Definition
Internet-of-Things (IoT) security integrates processes and tools that defend networks from cybersecurity threats. These threats continuously evolve and exploit IoT device’s vulnerabilities. Proactive threat analysis and risk mitigation strategies counteract these threats through policies, technology, and people. IoT networks are diverse, so a single strategy or industry standard will not apply to all networks.
Device (also called endpoints, nodes, or sensors) manufacturers design are not forced to comply with security standards, old devices with outdated technology are integrated into the IoT network, devices are placed outside a secure perimeter, different communication protocols, and ad-hoc reconfiguration increase IoT security complexity.
This article will summarize recent adoption trends, list common security threats, present underlying IoT vulnerabilities, recommend risk mitigation strategies, and present common security tools to strengthen the IoT security posture. Given the breadth of this article, references have been hyperlinked to aid further analysis.
Significance
IoT technology has catalyzed global digital transformation, identified in many reports as the greatest business driver. Corporations harness the technology to improve processes, develop new capabilities, quickly pivot to new markets, or compile data for strategy development. Smart cities, smart homes, telehealth, and industrial automation are applications driving this adoption. Consumers now rely on IoT to improve daily habits, automate home appliances, and for entertainment. Technology adoption has accelerated despite supply chain disruptions, a global semiconductor shortage, and the COVID-19 pandemic. Technology catalysts include decentralized processing capability, cloud computing, cheap hardware, wireless spectrum access, and scalability.
Despite the explosive growth, IoT security has not kept pace with technology adoption. The devices themselves pose many security risks: poor password management, software is not properly updated, and many devices lack security features. Users also do not adopt best security practices since they are not held accountable, nor do they properly understand the risk or how to manage security. Effectively, network security is as strong as its weakest link.
Therefore, hackers view IoT as the bridge into the enterprise network. For example, a Las Vegas casino’s network was compromised through an unprotected aquarium temperature sensor, this sensor was part of a third-party system design that was not reviewed for cyber readiness and actively managed by the Information Technology (IT) team.
Hackers who are motivated by financial gain, revenge, or politics, can cause significant damage once they access the network. Users can experience injury, death, financial loss, damaged reputation, corrupted data, data theft, data loss, and service disruption. Corporations must protect personal data including credit card info and Personally Identifiable Information (PII).
Once compromised, corporations must reach out to their customers and remedy the breach. Recently, hackers have targeted medical IoT during the COVID-19 pandemic to compromise data or disrupt medical devices, such as insulin pumps. Ethical hackers, in an exercise to demonstrate a connected car’s vulnerability, were able to access the car’s network and remotely control the brakes, the car’s acceleration, and door locks.

Threats
In addition to the short-term damages mentioned above, hackers can cause long-term damage once they access the network. The following threats have been repeatedly identified.
Malware is a type of attack that occurs when software is installed on a network device. The malware could take the form of a worm or virus that potentially infects other network components and servers. Malware can be used to deny access to critical components, gather sensitive data, or corrupt system automation. If a hacker can access an IoT endpoint, the malware will be installed on that sensor. Historically, malware was distributed through e-mail attachments that required unsuspecting people to open them. Botnets are distributed malware used across an endpoint array to disrupt a portion of the network.
Botnets are typically used for denial of service (DoS) attacks or transfer enterprise command and control to the hacker. The hacker will install the malware on one node, which then infects other nodes with the malware. Removing this distributed attack will require remediating each infected node.
Ransomware is a type of malware that will lock out system users and administrators until a payment (ransom) is made. Command and control could also be transferred to the hacker and increase the urgency and motivate immediate payment. An example is the compromised vehicle where the hacker will control a compromised vehicle until the payment is sent. The Baltimore City government and Atlanta City governments were affected by this type of attack between 2018 and 2019.
The following two threats are exclusive to sensors and hardware located outside the security perimeter (also identified as defense-in-depth).
Physical theft is the removal of the endpoint or infrastructure from its location. Most likely the network will not be accessed through the stolen node, but service continuity is at risk if it is used to relay data from other endpoints or commands from the enterprise.
Reverse engineering techniques will examine the stolen hardware to replicate the node design. The design can be manufactured and integrated into the network to collect network data or distribute malware across the network.

Issues
Analysts report that IoT adaptation has exceeded growth expectations. However, IoT security has lagged the accelerated technology deployment; many systems are deployed without any cyber readiness or vulnerability assessment. The underlying concern is an exponentially growing vulnerability gap that also has exceeded projections.
Common causes leading to the gap are designs, sensor security limitations, asset management, corporate policies and procedures, and education.
Rapid adoption also requires technical talent capable of managing enterprise assets. However, the necessary talent pool size is also not growing proportionally. As stated by an ISC2 report, analysts estimate a global 2.7 million cybersecurity professional shortage in 2021.
Skills critical to maintaining the security posture include hands-on experience with tools, technical writing, system design, data analysis, and technology lifecycle management. Traditionally, cybersecurity professionals started in information technology (IT) and transitioned into cybersecurity. However, Generation Z and Millennials have completed self-paced or university education to enter the profession but lack technical acumen. Finally, analysts show that cyber professionals are predominantly male (76%) and Caucasian (72%) in the United States and the United Kingdom. These three trends quantify severe limitations with current hiring strategies.
Budgets are also not keeping pace with accelerated IoT adoption. An executive survey reports IoT cybersecurity spending will not increase year over year (YoY). Budgets limit staffing, tool acquisition, training, corporate culture, and risk management capabilities. Recent inflation further limits budget and spending impact. Executives also need to identify critical vulnerabilities that pose the greatest corporate threat and dedicate resources to mitigate risk.
IoT nodes can range from simple sensors that digitize and transmit data to complex command and control systems. Endpoint design standards do not exist and designs range in processing capabilities, local storage, firmware, communication protocols, and memory. Unfortunately, security features are not a design requirement and it is the responsibility of the system designer to implement security controls. Many manufacturers also do not update software nor release patches to mitigate discovered vulnerabilities. Nodes with patches and new software have finite processing power, memory, and storage that limit data collection or processing while upgrading software.
In many IoT systems, IoT nodes are located outside security perimeter and communicate via unregulated wireless channels in the Industrial, Scientific, and Medical (ISM) bands. Wireless transceivers in these bands are commercially available and access barriers do not exist. Hackers actively exploit the vulnerabilities through the wireless channels to penetrate the network.
Consumer IoT adoption is also a developing vulnerability. Employees link their wearables (such as biometric trackers) and virtual assistants to both public, home, and enterprise wireless networks. Consumers are predominantly ignorant about cybersecurity and poorly managed risk. Wearable manufacturers rarely design security features nor update operating software to patch vulnerabilities. Since personal devices are not corporate assets, they rarely adhere to enterprise compliance and risk mitigation standards.
According to ArchonSecure, recently, many older endpoints have been integrated into IoT networks. This practice is common in manufacturing facilities that do want to disrupt optimized industrial processes. These nodes are no longer supported by the manufacturers and operate on antiquated firmware that predate basic security features. In many corporations, the assets are not managed by the enterprise IT team but are managed by industrial engineers or facilities maintenance. Many sensors operate on outdated communication protocols, such as RS-232, that are not compliant with internet based schemas, such as Transmission Control Protocol (TCP) or User Datagram Protocol (UDP).
To effectively communicate with the corporate network, these sensors are connected to aggregators which translate data and commands from multiple sensors between the native protocol and the network. This strategy increases network vulnerability because these sensors do not have an IP address and are isolated from asset and configuration management tools. This isolation compromises asset management since the legacy sensors are often not properly cataloged, managed, and decommissioned when the system is permanently removed from service.
Executives have identified broader IoT asset management as a vulnerability. In addition to the deficiencies mentioned above, new designs and capabilities are not properly reported to the Enterprise IT staff nor the cyber team.
The endpoint vulnerabilities are not properly analyzed and risk mitigation strategies are not developed and implemented. The endpoints’ risk profile also increases as critical software updates and security patches do not propagate to the network edge.
In the event the network breach is caused by an unknown sensor, forensic analysis, and an incident management remediation plan will be unable to quickly quarantine the affected sensor and mitigate damage.
Corporations adopting IoT typically lack system design expertise and outsource the project to engineering firms. One common mistake is omitting a cyber professional’s design assessment of its cyber readiness. Cyber professionals can also advise on asset management, event management, and cyber awareness training. Unfortunately, cyber specialists are in high demand, and adding them to the design team significantly increases project costs. Finally, policies to assess cyber readiness continuously through audits are not implemented to improve the security posture.
Recent surveys have also reported password management is a significant IoT vulnerability. In many sensors, passwords are never implemented nor changed from the default one set by the manufacturer. Because many sensors are not managed by the IT, corporate policies for password complexity and periodic password changes are never enforced. As a result, generic or default passwords are easily deciphered.
Business leaders are also concerned with the lack of cyber awareness and accountability. Trending vulnerabilities are not disseminated to employees. Also, employees’ cyber awareness is not audited, and refresher training is rarely presented. Employees also develop risky habits, for example, people who telework may travel overseas and work from unsecured locations with public WiFi.
In addition, employees should be held accountable for IT assets issued to them, such as corporate keycards or laptops. Poor management, for example, such as leaving assets unsecured in a public space, is a significant risk, since they can be lost or stolen. Unfortunately, many security concerns remain unreported and violators are not held accountable. This behavior empowers irresponsibility.
With the recent COVID-19 pandemic, business operations have transitioned from offices to homes. Cyber risk has also increased with employees using corporate assets on home networks with unsecured IoT controls and sensors. Since corporate IT does not have the capability to manage employees’ home devices, they cannot quarantine, upgrade, or segment them.
The vulnerabilities listed in this article represent trending security concerns. As technology evolves, new threats will emerge. The optimal cybersecurity strategy is to continuously analyze potential threats and apply best practices to mitigate the risk and the potential impact.

Defenses
Countermeasures to mitigate the risks listed above involve processes, people, and tools (e.g. technology). Processes define the expectations and the sequences implemented to improve the security posture. People need to be trained to follow processes and management’s expectations. Tools aid people with event detection, enforce policies and evaluate cyber readiness.
A cyber champion or evangelist is needed in many organizations to improve their security posture. This person should be the face of cybersecurity within the organization. Key messaging disseminated throughout the organization should highlight potential improvements to mitigate security gaps, success metrics, any recent security events, and any lessons learned. From an IoT perspective, the evangelist should focus on implementing a strong cyber awareness that is reflected in the system lifecycle, cyber readiness evaluation, event management, and training programs.
A cyber evangelist’s most ambitious goal should be a cyber-aware corporate culture throughout the organization, including clerical and hourly staff. In addition to training programs and information sharing, evangelists can recommend rewards for cyber adoption, incorporate cyber practices into performance reviews, identify performance gaps, and recommend improvement plans.
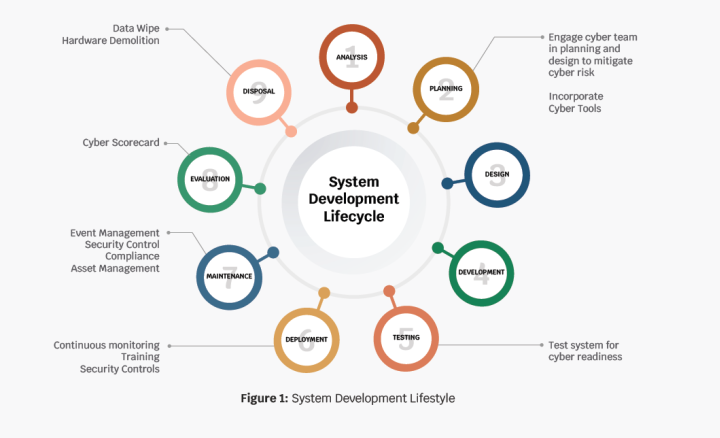
Businesses typically lack the system design expertise and outsource projects to engineering firms. One common mistake is omitting a cyber readiness design assessment. Implementing cybersecurity best practices into a system lifecycle is shown in Figure 1. A system lifecycle is a standard framework that describes the event sequence from the initial strategy through system obsolescence. Key cybersecurity contributions are highlighted through the system lifecycle. During the design phase, security tools are integrated into the system design.
The tools consist of both hardware and software platforms that strengthen the system’s security posture. After the prototype has been implemented and is ready for a pilot phase, cyber tools scan the infrastructure, for both, vulnerabilities and best security practice compliance. These security gaps must be remedied before the system is activated for use.
Event management is a critical gap in cybersecurity. When a data breach or virus infection occurs, key players must react to isolate the affected areas, remedy the vulnerability, collect lessons learned, and recommend strategies to mitigate future risks.
To prepare for events, roles and responsibilities must be clearly defined and processes must be planned and broadcast to the key players. Periodic simulations or rehearsals with key players help refine event sequences, identify dependencies, and address any discovered gaps.
Asset management has been identified as a key defense against cyber risk. IT personnel must track the IoT assets throughout the lifecycle and manage software updates, configuration changes, repairs, and decommission.
If properly managed, the sensors can be properly retired when they are no longer useful. The assets must also have their memory wiped and hardware must be demolished so data is not compromised nor can the hardware be repurposed or re-engineered to enable unauthorized network access.
Virtual Private Networks (VPN) can mitigate the risk incurred by employees’ use of personal home networks. VPNs establish a secure and encrypted internet connection between the workstation and the corporate network.
Unfortunately, the VPN’s security is as robust as the device accessing it. If an employee is using their personal device on the VPN, then any viruses or malware installed on it can migrate to the corporate network. The best practice with teleworking employees is to distribute laptops with enterprise antivirus software and other security tools.
The partitioning of vulnerable sensors into Virtual Local Area Networks (VLANs) (also known as network segmentation) is important to mention at this point.
VLANs partition the network and will restrict traffic from the vulnerable sensors into the enterprise. VLANs can also quarantine compromised devices from the network itself. Firewalls and firewall rules can be implemented between VLANs to enhance security between different network subnets.
The growth of personal IoT devices used on enterprise networks has increased network vulnerability. The best risk mitigation strategy is to deploy an unsecured wireless network firewalled from the corporate network. A policy mandating these personal assets connect to this network needs to be released and enforced. Tools, such as Network Access Control (NAC) can be used to enforce these policies.
2-Factor Authentication (2FA), also loosely referred to as Multifactor Authentication, enhances Access Management by adding another access variable to strengthen the enterprise network’s access portal. The three main types of authentication are:
- “What I possess?” – Examples include a cell phone to receive SMS messaging, an e-mail to receive a temporary password, or a key card
- “What I know?” – Ranges from username and password through security questions that pertain to you
- “Who am I?” – Such as a fingerprint or facial recognition
2FA protects against asset theft or password compromise. In terms of network access via the IoT endpoints, the first two options (What I possess and What I know) are implemented.

Tools
Scanning tools audit both hardware and software. Compliance scanners are software tools that audit the network and notify administrators of devices that do not operate on recommended software versions or have not been properly patched.
Scanning can occur daily, weekly, or monthly. Once non-compliant systems are detected, the administrators must update the software and patches to maintain compliance. Vulnerability scanners are software tools used to detect misconfigurations, nonconformance to cybersecurity best practices, and other risks in network components including IoT nodes. Scans can be configured to recommend mitigation strategies for reported vulnerabilities.
Network access control (NAC) incorporates Access Control Lists (ACLs) to grant entry into the network. Devices not existing in the ACL will either be quarantined or redirected to a VLAN. NAC can also be configured to restrict compromised devices from accessing the network.
NAC also replaces port security, where a specific network port goes to a specific network device. This capability eliminates device replication.
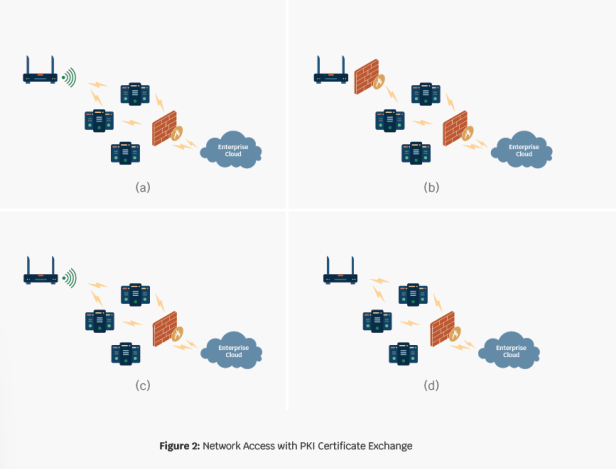
IoT networks are dynamically scalable and use Certificate Authority to manage the public key Infrastructure (PKI) for the network. The CA releases certificates to trusted devices. When a device comes online and starts communicating, it shares its credentials with the enterprise. If the enterprise recognizes its credentials, the device is integrated into the network. If the credentials are not recognized, it is not allowed to join the network.
Figure 2 shows this interaction. Figure 2 (a) and (b), demonstrate a wireless device whose credentials are not recognized and are firewalled from the network. In Figure 2 (c) and (d), the enterprise network recognizes the certificate and allows the device to join the network. PKI can also be used to encrypt the data through key use, further hardening the sensor network.
An Intrusion Detection System (IDS) actively monitors the wireless network access and reports anomalous behavior.
Intrusion Detection Systems can also be configured to alert administrators when black-listed devices try to communicate with the network. IDS can also be configured to alert users of anomalous traffic, such as a device repeatedly trying to access one device or cycling through a string of network addresses. IDS is a monitoring tool and is not used to actively manage the network.
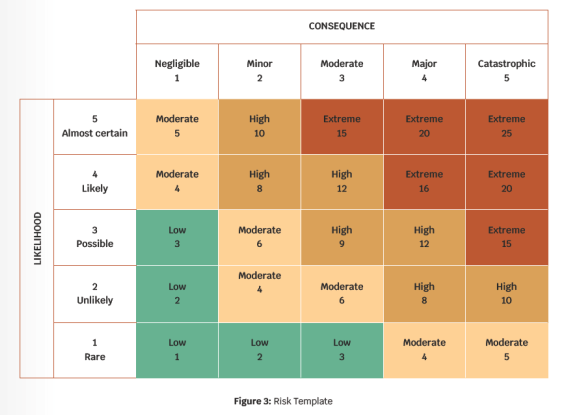
Many sensors are placed outside the organization’s secure perimeter and are not protected by fencing, access controls, and guards. These endpoints are not protected from theft or damage. To mitigate risk, designers can explore placement in inaccessible locations to limit occurrence probability and the potential damage. Figure 3 shows a generic risk template.
The cells in the matrix are also color-coded to highlight criticality. Each risk is scored on a scale of 1 to 5 on its occurrence and impact respectively. Red-colored cells identify risks with the greatest probability and impact physical access. Designers can also house the nodes in weather-resistant enclosures with locks. The enclosures can be designed to include an alarm trigger that notifies staff when a node is accessed or damaged. The design tradeoff is cost and accessibility to service the nodes.
Risk matrices can help identify which vulnerabilities are most likely to cause significant damage and drive cybersecurity budgets.
A risk matrix is a high-level analysis tool organizations use to identify key areas that require the most resources.
The matrix compares different risks in terms of the that require immediate attention while green-colored cells have minimal impact or probability and can be passively monitored.
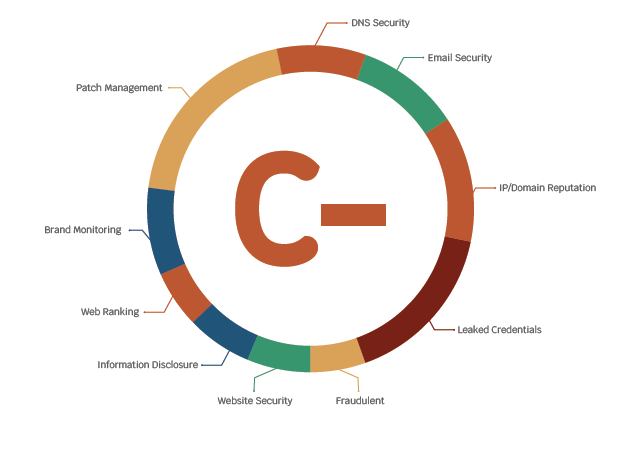
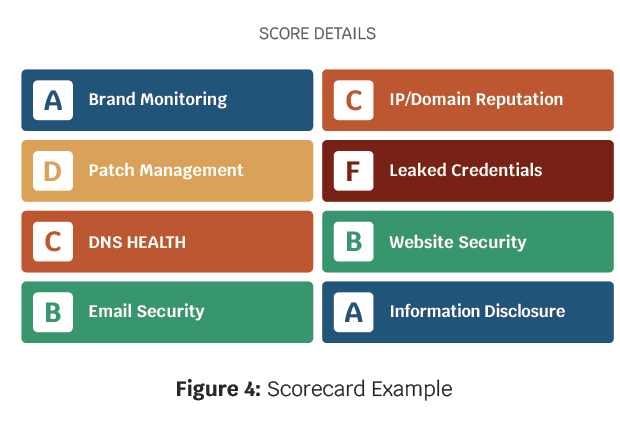
A generic scorecard is a dashboard used to continuously assess cybersecurity training, policies, and infrastructure. A scorecard should be simple and easy to read, however, the top quadrant is an evaluation of how the company’s cyber posture compares to its competitors.
This scorecard is just an example, but the key data points are the overall score, the score breakdown to the individual metrics, such as patch management, the score weighting, and the trending score over the past year. Other data points not presented in this scorecard are key security events, such as a data breach or bullets describing deficiencies. A generic scorecard template can be downloaded or a custom scorecard highlighting key metrics can be designed in a spreadsheet tool.
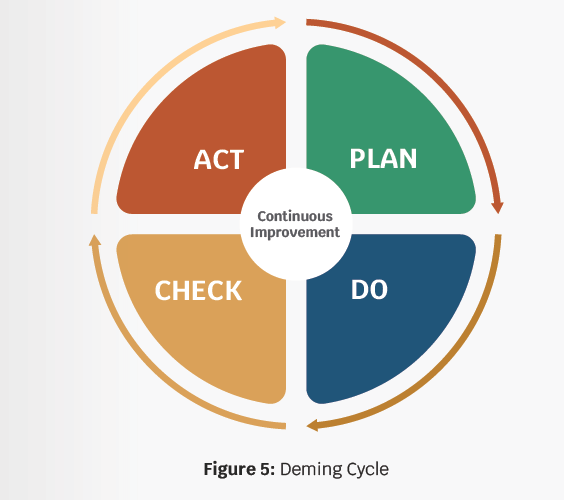
Finally, organizations must complete periodic reevaluation and audits should be implemented to identify developing vulnerabilities. Remediation plans are then evaluated and implemented to mitigate risk. The Deming Cycle (Plan-Do-Check-Act), shown in Figure 5, is a management framework used to assess cyber readiness continuously and implement corrective action.
During the Plan stage, multiple strategies are evaluated for cost, complexity, and potential efficacy. The success criteria is also planned during this phase as is the fallback plan in the event the strategy is not successfully implemented.
The best strategy is selected and the implementation team plans the roll-out. The implementation team then integrates the strategy during the Do phase. During the Check phase, the implementation is evaluated against its key success factors, and lessons learned are also discussed. Finally, in the Act phase, the next improvement is selected based on the success and lessons learned. The Deming Cycle is repeated as the iteration is planned, implemented, and evaluated.
Conclusion
IoT technology represents transformational opportunities for many businesses. The benefits include; data mining, new business opportunities, and reduced cost. However, IoT is a growing vulnerability within enterprise networks. Many factors, such as training, oversight, and system design, contribute to this vulnerability.

Fortunately, there are many tools and strategies that can mitigate this risk. Organizations must determine what their greatest risk is, develop a strategy to mitigate it, assess the strategy’s efficacy, and improve the strategy.









