At any point in time, any organization can face Information Security or Cybersecurity incidents1. Without having a risk management process supported by an effective and well-documented method in place, organizations will struggle when facing incidents that seriously threaten their sustainability and overall success. It is the top management’s responsibility to structure the organization properly, so that it can effectively cope with potential risks.
Risk is defined as the probability of an incident occurring that can impact the organization and its components in a form that is undesirable and unpredicted.
By focusing on detecting what might go wrong, the risk management process helps to identify risks that could potentially affect the organization. Evaluating risks in terms of probability and impact allows the organization to rank them in order of importance, and deal with them in accordance with their priority. By identifying risks, organizations will be better prepared; will reflect on potential threats beforehand, and may even be able to consider the cost-effectivity of different forms of addressing risk.
It is incorrect to presume that only large organizations need to manage risk. The size of the organization is not a factor when it comes to dealing with risk; all organizations are responsible for ensuring the availability, integrity, and confidentiality of the assets entrusted to them by their clients. Therefore, the need to take into account the organizational framework and the competences of the human resources involved in technology management and Information Security management becomes apparent.
Implementing a risk management process in an organization comes with challenges and pitfalls. Firstly, there is the technological aspect of the organization. Different factors, such as the nature of the information systems in place, the amount of data, the novelty of applications, the transactional exchanges, and the emerging technologies, require the IT specialists to make sure everything works correctly (infrastructures, networks and services, etc.).
Yet, Information Security will be seen in many ways as an irritating factor, and technology managers may try to minimize security because, according to them, security affects performance, is expensive, and requires controls that restrict access. It is, therefore, imperative to separate the branch of Information Security and Risk Management from Information Technology (IT). Ideally, the management of security should be the responsibility of the general management or, even better, it should be under the direct authority of the top management.
Security and Cybersecurity are therefore not just IT issues. On the contrary, they are multifaceted challenges that require an integrated management approach. Total protection against threats and cyber-threats is impossible. The concept of zero risk is non-existent here. We can, nevertheless, create a risk-based approach that features a broad strategy to deliberately avoid, mitigate, accept, or transfer the risks posed by these threats.
Organizations must establish and maintain an appropriate governance and risk management framework to detect and eliminate risks to communication networks and services.
In this context, an effective security (including Cybersecurity) program based on risk management requires a governance framework that uses processes, methods, and tools wisely to manage risk properly.
A Governance Framework
The first step for the management team is to identify the persons within the organization that need to be involved in the development of a security program. Among the key internal measures to be taken initially is the identification of known risks and established controls.
It is best practice to set up an Information Security Management Committee that consists of managers representing the full range of knowledge and skills of the organization.
Another best practice is to appoint a Chief Information Security Officer (CISO) and assign him/her to the function of overseeing the organization’s initiatives in the area of security. Nevertheless, the appointment of a person for this duty does not release the rest of the organization – including the senior management, staff, consultants, partners, and clients – from their share of responsibility regarding security management. Security is everyone’s responsibility.
A Risk Management Process
As organizations face a considerable number of risks, risk management must be a central part of any organization’s strategy. Such strategic management helps in identifying and addressing the risks faced and, in doing so, increases the likelihood of successfully meeting business objectives.
A risk management process based on good practices will:
-
Help the management team to take decisions when selecting the risks to prioritize and plan the controls to be deployed
-
Facilitate the allocation of capital and resources
-
Help anticipate possible scenarios, minimize the number of incidents and their impacts or, in the worst-case scenario, avoid a disaster or a serious financial loss
-
Strengthen relationships with partners, clients, and various third parties
-
Enlighten leaders in their strategic choices
-
Improve brand image vis-à-vis the market
-
Build employee confidence in the effective management of the organization
The figure below summarizes the process recommended by ISO/IEC 27005 and includes 6 major steps.
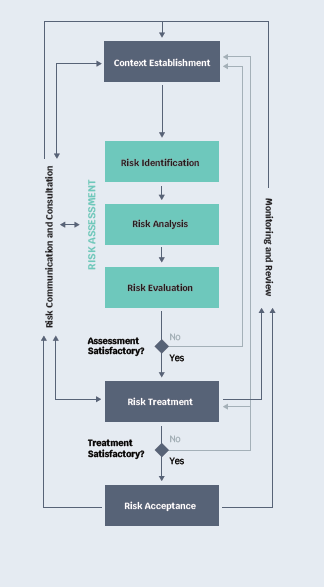
- Context establishment aims at globally identifying the information assets (data, information systems, network, etc.) that will be evaluated and located in the internal and external environment.
- Risk assessment makes it possible to identify the risk sources, to estimate the risks, and to assess the importance of risks in terms of their severity.
- Risk treatment allows the selection and implementation of risk-modifying controls (accepting, mitigating, transferring, or avoiding risk).
- Risk acceptance confirms the top management’s decision to accept risk.
- Risk communication and consultation ensures transparency between the organization and its stakeholders.
- Monitoring and review ensure that the process is continuously improved and generates the desired outcomes.

The implementation of this process will allow:
- The methodical identification of the risks associated with the organization’s activities
- The assessment of the probability of an event occurring
- The knowledge on how to respond to these events
- The strategies to deal with the consequences of such events
- The monitoring of the effectiveness of risk management approaches and controls
A Risk Management Methodology Carried Out by Experienced People
The worst risk is the one you do not know about
Didier Hallépée
In terms of skills, it is important to have experienced staff in risk analysis. The use of a novice advisor may seem economical at first glance, but may become a bad investment if he/she fails to identify and analyze the risks properly. At this stage, it is best practice to delegate the task of carrying out the risk analysis to a risk management-certified specialist.
Managing risk without using a recognized method2 will not generate the expected benefits to the organization. Using a proven method will allow you to identify the risks, vulnerabilities, likelihood, impact, and nature of the scenario describing how the asset is affected.
The use of a risk map will enable you to visualize risks in relation to each other, judge their extent, and plan the types of controls (organizational, technical, administrative, or legal) that must be implemented to treat them.
Risk prioritization, regardless of how it is done, makes it possible to allocate the right amount of time and financial resources to cope with high magnitude risks. One can put systems and controls in place to deal with the consequences of an event. This could involve defining a decision-making process, as well as escalation procedures an organization should follow if an event occurs.

Risk management requires discipline and great cohesion. For most activities, one needs to structure the approach and identify the carriers.
The implementation of important security processes is essential to support risk management, and we must not reduce the efforts to maintain a proper documentation if we want to improve the quality of the measures, the robustness of the infrastructures, the maturity, and the conformity of the organization.
The four main pillars of Information Security that support the entire risk management structure are:
- An information security policy
- Categorization of information assets
- A risk analysis describing the environment facing the organization
- An applied Information Security incident management process
These four pillars support a mature management of risk, effective identity and access management, effective technology management, a tested business continuity management process, and an effective and continual education and awareness program.
The combination of all these elements will allow the measurement of an organization’s exposure to information security risks. Some of the risks that can be faced include:
- Risks from mobile devices
- Human resources to recruit
- Problems in relationships with third parties (suppliers)
- Various risks associated with off-site work
- Technology risks, such as: risk of loss, damage, theft, or misappropriation of assets; risk of unauthorized access; risk of business disruption
The list can also include emerging risks such as cloud computing, the Internet of Things, artificial intelligence, metadata, etc.
A risk-based approach will help in better defining investments, and providing a more complete picture of the way things are done. It is not wise to take a chance with risks.









