determine who is going to be involved in the actual development of polices. Ideally, a policy should be developed by the same group who will later own and enforce it. For example, Governance-level policy can be written by Information Security team in association with the Senior Management. Depending on the availability of skills and experience, assistance from experienced consultants can be considered. Other roles that may provide input include technical teams, legal team, human resources team, audit and compliance, etc.
What are the Phases of Policy Development?
The policy development process starts from securing Senior Management’s commitment. Senior Management must be made aware of both the importance and size of the task ahead so that they can allocate resources accordingly. Enforcement and compliance of policies cannot be done without the ownership and support from the Senior Management.
Who Should be Involved? It is important to determine who is going to be involved in the actual development of polices. Ideally, a policy should be developed by the same group who will later own and enforce it. For example, Governance-level policy can be written by Information Security team in association with the Senior Management. Depending on the availability of skills and experience, assistance from experienced consultants can be considered. Other roles that may provide input include technical teams, legal team, human resources team, audit and compliance, etc.
If your company has existing security policies, start with reviewing them to determine company’s current stance on a given issue or technology. Talk to subject matter experts and review information material from the internet.
Next develop an initial draft. Review of right level of balance between rigidity and weakness for implementation. This ensures that the policy is clearly stated and enforced as per the best practices, while at the same time providing a mechanism for dealing with occasional exceptions without weakening the policy.
The Coca-Cola Rule: Replace the name of your organization with Coca-Cola in your Information Security policy. Read the policy again. If the same policy makes sense for Coca-Cola company, you probably need to rewrite the policy. Good policy is always organization specific. Mention why information security is important for your organization. Note: If you have written policy for Coca-Cola, consider above rule as Emirates Airline Rule.
Finally, review with different stakeholders for possible gaps. Such stakeholders include the technical, legal and internal audit departments. Ensure that all identified gaps are closed before publishing policy documents.
Policy documents should be published so that they are available to all employees. You may put them on the company intranet site, or any other suitable place. The documents should be easily accessible and available for download, printing, and saving.
The most important part of polices development and enforcement is to ensure that relevant employees are aware of them. While email can be an excellent way to inform all personnel about the policy documents, however, communications must not be limited to emails only.
An education and awareness development program needs to be designed and implemented. The purpose is to ensure that employees who are supposed to follow the policies understand the “value” of adhering to them. Patently, awareness, education and policy go hand in hand, each strengthening the other.
Newly developed policies and procedures must be given some grace time for compliance. Subsequently, grace period for compliance enhances the effectiveness of enforceability and helps in building employees’ confidence and trust. Depending on the size of the company, the grace period can be from a few weeks to few months. Thus, the internal audit department and Senior Management must be taken onboard to decide for the appropriate grace time.
Policies must be reviewed and updated on regular basis. Ultimately, the purpose is to ensure that the polices are not obsolete due to changing business practices or technology updates. Annual reviews can provide a good balance between agility and stability. However, if required, a need-basis review and update can be conducted after a major change in the business, environment or technology.
Common issues that hurts policy effectiveness
In this section, I will try to identify top three reasons which contribute in reducing the effectiveness of any policy document:
1. Lack of skills and experience while developing policy documents – Writing a policy document is easy if you want to end-up as a “shelfware”. The right skills and experience is required to engage stakeholders and develop policy that “clicks”.
2. Lack of proper education and awareness plan – No matter how well polices are written, they are of no use if the practitioners are not aware of the value of adhering them. Therefore, much efforts and time must be invested in developing and implementing an effective awareness program for all employees and stakeholders to digest.
3. Demonstrable commitment from all levels of management – All levels of management must demonstrate their commitment in adhering policies, especially because it is very different to follow them after their development. This cultivates confidence and trust among the employees.
PECB
The latest developments on the security world have been seriously shaping the way it is being proceeded with day-to-day business activities. Playing a vital role to the organization, information security and data protection should be incorporated to the firms policy of increasing customer satisfaction. At PECB, we are constantly increasing competence through our Information Security courses.



![David-Lannoy-Managing-the-success-of-Enterprise-Risk-Management-[KRIs]](https://insights.pecb.com/wp-content/uploads/2017/01/David-Lannoy-Managing-the-success-of-Enterprise-Risk-Management-KRIs-500x350.png)





