In order to be able to discuss the similarities and differences between the three frameworks, we need to understand the background of each one. There certainly are some similarities between all three but also wide areas of vast differences.
Firstly, we need to understand that ISO/IEC 27032 is really about implementing security rather than a security framework that must be adhered to ISO/IEC 27001 or CMMC. Thus, ISO/IEC 27032 is about being a cybersecurity manager that manages one or more cybersecurity frameworks such as ISO/IEC 27001, CMMC, or possibly both simultaneously. It goes into more of the administrative controls, such as creating policies that adhere to the security framework.
Generally, it could be viewed, that a certified ISO/IEC 27032 Lead Implementer would bring a company up to speed with a framework of some sort, and then an ISO/IEC 27032 Lead Manager would keep that framework alive and not allow security to start sliding backward. So, for example, ISO/IEC 27032 would indicate that the Confidentiality, Integrity, and Availability (CIA) triad must be followed but not mandate exactly how to follow it. That would be the job of a framework such as ISO/IEC 27001 or CMMC.
It is widely known that ISO/IEC 27032 and ISO/IEC 27001 are from the ISO family, while conversely CMMC is from the NIST family. The longer you work with the two families the more you realize they are cousins to each other with one (ISO/IEC 27001) being more internationally based and the other (CMMC) being more focused around the United States.
Foundational Material
As it relates to foundational material, it absolutely must be pointed out that ISO/IEC 27001 is a tried, proven, and seasoned framework with almost two decades of successful implementation. CMMC is in its infancy, relatively speaking, but rapidly making an impact in numerous areas.
As everyone is aware, ISO/IEC 27001 covers numerous areas of security and is designed to be fairly universal regardless of what line of business the company is in. However, CMMC is not designed as such and it does specifically target companies that support the US Department of Defense (DoD). Once we understand this, the differences between the two frameworks start becoming more apparent.
For example, ISO/IEC 27001 is a one-shot framework in which you either are compliant or not. CMMC is a framework that has maturity built into it. In other words, you may be CMMC Maturity Level 1 (ML1) compliant but not CMMC Maturity Level 3 (ML3) compliant. That is not to say that you cannot mature ISO/IEC 27001 but it takes a good ISO/IEC 27032 Lead Manager to understand the vision and need to do so.
To continue on this area of difference, any maturity target in relation to ISO/IEC 27001 is really up to the ISO/IEC 27032 Lead Manager whereas the maturity for CMMC is clearly defined.
Another area of difference is that there are no legal requirements to implement ISO/IEC 27001, so when it is implemented, it is to indicate to others that a company is secure while following an established standard. However, CMMC does have legal requirements attached to it, so essentially it boils down to the following: if you want to do business with the DoD then you will be CMMC compliant, and if you are not compliant while doing business with the DoD then you could be facing numerous federal sanctions.
As it relates to the fundamentals of the frameworks, there are numerous overlaps. Both require separation of duties, complex passwords, network segmentation, minimization, etc., all the basics that are in any framework from ISO/IEC 27001, HIPAA, PCI, FFIEC, and so on. However, in my experience, CMMC takes the concept of a security framework to the next level.

An area of CMMC that is not present within ISO/IEC 27001 is that CMMC is really a combination of NIST 800-171/FAR 52.204-21 and has multiple levels of data classification. While ISO/IEC 27001 may require data classification in a holistic sense there are no actually defined classification labels (that is up to the ISO/IEC 27032 Lead Implementer/ Manager to figure out) nor are there different levels of security based on the classification level. On the other hand, CMMC requires at least ML1 to handle or process Federal Contract Information (FCI) and ML 3 to handle Controlled Unclassified Information (CUI). It is important to point out that CUI is, essentially, directly below the classification level of SECRET according to the US Government, with an example of SECRET data being what was released to WikiLeaks by Chelsea Manning.
Evolution
Of course, ISO/IEC 27001 has evolved over time and will continue to do so. As the threat evolves, technology grows or improves as well. CMMC is no different when it comes to this. However, where ISO/IEC 27001 seems to take the lead is a much more methodical pace involving industry leaders and mentors across the globe to provide useful input to maturity. CMMC, on the other hand, does not seem to have that same methodical pace of maturity.
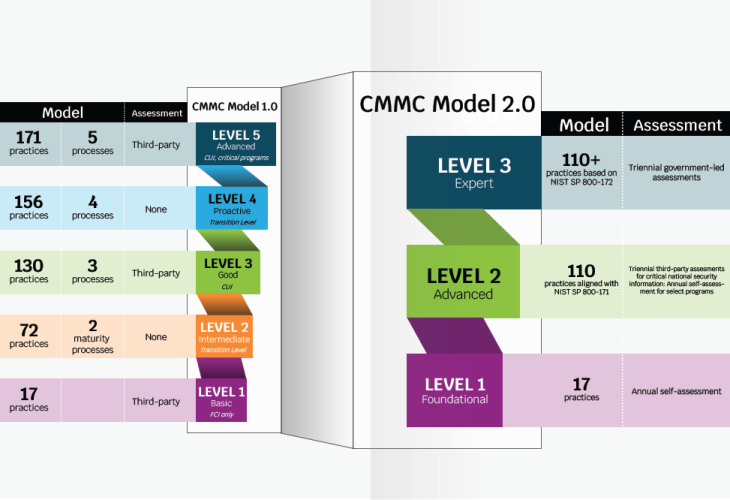
To begin with, CMMC started with version 1.0 (CMMCv1) with 5 maturity levels, with Maturity Level 2 and 4 designed to be transitionary before landing at either ML3 or 5. However, in November of 2021, CMMC matured to version 2.0 (CMMCv2) which had significant changes and still appears to have a high probability of further changes.
One obvious change was that v1 went from 5 maturity levels to 3 in v2. In a way, this makes sense, however, this also removes the ability for a company to demonstrate forward momentum on maturity until that company has already achieved it. An example of this evolution is demonstrated in the graphic.
Another area of change for CMMC was that an auditor was required to be onsite for v1 ML1 in comparison to a company self-attesting to ML1 in v2. A similarity with ISO/IEC 27001 is that there is no requirement for an auditor to be onsite for any part of the actual audit as everything could be done via zoom. However, for CMMC v2 ML2, an auditor must be on location to personally witness the company perform evidence tasks.
Another area of difference is that an ISO audit could be viewed as easier to deal with than a CMMC audit from the standpoint of the company getting audited.
An ISO audit generally requires one item of evidence to meet an audit area with possible expansion for sampling. Conversely, CMMC auditors are obligated to get at least two items of evidence for each audit area with one of those items being a one-on-one interview with a key person, who performs that task, to demonstrate or verbally explain in sufficient detail that the particular practice is well established within the company.
The CMMC auditor must ensure that the person performing the relevant task is doing so at an expert level. Granted, that is in addition to actual evidence that still must be collected. So, for example, an ISO/IEC 27001 auditor may ask for proof of data backup being performed, as well as follow-on proof of data restoration, with log files possibly being sufficient. A CMMC auditor will ask for the same and then require the administrator to demonstrate both processes just to see if the administrator acts confused through the process.
One similar area is the indirect management of CMMC. By simply being CMMC compliant and wanting to maintain that compliance, or by maturing into a higher level of compliance, meeting all the CMMC requirements would naturally align with the functions that an ISO/IEC 27032 Lead Manager would perform.
Pitfalls
There are some pitfalls that you need to be aware of as well, most relating to CMMC. Generally, once a company gets an ISO/IEC 27001 certificate, they are set for three years before needing a new audit. CMMC is the same, however, a company that holds any CMMC maturity level can be audited by the DoD or a Prime Contractor at any time to ensure continual compliance. This is to ensure companies do not do the work to become compliant but then slide backward after being awarded. Companies are specifically warned that spontaneous follow-on audits could happen at any time.
Where this comes becomes effective is when CMMC is attached to a federal law called the False Claims Act which has significant penalties attached to it. ISO/IEC 27001 does not have any sanctions attached to it, as becoming compliant is still essentially a voluntary action by a company. As an example of severity, in 2020 alone, the US Department of Justice recovered over $2.2 billion due to false claims by providing generous rewards for whistleblowers.
The CMMC audit process is also more complex when compared to ISO/IEC 27001, with multiple review stages required before being awarded a CMMC Maturity Level, during which, if at any review stage a reviewer does not think there is enough evidence, then the audit is denied until the issue is rectified.
Of course, this does not apply to v2 ML1 given it just requires an attestation and no actual auditor present.
Closing
In a general sense, ISO/IEC 27001 is a foundational framework for any company to implement with a consistent evolution based on solid input by seasoned professionals worldwide. However, CMMC is rapidly gaining traction in the Defense Space within the USA and will likely continue to evolve past v2 at some point based on the needs of the DoD.
Moving into a CMMC framework can be challenging however starting with an ISO/IEC 27001 framework before moving to CMMC can make that process much easier.
Lastly, having a solid ISO/IEC 27032 Lead Manager to blend CMMC into an existing ISO/IEC 27001 framework can easily reduce cost and headache if any company believes CMMC is in that company’s future.
PECB is approved as a Approved Publishing Partner (APP) from the Cybersecurity Maturity Model Certification Accreditation Body (CMMC-AB) for the Cybersecurity Maturity Model Certification standard (CMMC). For further details, please click here.









